Who is Really Behind the Ukrainian Brute Force Attacks?
This entry was posted in General Security, Research, Wordfence, WordPress Security on December 19, 2016 by mark 11 Replies
Last Friday we published a report showing a significant increase in Brute Force Attacks. We showed that most of the attacks are originating in Ukraine and we shared the most active IP addresses with you.
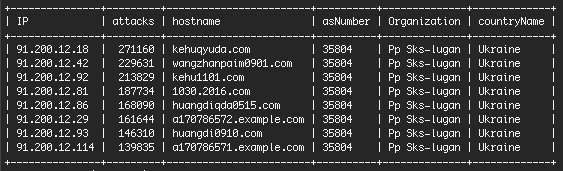
I have chatted via Skype and email with a source in Kiev, Victor P, who sent me some additional info. The company that owns the malicious IP block is “SKS-Lugan”. They are based in Alchevs’k in eastern Ukraine. According to a business guide Victor sent me, they have 16 employees and their CEO is Lizenko Dmitro Igorovich.
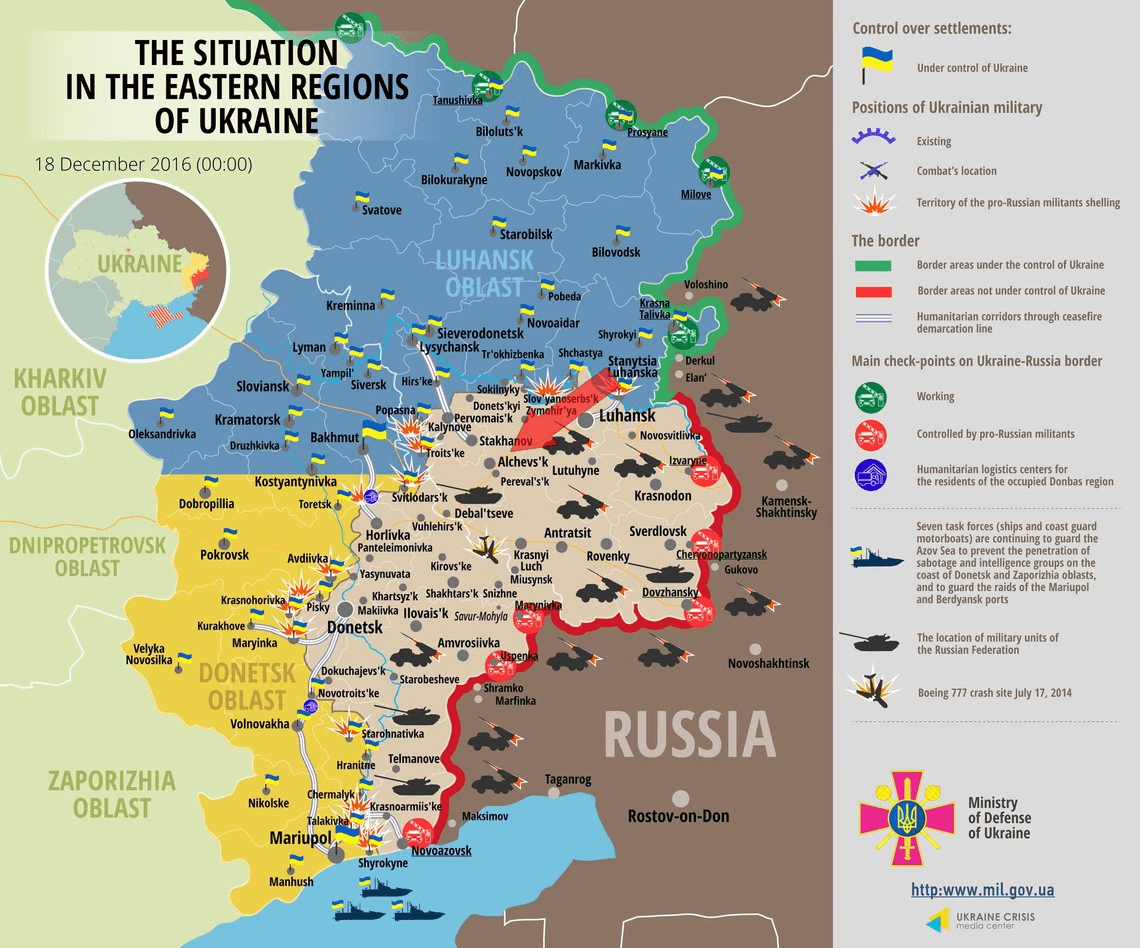
The eastern part of Ukraine is currently occupied by Russia. The map below, dated December 18th (yesterday), is from the Ukrainian Ministry of Defense. It shows which territories within Eastern Ukraine are currently occupied by Russia.
I’ve marked the location of Alchevs’k on the map with a red arrow. Victor is familiar with the reputation of the attacking IP block. He says that the company is being controlled by Russia and is being used to launch cyber attacks globally.
“Gabriele”, one of our readers, pointed out in the comments on our earlier post that the full IP block is 91.200.12.0/22. If you aren’t familiar with CIDR notation, that is an IP block that starts at 91.200.12.0 and ends at 91.200.15.255. It contains 1024 addresses (1022 usable addresses).
The network block is known for “Spammer & cybercriminal hosting”. The range of activities that are listed for this IP block are:
- Botnet controller
- Spam email leading to domains hosted on this block
- Spammer hosting
- Citadel botnet controller
- Neurevt botnet controller
- Smoke Loader botnet controller
- Locky botnet controller
- Canadian Pharmacy Botnet spam
- Tinba bonet controller
- Carding fraud site
- Madness botnet controller
- FindPOS botnet controller
- Pony bonet controller
- DDoS botnet controller
- Forum/Comment spam source
- Vawtrack botnet controller
- Necurs botnet controller
- Russian botnet drug spammer server
- Andromeda botnet controller
- Cutwail botnet controller
- KINS botnet controller
- Vawtrak botnet controller
Those are just some of the spam and botnet activities logged from this network. The list is long.
Russia has staged a military intervention in Ukraine that started in 2014. It wasn’t until December 2015 when Putin first admitted that Russian military intelligence officers were operating in the country.
In cyber security, attributing attacks to an individual or state is very difficult, sometimes impossible. Attackers on the Internet can route their traffic through as many servers in as many countries as they like before they reach their target.
The Russian intervention in Ukraine makes attribution of attacks even more complex. Using a Ukrainian Internet service provider gives Russia the ability to launch attacks globally with plausible deniability.
It makes sense that disputed areas like eastern Ukraine and Syria are a hotbed of malicious activity because they provide attackers with means, motive and opportunity. Occupying forces have the means to launch their attacks by using local ISP’s. They have several motives: They want to benefit from the attack itself and also discredit local businesses or government. And they have plenty of opportunity as these regions are usually occupied for years.
What to do about these attacks
Wordfence blocks these attacks by default. It will handle any brute force attacks and our firewall does a great job of blocking more sophisticated attacks. The free version of Wordfence receives our ‘community’ firewall and scan rules which are 30 days old. The Premium version of Wordfence receives real-time updates, so if we release a new rule for the firewall or malware scan, you receive it in real-time.
To combat these attacks, we recommend you simply install the free version of Wordfence if you haven’t already. Wordfence will lock down your site and protect your investment against these attacks.
Mark Maunder – Wordfence Founder/CEO.
Feedback: As always please share your thoughts in the comments below. I will be around to reply. If you would like to send a tip or data related to this story, you can email us at feedback@wordfence.com.
Thanks to Matt Rusnak and Kerry Boyte for their assistance editing this post.
This entry was posted in General Security, Research, Wordfence, WordPress Security on December 19, 2016 by mark 11 Replies
Last Friday we published a report showing a significant increase in Brute Force Attacks. We showed that most of the attacks are originating in Ukraine and we shared the most active IP addresses with you.

I have chatted via Skype and email with a source in Kiev, Victor P, who sent me some additional info. The company that owns the malicious IP block is “SKS-Lugan”. They are based in Alchevs’k in eastern Ukraine. According to a business guide Victor sent me, they have 16 employees and their CEO is Lizenko Dmitro Igorovich.
The eastern part of Ukraine is currently occupied by Russia. The map below, dated December 18th (yesterday), is from the Ukrainian Ministry of Defense. It shows which territories within Eastern Ukraine are currently occupied by Russia.
I’ve marked the location of Alchevs’k on the map with a red arrow. Victor is familiar with the reputation of the attacking IP block. He says that the company is being controlled by Russia and is being used to launch cyber attacks globally.
“Gabriele”, one of our readers, pointed out in the comments on our earlier post that the full IP block is 91.200.12.0/22. If you aren’t familiar with CIDR notation, that is an IP block that starts at 91.200.12.0 and ends at 91.200.15.255. It contains 1024 addresses (1022 usable addresses).
The network block is known for “Spammer & cybercriminal hosting”. The range of activities that are listed for this IP block are:
- Botnet controller
- Spam email leading to domains hosted on this block
- Spammer hosting
- Citadel botnet controller
- Neurevt botnet controller
- Smoke Loader botnet controller
- Locky botnet controller
- Canadian Pharmacy Botnet spam
- Tinba bonet controller
- Carding fraud site
- Madness botnet controller
- FindPOS botnet controller
- Pony bonet controller
- DDoS botnet controller
- Forum/Comment spam source
- Vawtrack botnet controller
- Necurs botnet controller
- Russian botnet drug spammer server
- Andromeda botnet controller
- Cutwail botnet controller
- KINS botnet controller
- Vawtrak botnet controller
Those are just some of the spam and botnet activities logged from this network. The list is long.
Russia has staged a military intervention in Ukraine that started in 2014. It wasn’t until December 2015 when Putin first admitted that Russian military intelligence officers were operating in the country.
In cyber security, attributing attacks to an individual or state is very difficult, sometimes impossible. Attackers on the Internet can route their traffic through as many servers in as many countries as they like before they reach their target.
The Russian intervention in Ukraine makes attribution of attacks even more complex. Using a Ukrainian Internet service provider gives Russia the ability to launch attacks globally with plausible deniability.
It makes sense that disputed areas like eastern Ukraine and Syria are a hotbed of malicious activity because they provide attackers with means, motive and opportunity. Occupying forces have the means to launch their attacks by using local ISP’s. They have several motives: They want to benefit from the attack itself and also discredit local businesses or government. And they have plenty of opportunity as these regions are usually occupied for years.
What to do about these attacks
Wordfence blocks these attacks by default. It will handle any brute force attacks and our firewall does a great job of blocking more sophisticated attacks. The free version of Wordfence receives our ‘community’ firewall and scan rules which are 30 days old. The Premium version of Wordfence receives real-time updates, so if we release a new rule for the firewall or malware scan, you receive it in real-time.
To combat these attacks, we recommend you simply install the free version of Wordfence if you haven’t already. Wordfence will lock down your site and protect your investment against these attacks.
Mark Maunder – Wordfence Founder/CEO.
Feedback: As always please share your thoughts in the comments below. I will be around to reply. If you would like to send a tip or data related to this story, you can email us at feedback@wordfence.com.
Thanks to Matt Rusnak and Kerry Boyte for their assistance editing this post.