DOWNLOAD THE PDF OF THE WHOLE DRAFT INVESTIGATION DOCUMENT: Click this link:
POLITICAL PAYBACK TACTICS USED
DID VC FIRM KLIENER PERKINS, OR OTHER VC’S, PUT SABOTEURS INSIDE OF THEIR ENEMIES, OR COMPETITORS COMPANIES, WORKING WITH ELECTED OFFICIALS?
A number of start up companies have reported that former Kliener Perkins staff had penetrated their companies under the pretext of “helping them” only to, later be found to be sabotaging those very companies, using CIA-recommended internal manipulation techniques. A consultant named “Bruce” and another named “Robert”, who used to work with John Doerr’s Kleiner Perkins, are under investigation for such suspected acts. Kleiner is deeply in bed with the CIA’s In-Q-Tel and uses them for public policy manipulation.
Declassified CIA documents detail how to sabotage employers, annoy bosses
The previously secret guide might make you wonder whether your annoying colleagues are actually spies
Your annoying colleagues might actually be CIA spies, according to recently-released documents from the US agency.
A previously secret document titled “Simple Sabotage Field Manual: Strategic Services” details the various ways that spies should work to bring down companies that they are placed in. But the sabotage techniques sound very similar to those encountered in many offices today.
The document was published in January 1944, as a way of showing spies and concerned citizens how they could work to bring down the productivity of important Axis workplaces during the war.
Read moreModern art was CIA ‘weapon’
It was produced to detail the “simple acts which the ordinary individual citizen-saboteur can perform”, allowing citizens to do damage to countries and companies using normal kit and “in such a way as to involve a minimum danger of injury, detection and reprisal”.
Some of the document’s suggestions are difficult to carry out and involve work. But others just read like simple tips for avoiding having to do too much at work.
Those include suggestions that saboteurs should hold meetings during important times, and to be a jobsworth by “apply[ing] all regulations to the last letter”.
As well as means for being bad at their jobs, the CIA offers instructions to “Act stupid” and “Be as irritable and quarrelsome as possible without getting yourself into trouble”.
Included in the spies’ orders for sabotaging a company are instructions to:
- When possible, refer all matters to committees, for “further study and consideration.” Attempt to make the committees as large as possible – never less than five.
- Bring up irrelevant issues as frequently as possible.
- Misunderstand orders. Ask endless questions or engage in long correspondence about such orders. Quibble over them when you can.
- Haggle over precise wordings of communications, minutes, resolutions.
- Be unreasonable and urge your fellow-conferees to be “reasonable” and avoid haste which might result in embarrassments or difficulties later on.
- Don’t order new working’ materials until your current stocks have been virtually exhausted, so that the slightest delay in filling your order will mean a shutdown.
- To lower morale and with it, production, be pleasant to inefficient workers; give undeserved promotions. Discriminate against efficient workers; complain unjustly about their work.
- Fill out forms illegibly so that they will have to be done over; make mistakes or omit requested information in forms.
- Spread disturbing rumors that sound like inside dope.
The full document is published in full on the CIA website
Timeless Tips for ‘Simple Sabotage’ — Central … – CIAhttps://www.cia.gov/…/simple-sabotage.html
Central Intelligence Agency
Jul 12, 2012 – In 1944, CIA’s precursor, the Office of Strategic Services (OSS), created the Simple Sabotage Field Manual. This classified booklet described …[PDF]Simple Sabotage Field Manual – CIAhttps://www.cia.gov/…/CleanedUOSSSimpleS…
Central Intelligence Agency
Apr 2, 2008 – This Simple Sabotage Field Manual– Strategic Ser- vices (Provisional) – is published for the information and guidance of all concerned and will …
Images for cia sabotage manualReport images
More images for cia sabotage manual
CIA SABOTAGE MANUAL | Flickr – Photo Sharing!https://www.flickr.com/photos/mickie/sets/983397/
In the 1980s the CIA produced a small illustrated booklet in both spanish and english designed to destabilise the nicaraguan government and economic system.OSS Simple Sabotage Manual, Sections 11, 12svn.cacert.org/CAcert/CAcert_Inc/Board/oss/oss_sabotage.html
Editor’s Note: This is sections 11,12 of the OSS’s Simple Sabotage Field Manual, a 1944 document that has been declassified. The OSS became the CIA after …How to
Operate Like a Spy: CIA Declassifies OSS Field …www.theblaze.com/…/how-to-operate-like-a-spy-cia-declassifies…
TheBlaze
Feb 19, 2014 – As the CIA writes in their release of this field manual, “many of the sabotage instructions guide ordinary citizens, who may not have agreed with …
In the news
Declassified CIA documents detail how to sabotage employers, annoy bosses
The Independent – 1 day ago
A previously secret document titled “Simple Sabotage Field Manual: Strategic Services” …
More news for cia sabotage manual
..CIA: Five particularly timeless tips from the Simple Sabotage …www.networkworld.com/…/cia–five-particularly-timeless…
Network World
Jul 13, 2012 – CIA The CIA today published a very interesting piece of its history, the once classified “Simple Sabotage Field Manual,” which defines how the …
The “RATF*CKING” Of the American Voters: The Crime Without A Penalty
- Using the resources of taxpayer cash and public offices, an increasing number of Americans are being attacked and destroyed by their own elected officials
- Over 1000 companies offer criminally evil attack-and-destroy services, against voters, to politicians
- No laws prevent such attacks and politicians won’t put any laws in place because they use these attacks so much
Example cases:
http://thecleantechcrash.wordpress.com
and below:
Ratfucking
From Wikipedia, the free encyclopedia
Ratfucking is an American slang term for political sabotage or dirty tricks. It was first brought to public attention by Bob Woodward and Carl Bernstein in their book <as_men” href=”https://en.wikipedia.org/wiki/All_the_President%27s_Men”>All the President’s Men.
Contents
Background Woodward and Bernstein’s exposé All the President’s Men reports that many staffers who had attended the University of Southern California such as Donald Segretti, Tim Elbourne, Ronald Louis Ziegler, H. R. Haldeman and Dwight Chapin had participated in the highly-competitive student elections there. UPI reporter Karlyn Barker sent Woodward and Bernstein a memo “Notes On the USC Crowd” that outlined the connection. Fraternities, sororities and underground fraternal coordinating organizations such as Theta Nu Epsilon and their splintered rival “Trojans for Representative Government” engaged in creative tricks and underhanded tactics to win student elections.[1][2] Officially, control over minor funding and decision-making on campus life was at stake but the positions also gave bragging rights and prestige. It was either promoted by or garnered the interest of major political figures on the USC board of trustees such as Dean Rusk and John A. McCone.[3][4] It was here that the term ratfucking had its origin. It is unclear whether it was derived from the military term for stealing the better part of military rations and tossing the less appetizing portions away or if the military adopted the phrase from the political lexicon.
The term was made famous in Australia after the phrase was attributed to then Prime Minister Kevin Rudd at the 2009 Copenhagen Climate Change Summit.[5]
Usage in the U.S. militaryThe term ratfucking (rat in this case is shorthand for ration) is the unofficial slang term used by soldiers in the U.S. Army to mean the targeted pillaging of MREs (Meals Ready-To-Eat), which the U.S. military calls field stripping. It refers to the process of opening a case of MREs, of which there are twelve in a box, then opening up individual MRE packages, and removing the desired items (generally <as” href=”https://en.wikipedia.org/wiki/M%26M%27s”>M&M’s and other sweets), and leaving the unenticing remainder. It is a common but generally frowned-upon practice.[6]
Other usagesAn early use of the term (as “rat-fuck”) appears in Edmund Wilson‘s “The Twenties” in an entry dated February, 1922.[7]
A more benign use of the term “ratfucking” was commonplace in Southern California (and possibly other) college slang in the late 1950s to at least the early 1960s, meaning a prank. Around that time, Tony Auth was the cartoonist for the UCLA Daily Bruin. One of his cartoons showed a large, inebriated rat suggesting to another rat, “Let’s go PF-ing tonight!”, a play on ratfucking or “RF-ing”. The lead story in the January 6, 1961, California Tech, Caltech’s student newspaper, was headlined, “Tech Scores First Televised RF”. The article chronicled the Great Rose Bowl Hoax, which had just taken place. A political context was irrelevant to such usage; at the end of the article, an Editor’s Note both explained and bowdlerized: “RF (for Royal Flush) is a contemporary college colloquialism for a clever prank.”
References
- Matt Taibbi, Meet Mr. Republican: Jack Abramoff, Rolling Stone, March 24, 2006.
- Evan Wright, “Generation Kill”, p. 87
- Edmund Wilson, The Twenties, ed Leon Edel, Farrar Straus and Giroux, 1975, p. 116
Donald Segretti Tribute – The Triumph Of The Ratfuckers – Esquirecached
Oct 4, 2013 … Let us raise a morning glass to Donald Segretti, the ratfucker.
google
http://www.esquire.com/news-politics/p[…]25090/donald-segretti-ratfking-100413/
Ratfucking – A GOP Tradition | Correntecached
Mar 28, 2008 … According to Woodward and Bernstein, Nixon aide Dwight Chapin hired fellow USC alumnus Donald Segretti to run a campaign of dirty tricks …
google
http://www.correntewire.com/ratfucking_a_gop_tradition
Donald Segretti scene from All the President’s Men – Critical Commonscached
USC alum Donald Segretti talks about his involvement in pre-Watergate dirty tricks … Many of the tactics ( termed “ratfucking”) that Segretti and his team used to …
google
http://www.criticalcommons.org/Members[…]scene-from-all-the-presidents-men/view
Ratfucking – RationalWikicached
May 20, 2015 … Segretti was hired by the Committee to Re-elect the President (CREEP) to work his ratfucking magic for Nixon in the 1972 elections and funded …
google
http://rationalwiki.org/wiki/Ratfucking
Donald H. Segretti | All the President’s Mencached
In 1972, Donald H. Segretti held the title as the CRP’s political operative. Segretti was hired to run a slew of dirty tricks, dubbed as “ratfucking” against the …
google
Did Donald Segretti and his friends at USC invent “ratfucking”? What …cached
Ratfucking is an American slang term for political sabotage or dirty tricks. It was first brought to public attention by Bob Woodward and Carl …
google
http://askville.amazon.com/Donald-Segr[…]-word/AnswerViewer.do?requestId=450637
Ratfuckingcached
Ratfucking is an American slang term for political sabotage or dirty tricks. … portions away or if the military adopted the phrase from the political lexicon. The term …
wikipedia bing google yahoo
https://en.wikipedia.org/wiki/Ratfucking
Ratfucking – RationalWikicached
May 20, 2015 · This page is about electoral fraud. For fucking rats (if it actually fits), see bestiality. “Ratfucking” was a term used by Richard Nixon’s campaign …
bing google yahoo
http://rationalwiki.org/wiki/Ratfucking
Dirty tricks – Wikipedia, the free encyclopediacached
Dirty tricks are unethical, duplicitous, slanderous or illegal tactics employed to destroy or diminish the effectiveness of political or business opponents.
bing yahoo
https://en.wikipedia.org/wiki/Dirty_tricks
Rep. Todd Courser has a checkered political pastcached
On Monday, however, the attention was on the latest political scandal, with investigators combing through computer servers, e-mails and other documents from the …
bing yahoo
http://www.freep.com/story/news/local/[…]at-facing-increased-scrutiny/31435681/
Propaganda – RationalWikicached
Jun 09, 2015 · No, this is not about the Russian girl group of a similar name (Пропаганда). Or the German ’80s popstars. Or the album by the band Sparks.
bing yahoo
http://rationalwiki.org/wiki/Propaganda
The Boston Olympic Debacle – Grantlandcached
The very first American to win an Olympic medal was James Brendan Connolly — or Séamas Breandán Ó Conghaile, as he was born — who grew up as one of 12 children …
bing yahoo
It’s still Richard Nixon’s party: How Watergate shaped the …cached
Aug 08, 2015 · When your own lawyer calls it “ratfucking,” it might be time to think twice about what you’re doing. The man who didn’t think twice, of course, was …
bing yahoo
http://www.salon.com/2015/08/08/its_st[…]aped_the_modern_conservative_movement/
Political Awareness Matters: How Black Lives Matter Are …cached
Aug 08, 2015 · It’s time to call out BLM: If you want to change policy, and the racist culture handed down from Washington, you are going to need to win 200 seats in …
bing yahoo
http://www.dailykos.com/story/2015/08/[…]Screwing-Themselves-And-the-Rest-of-Us
Sharia Prince Owns Stake In FOX News Parent | Big Thinkcached
How ironic is it that the FOX News where Sean Hannity has been howling about Imam Feisal Abdul Rauf wanting “Sharia law” to replace our existing laws is the very …
bing yahoo
http://bigthink.com/Resurgence/sharia-prince-owns-stake-in-fox-news-parent
Feminist writers are so besieged by online abuse that …cached
Jessica Valenti is one of the most successful and visible feminists of her generation. As a columnist for the Guardian, her face regularly appears on the site’s …
bing yahoo
https://www.washingtonpost.com/opinion[…]b7dd-11e4-a200-c008a01a6692_story.html
Donald Segretti Tribute – The Triumph Of The Ratfuckers – Esquirecached
Oct 4, 2013 … Let us raise a morning glass to Donald Segretti, the ratfucker. … pause for a moment to pay tribute to a political visionary whose entire career …
google
http://www.esquire.com/news-politics/p[…]25090/donald-segretti-ratfking-100413/
Ratfucking – A GOP Tradition | Correntecached
Mar 28, 2008 … Maybe they are a special breed of GOP trolls called “ratfuckers.” Part I Ratfucking is an American slang term for political sabotage or dirty tricks.
google
http://www.correntewire.com/ratfucking_a_gop_tradition
Jonathan Korman on Twitter: “Mindboggling story of Nixonian …cached
Aug 13, 2015 … … Korman @miniver Aug 13. Mindboggling story of Nixonian political ratfucking using the Peace & Freedom Party, from @MarkAmesExiled …
google
https://twitter.com/miniver/status/631914760649334784
How to pick your opponent: A guide to gaming Republican primariescached
May 18, 2014 … Along with McCaskill, Democrats ratfucked a Florida House primary in …… Ratfucking is an American slang term for political sabotage or dirty …
google
http://www.dailykos.com/story/2014/05/[…]A-guide-to-gaming-Republican-primaries
ratfucking | The Vermont Political Observer.cached
Jun 11, 2015 … Well, the briefest of gubernatorial trial balloons has settled to the floor, like the birthday balloon that got a half-shot of helium. Deb Markowitz …
google http://thevpo.org/tag/ratfucking/
THE TACTICS OF THE ATTACKERS
By Thomas Winstead, Bob Unruh, Edward Snowden, Winston Emery & Piper Lee
Government sponsored character assassination delivered by Google, Gawker Media, IN-Q-Tel and New America Foundation; all of whom are financially, politically and operationally connected. Eric Schmidt ran and funded New America Foundation; Ran Google; Partnered and funded In-Q-Tel; hired, along with his associate: Elon Musk, In-Q-Tel executives; Worked with Gawker Marketers along with In-Q-Tel; was, himself and Google, funded by In-Q-Tel; funded the top 4 political campaigns, that all of those parties aggressively supported; and managed a business plan, that ran between all of those efforts, to ruin competitors and those who did not think like him, in any way possible.
Using the largest character assassination engine ever created. The Large Hadron Collider of defamation, Schmidt and his little Cartel went to work on enemies of his ideology. These were hit-jobs, using taxpayer dollars, against American born taxpayers, inside America, on U.S. soil because some politician or, campaign backer billionaire, wanted to hide their crimes.
VIDEOS:
DON’T MISS THIS ONE:
REFERENCE LINKS FOR DETAILS ON SOME OF THE PLAYERS:
What kind of company Google is:
http://www.whengoogleattacks.com
Where you should write to complain about these kinds of things:
http://www.opencongress.org/people/zipcodelookup
Who Eric Schmidt’s little hit-job spy buddies are:
http://www.inqtelcase.wordpress.com
How YOU can stop dirty politicians:
http://www.corruptionbusters.info
The details of their tactics:
http://www.paybackpolitics.org
How Eric’s Cartel Works:
ARTICLES CONFIRMING THE BACKGROUND:
Character assassination – Wikipedia, the free encyclopedia
Character assassination is a deliberate and sustained process that aims to destroy the credibility and reputation of a person, institution, social group, or nation.
en.wikipedia.org/wiki/Character_assassination
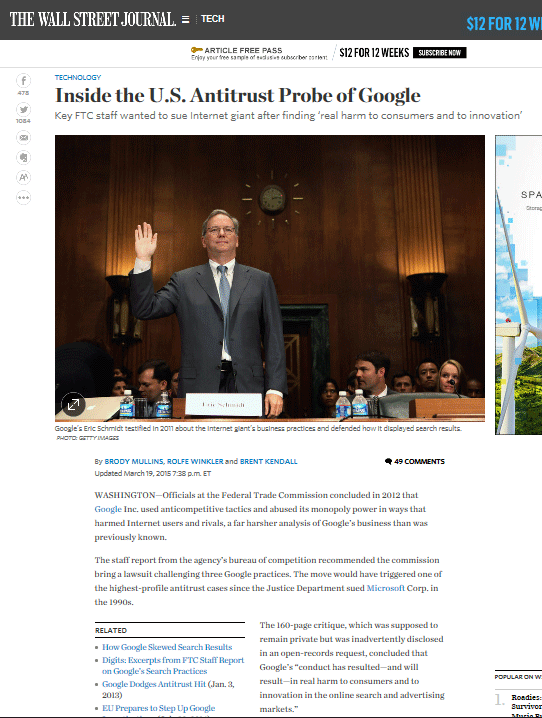
Google Search Results Rigged? – Outside The Beltway
Is Google manipulating its search results to keep competitors down? … When Google was a pure search engine, it was easy to appear agnostic about search results, … Are Google’s results rigged? Heck yeah.
outsidethebeltway.com/google-search-results-rigged/More results
Character Assassination | Definition of character …
Full Definition of CHARACTER ASSASSINATION : the slandering of a person usually with the intention of destroying public confidence in that person See character assassination defined for English-language learners Examples of CHARACTER ASSASSINATION None of those rumors are true. She’s been the …
merriam-webster.com/dictionary/character assassination
More results
Urban Dictionary: Character Assassination
Character Assassination is the act of attempting to influence the portrayal or reputation of a particular person, causing others to develop an extremely negative perception of him/her.
urbandictionary.com/define.php?term=Character Assassination
PCWorld; Google Defends Against Claims of Rigged Search …Google Defends Against Claims of Rigged Search Results. Google is aggressively defending itself against accusations it manipulates its search … or specialized image, shopping, flight, or movie results. And that’s not just Google; Bing, Yahoo and other search engines do the …
pcworld.com/article/257269/google_defends_against_cla…
Character Assassination Law & Legal Definition
Character Assassination refers to the slandering or vicious personal verbal attack on a person with the intention of destroying or damaging that person’s reputation or confidence.
definitions.uslegal.com/c/character-assassination/
Google Has Rigged It’s Search Results… …
The bclund Blog The Intersection of Markets, Trading, and Life! Main menu. Skip to content. Home; About Brian Lund; THE BEST OF bclund; Brian Lund In Media; Google Has Rigged It’s Search Results…Is Anyone Surprised? … To bolster its own listings, Google sometimes copied, …
bclund.com/2015/03/20/google-has-rigged-its-search-r…More results
character assassination – The Free Dictionary
character assassination n. The malicious denunciation or slandering of another person, especially as part of an effort to ruin the reputation of a public figure. character assassin n. character assassination n 1. the act of deliberately attempting to destroy a person’s reputation by defamatory …
thefreedictionary.com/character+assassination
Europe investigates Google: Rigged search rankings …Europe investigates Google: Rigged search rankings? More like this. Update: Google targeted by EU antitrust probe. Google Instant results: … it makes no sense. … Google is a search engine. … It s their job. If they are not allowed to do this, they cannot serve their users. …
computerworld.com/article/2469754/e-commerce/europe-investi…
Character Assassination – Changing Minds
Character Assassination . Techniques > Propaganda > Character Assassination. Method | Example | Discussion | See also . Method. Attack the person, showing them to be bad and unworthy.
changingminds.org/techniques/propaganda/character_assassina…
Spies and Honey Traps: PW Talks with Jason MatthewsI don’t know if there still is an operating Sparrow School, but I imagine honey traps are still used. … which continues the narrative with the same characters (and some new ones). There are recruitments, double crosses, despicable traitors, assassination attempts, and a desperate …
publishersweekly.com/pw/by-topic/authors/interviews/article/56…
EU competition commissioner ‘concerned’ Google is rigging its …… with competition commissioner Margrethe Vestager formally accusing the search giant of rigging its search engine and its Android smartphone . Jobs. Jobs; Cars. CarsIreland.ie; Used Car Search; Car Dealers; Deals. … EU competition commissioner ‘concerned’ Google is rigging its search engine …
independent.ie/business/technology/news/eu-competition-c…
Barbara Hartwell Vs. CIA: Honey Trap Trickster? Or CIA Assassin?… Honey Trap Trickster? Or CIA Assassin? … Here’s a little sample of Negri’s more recent character assassination regarding myself and my friends and colleagues Rayelan … But it’s getting late and this ‘Former CIA Assassin’ and ‘Honey Trap Trickster’ has grown tired of typing …
barbarahartwellvscia.blogspot.com/2006/11/honey-trap-trickster-or-cia-assas…
Julian Assange in the Honey Trap by Justin Raimondo …Julian Assange in the Honey Trap. How they snared him. by Justin … character assassination is an art, to be practiced with a fine attention to detail … One of the participants in the ensuing conversation describes her as “certainly an odd character,” who seemed out of …
original.antiwar.com/justin/2010/12/07/julian-assange-in-the-h…
Snowden Drip: Government Funded Character Assassination …Snowden Drip: Government Funded Character Assassination Squads Rampant Online From The Intercept: … the use of “honey traps” (luring people into compromising situations using sex) and destructive viruses. But, here, …
blog.agupieware.com/2014/02/snowden-drip-government-funded.html
By Bob Unruh
Journalist Glenn Greenwald, through whom document-leaker Edward Snowden previously rattled the entire National Security Agency, is now confirming Western intelligence networks strategize to place “trolls” on the Internet to undermine, discredit and destroy critics.
In an article posted on website Greenwald help create called the Intercept, Greenwald reports secret documents from the GCHQ – the United Kingdom’s version of the NSA – reveal “how western intelligence agencies are attempting to manipulate and control online discourse with extreme tactics of deception and reputation-destruction.”
He cites documents from the “previously secret” Joint Threat Research Intelligence Group in the U.K., which describe injecting “all sorts of false material onto the Internet in order to destroy the reputation of its targets” and to use “social sciences and other techniques to manipulate online discourse and activism to generate outcomes it considers desirable.”
“To see how extremist these programs are, just consider the tactics they boast of using to achieve those ends: ‘false flag operations’ (posting material to the Internet and falsely attributing it to someone else), fake victim blog posts (pretending to be a victim of the individual whose reputation they want to destroy), and posting ‘negative information’ on various forums.”
The document lists a “Disruption Operational Playbook” and subheadings titled “Infiltration Operation, Ruse Operation, Set Piece Operation, False Flag Operation, False Rescue Operation, Disruption Operation, Sting Operation.”
Regarding how to “discredit a target,” the instructions include, “Set up a honey-trap, change their photos on social networking sites, write a blog purporting to be one of their victims, email/text their colleagues, neighbors, friends etc.”
Sam Rolley at the Personal Liberty blog wrote that his organization for years has been “warning readers that the well-connected and ruling elite, displeased by this newfound proletariat freedom, have been prolific in attempts to undermine and marginalize information provided by any media outlet unwilling to obey the same unspoken rules that govern the content choices of major media outlets.”
“Now, thanks to the efforts of National Security Agency whistleblower Edward Snowden and journalist Glenn Greenwald, readers no longer have to take the word of ‘paranoid’ bloggers who relate tales of paid government trolls lurking in comment sections and other concentrated top-down efforts to muddy the information provided by alternative media,” Rolley said.
He warned that the “most disturbing confirmation provided in the newly publicized intelligence documents is that spy agencies in Western nations with free speech guarantees have been given carte blanche authority from political leadership to target private individuals and organizations deemed uncooperative with the will of the state with ruthless online reputation-destruction efforts.”
Greenwald said the discussion of many of the techniques “occurs in the context of using them in lieu of ‘traditional law enforcement’ against people suspected (but not charged or convicted) of ordinary crimes or, more broadly still, ‘hacktivism,’ meaning those who use online protest activity for political ends.”
Rolley said it takes “no stretch of the imagination – even for those who have resisted considering the possibility of malevolent intent on government’s part – to assume that the mission of organizations like the NSA and GCHQ is ultimately more about quelling citizen dissent than stopping citizen bloodshed at the hands of terrorists.”
“The mere existence of documents like those published this week,” Rolley said, “provides that the nefarious and long-suspected Internet activities of Western propagandists are not just plausible – they have very likely occurred in the comment sections and social media posts of articles like the one you are reading now.”
WND columnist Eric Rush highlighted the outrageous idea of government agents trying to destroy the reputations of critics.
“It is worth noting that in 2008, Cass Sunstein, an Obama adviser and the White House’s former head of the Office of Information and Regulatory Affairs … wrote a paper proposing that the U.S. government engage teams of covert agents and independent, ideologically kindred surrogates to employ precisely the aforementioned methods to achieve their objectives,” Rush said.
Greenwald said the “point is that, far beyond hacktivists, these surveillance agencies have vested themselves with the power to deliberately ruin people’s reputations and disrupt their online political activity even though they’ve been charged with no crimes, and even though their actions have no conceivable connection to terrorism or even national security threats.”
Greenwald said the British organization, GCHQ, in response to his questions, said only that it does not comment on intelligence matters.
“Furthermore,” the agency said, “all of GCHQ’s work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorized, necessary and proportionate, and that there is rigorous oversight, including from the Secretary of State, the Interception and Intelligence Services Commissioners, and the Parliamentary Intelligence and Security Committee.”
“Whatever else is true,” Greenwald wrote, “no government should be able to engage in these tactics: what justification is there for having government agencies target people – who have been charged with no crime – for reputation-destruction, infiltrate online political communities, and develop techniques for manipulating online discourse?”
WND previously has reported on leftist trolls operating online, including those with thousands of postings that would be unlikely to come from someone submitting comments during free time.
The report at the time said the trolls were performing a “disinformation” function typical of counter-intelligence efforts by intelligence agencies to confuse political enemies and refute or deflect opposing political views that are less susceptible to refutation by more traditional methods of debate and argumentation.
Typically, trolls operating on WND forums were defending Obama by posting specious and diversionary arguments with the goal of changing the subject and obscuring topics that could damage Obama, such as his birth records, life narrative, political history and policy preferences, including his current positions as president.
One was found to have posted nearly 4,800 comments over a two-year period. Another operated under different user names used various email addresses and nine different IP addresses to post 15,200 comments over 787 days on WND.com and FoxNews.com, as well as several smaller news websites, some of which had a local focus or interest.
The report confirmed many of the trolls banned from participating in WND forums appeared to have been operating on a professional level.
Read more at http://www.wnd.com/2014/02/govt-handbook-for-internet-trolls-uncovered/#lZFg1EdYRl9iTSC8.99
Who Is Gawker Media and Nick Denton? Let’s take a look at how the international news media answers that question:
Gawker Media: Hypocrites vs. Douchecanoes
by Matt Forney For TAKI MAG.com
In 2002, a failed British journalist named Nick Denton started Gawker, a bitchy gossip blog run out of his Manhattan apartment. Over 10 years later, Gawker and its sister sites have become the biggest names in clickbait “journalism,” pulling down millions of visitors a month and making its owner a millionaire several times over. The secret to Denton’s success? He took the aggressive, lynch mob mentality of British tabloids, which specialize in ruining people’s lives, and injected it into America’s comparatively placid, Oprahfied media market.
In particular, Gawker, Jezebel, Valleywag, and their sister sites specialize in witch hunts: digital vigilantism against those who fail to keep up with leftist orthodoxy. Geoffrey Miller, Pax Dickinson, Justine Tunney, Violentacrez: the list of people whom Gawker has garroted for “racism” or “misogyny” could fill a phone book. With an army of Twitter twits behind it, Gawker Media truly is the moral majority of the left, instigating mob action against those who sin against the religion of tolerance. Gawker’s provocations are even encouraging real-world violence now, as Valleywag’s overfed man-baby of an editor Sam Biddle eggs on attacks against San Francisco tech workers from the safety of the East Coast.
Video Player
00:00
Use Left/Right Arrow keys to advance one second, Up/Down arrows to advance ten seconds.00:00
18:53
Use Up/Down Arrow keys to increase or decrease volume.
“Which makes the revelation that Denton has been allowing trolls to terrorize his female employees all the more delicious.”
For the past few months, 4chan has been engaged in a trolling operation against Jezebel, posting pictures of rape and gore porn in the comments section. Despite the fact that these shocking and disgusting images are stressing out staffers to the point where they’re developing PTSD, Denton has steadfastly refused to do anything about the problem. Jezebel’s staff recently snapped and posted an open letter on the site demanding that Gawker Media do something, calling 4chan’s trolling “a very real and immediate threat to the mental health of Jezebel’s staff and readers.”
Fat chance of this happening, however. As others have pointed out, Gawker Media’s business model depends on getting clicks; indeed, their writers are paid according to how many page views their articles get. Since comments help drive traffic to websites, fighting 4chan’s rape porn trolling will reduce Gawker’s profitability. Not only that, Google itself ranks web pages according to how many comments they have, as comments are extremely difficult to fake. Fewer comments means a lower page rank, which translates into less search traffic and less money for Denton to blow on exotic vacations with his boy-toy hubby. If Gawker Media was willing to testify in federal court as to why they should be allowed to rip off their interns, you can bet your bottom peso that they aren’t going to do jack about this.
Gawker Media Attack Specialist Adrian Covert of San Francisco. Now under 24/7 electronic surveillance for “suspicious activities”
And there’s the punch line. Gawker Media, the company that gets people fired from their jobs for making “sexist” jokes, has been creating a hostile work environment for its women staffers for months. They’re the leftist equivalent of a priest who rails against homosexuality only to be caught molesting altar boys in the confessional booths. In staying silent on this for so long, Dodai Stewart, Lindy West, and Jezebel’s other star employees have shown themselves to be frauds. They don’t care about feminism, “fat shaming,” or whatever cause they’re screeching about today; all they care about is money and power. And now we have the proof.
Please share this article by using the link below. When you cut and paste an article, Taki’s Magazine misses out on traffic, and our writers don’t get paid for their work. Email editors@takimag.com to buy additional rights. http://takimag.com/article/gawker_media_hypocrites_vs_douchecanoes/print#ixzz3CCvoAIP4
Advertisers Ditch Gawker Media In Droves. “Brand Tainted” says Forbes Exec. Gawker’s Denton Sweats Over Decline in Web Ad Revenues – CBS NewsGawker Media’s Nick Denton has made a horrible prediction regarding internet adspend for the next year: … Gawker’s Denton Sweats Over Decline in Web Ad Revenues. Shares Tweets Stumble … But the web ad economy as a whole will be the beneficiary of falling budgets.
cbsnews.com/news/gawkers-denton-sweats-over-decline-i…
Nick Denton charged with ordering phone-hacking, helping Anonymous hackers, stealing Mitt Romney’s tax records, hiding money in Russia and Caymans and MORE…IS GAWKER MEDIA THE WHITE HOUSE PRESS SECRETARY’S “PLAUSIBLE DENI-ABILITY” HIT SQUAD? STILL MORE…‘Straight To Hell:’ Reflections On Annie, Gawker …I feel like I’m probably going straight to hell for all of this. But, given all the other shitty … Emily Ratajkowski entertainment expats facebook Gawker Gawker Media gender hipsters Hollywood Hugh Hefner inter-racial dating internet Jezebel Julia Allison korea liberalism …
migukin.wordpress.com/2014/08/06/straight-to-hell-reflections-o…
More from migukin.wordpress.com
Terror– John Cook of Gawker; now of Greenwald – NOT CIA’S FRIEND!Gawker Tries to Reveal Identity of CIA Agent Behind Bin Laden KillBy Jana Winter
May 1: Secretary of State Hillary Rodham Clinton, President Barack Obama and Vice President Joe Biden, along with with members of the national security team, receive an update on the mission against Usama bin Laden in the Situation Room of the White House.APThe Gawker website is under fire for trying to expose the CIA agent who may have helped lead the effort to kill Usama Bin Laden — despite efforts by the U.S. government and media to keep his identity secret for security reasons.
Using red arrows pointing to a full-length picture and close-up photos of the possible agent, Gawker reporter John Cook on July 6 wrote a piece under the headline “Is This the Guy Who Killed Bin Laden?” The story has since sparked an angry response from former intelligence agents — as well as Gawker’s own readers — who say Cook’s post was irresponsible and could have deadly consequences.
“This whole business of exposing people is a real serious matter. It’s not entertainment, some people may think it is, but it’s not … There are real people out there that are going to be killed because of this,” said Charles Faddis, a former CIA operations officer who spent 20 years working international hot spots and who headed the CIA’s Terrorist Weapons of Mass Destruction Unit before retiring in 2008.
“I don’t have a lot of patience for this,” added Faddis, speaking about attempts to out the identity of a CIA operative. “This is serious, this is really serious. It’s completely irresponsible.”
Some Gawker readers also weren’t amused. A commenter named “Myrna Minkoff” wrote in response to Cook’s story:
“If this is the guy who tracked down Bin Laden, I can think of no better way to thank him for his outstanding civil service than by outing him on a highly trafficked web site and putting his career, his life, the lives of his loved ones in danger. Hooray!”
Another commenter “joelydanger” wrote:
“Consider that the next time you decide to write another article that tries to glorify DEVGRU, the CIA, or anyone and anything else used on the mission. You’re causing harm and danger to the very people you’re claiming to be heroes.”
But Cook insisted he didn’t compromise anyone’s security by posting the photos.
“I do not believe my post put anybody in physical danger,” Cook said in an email response to several questions posed by FoxNews.com. “I do not believe that people whose photographs are distributed by the White House as part of its public relations efforts have a reasonable claim to ask that no one speculate as to who they are.”
Cook was referring to a series of official White House pictures taken from the Situation Room during the raid on Bin Laden’s compound in Pakistan. The most famous of those photos, seen on televisions, newspapers and websites around the world, showed President Obama, Vice President Biden, Secretary of State Hillary Clinton, Defense Secretary Robert Gates and other officials watching a live feed of the raid.
Barely visible in that photo is the right jacket arm and the bottom of a necktie that appear to belong to a tall man standing behind Gates. Other pictures taken in the Situation Room during the raid, posted on the White House Flickr feed, show full-on shots of a tall man whose jacket and tie appear to match those of the man standing behind Gates in the earlier photo.
On July 5, the Associated Press published an extensive article on a CIA agent who led the hunt and eventual takedown of Bin Laden. The article referred to the agent only as “John,” explaining: “The Associated Press has agreed to the CIA’s request not to publish his full name and withhold certain biographical details so that he would not become a target for retribution.”
Later that same day, the website Cryptome, a Wikileaks competitor that publishes leaked, sometimes classified documents and information, used clues from the AP article to home in on photos from the White House Flickr feed and other AP photos that might show “John.” The article noted that “John” appeared just out of frame in the famous photo.
The following day, Cook picked up the Cryptome info and published the photos from the White House Flickr feed, beneath the “Is This the Guy Who Killed Bin Laden?” headline. Cook’s post also included an AP file photo of CIA Director Leon Panetta leaving a briefing on Capitol Hill, where the man who may be “John” is seen in the background.
“Of course, it could be a random staffer who happened to be in both locations with John,” Cook wrote. “Or it could be the guy who iced bin Laden.”
The New York Observer posted a story late Tuesday that claimed to have confirmed the identity of the CIA agent, starting with the AP article and the Situation Room photo, and it posted photos online of the man it said was the agent.
Cook said he and his Gawker editors discussed potential safety concerns before publishing the information and photos.
“We came to the conclusion that it is highly unlikely that the White House would distribute for publication a photograph of a man whose life would be endangered if his photograph were ever published. Likewise, we decided that it is highly unlikely that such a man would publicly accompany the director of Central Intelligence, in the presence of AP photographers, to Capitol Hill to testify.”
But those White House photos do not identify the man in question, only noting that the group of people are “members of the national security team,” numerous Gawker commenters pointed out.
“You seem to have not noticed that they took great pains to make sure his face wasn’t in the shot and he was never identified by name,” Myrna Minkoff wrote, when another commenter challenged her criticism of the Gawker post.
Other commenters chimed in.
“Sure it’ll put him, his friends, and his family in danger regardless of whether or not he’s actually the guy, but it’ll generate some pageviews and advertiser revenue, and that’s the IMPORTANT thing, right?” wrote someone using the name “dgoat.”
“You should still be ashamed of yourselves.”
Sortie en merEmbarquez pour une expérience interactive et immersive. … speakers and fullscreen recommended
One Denton Bio | Gawker Media LLC and Nick Denton- The …The headquarters of Gawker Media, … (Ironically, it was one of the few things he’s ever done mainly for the hell of it.) … Blog at WordPress.com. Follow. Follow “Gawker Media LLC and Nick Denton- The Killing of Babies …
gawkerhell.wordpress.com/2012/08/27/one-denton-bio/
More from gawkerhell.wordpress
“Gawker is the most vile and evil example of the written word in history”, says employee. What Gawker Media Is Doing About Our Rape Gif ProblemOn Monday, we posted an open letter to the management of Gawker Media, our parent company, regarding an ongoing problem that we here at Jezebel could no longer tolerate: horribly violent rape gifs that were consistently appearing in our comments. For months, we asked Gawker Media HQ for help with
jezebel.com/what-gawker-media-is-doing-about-our-rape…
Jezebel calls out Gawker Media for failing to address …Jezebel calls out Gawker Media for failing to address incessant misogynist comments … we’d report the hell out of it here and cite it as another example of employers failing to take the safety of its female employees seriously.
salon.com/2014/08/11/jezebel_calls_out_gawker_media…
Gawker and the Rage of the Creative Underclass — New York …Everybody Sucks Gawker and the rage of the creative underclass. By Vanessa Grigoriadis; Published Oct 14, 2007 ; … Gawker made its debut under the leadership of Nick Denton, the complicated owner of the blog network Gawker Media, …
nymag.com/news/features/39319/
Gawker Sucks and Here is Why | The WritingsPerhaps you, like everyone else who uses the web, likes to visit gossip sites like Gawker. I have had it with those sites. Their trade is in lies, deception, … Gawker Sucks Even More | Gawker Media. Leave a Reply Cancel reply. Enter your comment here …
neobiblical.wordpress.com/2011/04/07/gawker-sucks-and-here-is-why/
More from neobiblical.wordpress.com
Gawker Sucks – “Free Beacon” — Breaking News, Politics …Gawker Sucks. Share. Tweet. Email. … It is unclear to me how Gawker Media’s actions are materially different from, say, Napster circa 2000 when it was sued out of existence for facilitating the illicit downloads of copyright material. Who knows.
freebeacon.com/blog/gawker-sucks/
Who else hates Gawker Media? – Boycott-Gawker-And-GizmodoWho else hates Gawker Media? Nobody who works at Gawker/Gizmodo/etc. should ever work again! Butt handed to Gawker; … http://juicedsportsblog.com/2008/05/gawker–media–sucks.html http://suckreport.com/search/gawker http://tomsucks.wordpress.com/2008/05/14/gawker–sucks/
boycott-gawker-and-gizmodo.weebly.com/who-else-hates-gawker-media.html
More from boycott-gawker-and-gizmodo.weebly.com
Why Digg Really Sucks and Gawker Media Probably Does Too …Right on. I won’t say that most of the stuff on Digg is bad. It’s just not that great. Meh. But I really agree with you that there are way too many “me too” blog posts out there.
imaginaryplanet.net/weblogs/idiotprogrammer/2007/06/why-digg-…
New Statesman | Reddit blocks Gawker in defence of its right …Links from Gawker are banned from /r/politics, after journalist threatens to reveal the identity of the man running Reddit’s “creepshots”, “beatingwomen” and “jailbait” forums.
newstatesman.com/blogs/internet/2012/10/reddit-blocks-gawk…
Gawker Sucks | Exposing “Gawker Medias” racist Slants one …Gawker Media gets traffic with copyrighted material? I find this bit even more interesting, … Follow “Gawker Sucks” Get every new post delivered to your Inbox. Powered by WordPress.com …
More from gawkersucks.wordpress.com
Gawker Sucks – blogspot.comGawker Sucks Sunday, August 24, 2014. … Earlier today, Joel Johnson announced Gawker was disabling all image uploads in their comments. … And you can be sure the top guys at Gawker Media, like Joel Johnson, are now looking into it!
More from gawkersucks.blogspot
Gawker Sucks: Finding MobutuGawker Sucks. Sunday, December 9, 2012. Finding Mobutu. Most people reading this are probably familiar with Gawker Media properties.
gawkersucks.blogspot.com/2012/12/finding-mobutu.html
More from gawkersucks.blogspot.com
Gawker Mediaとは – goo Wikipedia (ウィキペディア)Gawker Media. From Wikipedia, the free encyclopedia. Vanessa Grigoriadis, “Everybody Sucks: Gawker and the rage of the creative underclass, New York magazine, October 22, 2007.
wpedia.goo.ne.jp/enwiki/Gawker_Media
Gawker Media – Wikipedia, the free encyclopediaGawker Media is a Cayman Islands1 corporation online media company and blog network, founded and owned by Nick Denton based in New York City. It is considered2 to be one of the most visible and successful blog-oriented media companies.citation As of March 2012…
wikipedia.sfstate.us/Gawker_Media
More from wikipedia.sfstate.us
Gawker Writers Have to Work Weekends Now Too | New York ObserverNick Denton, for his part, said that the weekend plan is “nothing new,” and that in the first half of the year, … and said he thinks it “sucks.” Share this: Facebook; Twitter; Google; LinkedIn; Print; Email; Filed under: Alex Pareene, Gabriel Snyder, Gawker, Nick Denton, The Media Mob. Comment .
observer.com/2008/12/gawker-writers-have-to-work-weeke…
Nick Denton – Wikipedia, the free encyclopediaNick Denton, born 24 August 1966, is a British journalist and internet entrepreneur, the founder and proprietor of the blog collective Gawker Media, and the managing editor of the New York-based Gawker.com.
en.wikipedia.org/wiki/Nick_Denton
Shots In The Dark: Why Gawker SucksI was just googling “Gawker sucks” and this came up making a very clear point of why I was googling this phrase in the first place. They’re not even funny.
richardbradley.net/2005/11/why-gawker-sucks.html
Oh my! Gawker’s Nick Denton’s ex boyfriend is not happy with his new boy toy.
By Christopher Koulouris For http://scallywagandvagabond.com
Frankly there’s nothing more delicious than watching someone famous for ripping people’s alive (yes journalism sucks these days) apart become his own parody on manners and gossip. That said there was a twinkle of relish when I came across page 6‘s interesting expose on Nick Denton, the media zealot of Gawker media (which owns a smattering of salacious dribble including gawker, jezebel,deadspin,lifehacker and jalopnik)who has suddenly found himself the scorn of a former jealous and one imagines scorned lover.
page 6: Gadfly Gawker Media head Nick Denton recently changed his Facebook status from single to “in a relationship,” but not everyone seems to be happy about it.
Sources say an angry ex of his new boyfriend tossed a brick through the window of Denton’s SoHo loft building recently, and has been causing enough further trouble that the police have been contacted.
Not to drift too much from Nick but I too was quite aghast when I decided to publicly note that I was no longer single but in a relationship on Facebook (for some reason I was quite surprised by the number of people who responded to what I perceived to be something really quite arbitrary and of little consequence in the world scheme of things, but yes people do pay attention it seems) which perhaps might explain the sudden attention that Mr Denton received when he publicly decided to note that he was in fact now no longer a pedophile or single.
Of course who also noted one assumes is a scorned former lover of the media titan who felt compelled enough to go smashing bricks into his former lover’s abode. And perhaps with good reason as it appears Mr Denton’s attentions have now turned to presumably a nimble agile and quite pretty young man ( 28 year old Derrence Washington) who it appears is an English actor here in NYC on tour (permanent tour one supposes).
What perhaps make the intrusion even more charming (not to suggest they are ever charming) is Mr Denton’s own acknowledgment that he is now being served the same dish he is well known famous for serving up on a regular basis.
When we asked Denton about the incidents, he told us via e-mail: “After that Hulk Hogan sex tape on Gawker, I can hardly complain about intrusion into my private life!
“Yep, love is messy,” he added.
Indeed love and gossip are quite messy but that said I’m betting Mr Denton is loving every minute of it. If I could suggest one thing Mr Denton, perhaps if you were to send a bouquet to the former lover it may temper their ire. I know it worked for me once. Oh dear…
above image found here
——————————————————————————–
Who owns the Gawker Media company? – Ask questions, Find …… Who owns the Gawker Media company? : … Jossip founder David Hauslaib estimated Gawker.com’s annual advertising revenue to be at least $1 … but someone else will have better luck selling the advertising than we did.”[5] In a fall 2008 memo Denton announced the layoff of “19 of our …
askville.amazon.com/owns-Gawker-Media-company/AnswerViewer.do…
NICK DENTON SAYS, ON CAMERA, TO NBC, THAT HE MAKES A LIVING DESTROYING PEOPLE:http://jimromenesko.com/2012/03/06/gawkers-nick-denton-talks-to-nbcs-rock-center/
Billionaire industrialists are campaign backers who hire writers/bloggers (known as “shills”) who sell their services as character assassins.There is also a whole industry of character-assassins-for-hire today. They work for corporations, tabloids, investment groups and political organizations. The largest groups of them are in New York City and Silicon Valley. Their job is to destroy people and things. Their attacks on competing product innovations are the most prevalent. In the old days, it used to be cheaper to destroy your competitor than buy their stuff. Now, that is no longer true but they still try it anyway.
Good Inventors have built, patented, and launched some technologies that threatened billions of dollars of existing companies who were doing things the old-fashioned way. Some of them got unhappy and thought it might be cheaper to start trouble rather than pay for the technology that they later ended up copying. History has shown that the big-company-IP-theives were always wrong on that assumption, and that it was always cheaper in cash and bad PR recovery to have paid the inventor in the first place. Stealing IP never pays.
As part of the Playbook for attacking a new competing technology, the big competing entities hire digital THUGS to attack and seek to destroy the new, better, competing technology.
During the on-going IP theiving, a very aggressive group of companies launched a character attack on the inventors who “sort of reported them” to federal law enforcement agencies for stealing federal tax money, in the course of trying to control the market that the inventors had embarked on, and some of the bad-guy insider people got fired, some had to quit big government jobs and some got indicted (Over $25B+ in tax revenue is still missing and investigations are ongoing). It is the same five people, but they have spent millions of dollars on their character attack effort against the inventors. So far, the results are that they just keep getting in more trouble and the inventors they targeted get more jobs because the bad guys made such a stink. (It helps when a large number of Senators, major newspapers and federal prosecutors are backing the inventors up and when the bad guys found out that every communication they engaged in was under surveillance and archived.)
Because these are standard “Playbook” attack articles, the authors never interview those they are ordered to attack. In fact, they go to great lengths to make sure none of their targets are interviewed or allowed to provide counter-points in advance. They never allow the targets to fact-check the attack articles because they don’t want any factual data in their articles. Their attacks are contrived to simply be malicious, fake, damaging efforts to seek to destroy the lives of their targets and curtail or impede business, delay financing and slow public policy efforts. While the inventors have assisted major press, citizens groups and federal agencies with investigations that have caught the bad guys engaged in crimes, the hired blogger and attack writers are ordered to seek to punish those inventor/advocates for doing the right thing. There are usually only a couple of nasty attack articles, but the bad guys spend vast amounts of money to replicate them everyplace they can, and artificially stick them to the top of search engines. Some bad guys that do this, pay off the investors in search engine companies to have those search engines results artificially manipulated in order to keep the negative attack information at the top of the results in order to maliciously cause as much damage as possible.
The decades of thousands of positive, factual, fair and unbiased articles and references about those the inventors they attack, and their projects, stand in stark contrast to the few attack articles by the same entity operating under a variety of pseudonyms.
These people, some of them associated with the highest levels of government, have hired a tabloid organization, which owns many tabloids under different names, as their covert mouthpiece, to publish character attacks and purchase synthetically manipulated search engine result rankings from friendly search engine owners (Now under investigation). Multiple well know politicians have been attacked in the same manner and each has now hired investigators to confirm algorithm manipulation.
Why is this point a big deal? Because small companies that sell their ideas have a large suite of issued patents, validated by millions of dollars of outside appraisal third-party review, which they designed and engineered. They don’t “troll”, these are their in-house products. It is their bread-and-butter. The U.S. Government, The international industrial press, executed NDA’s, industry awards, published broadcast videos, documented presentations, patent documents, public demonstrations, published communications and other hard data prove, beyond question, that the handful of things that those other companies copied; were created first by them. In most of these cases, those few things just happen to have all been big hits in global markets.
Some of these inventors intellectual property is quite controversial because they were the first to create a few things that others, years later, copied and made billions of dollars on. Those others do not like people to know some of their things were not invented by them. They all feel that “Big companies can’t steal from small inventors and get away with it, with impunity.”
When major companies in a few large industries get caught stealing IP assets, violating the law, or both; they get unhappy and hire “Swift-Boat”-type cyberbully attack bloggers. The authors of those attack articles are also most of the commenters in the comments-section under each article, commenting under hundreds of different fake names. It is an honor that the bad guys wish to acknowledge the effectiveness of these inventor’s by attacking them with a malicious PR strike. It is good to know that they think their inventions and public policy efforts are that productive.
Law enforcement agencies, public policy law firms, constitutional lawyers and media investigators have now begun to successfully prosecuted those who sell their services as character destroyers.
Most intelligent people would not judge someone based on one read of a tabloid article no less credible than the rags at a supermarket check-out stand about actresses weight problems. Alas, some readers are not very smart and do not think to seek counter-point viewpoints.
The references, track-record and durability of the inventors that are attacked speak for themselves as positive credibility.
These product designers have always started a company to commercially sell the products they developed entrepreneurially, or, their products were produced for a corporate client or agency. Sometimes, though, a big copy-cat group floods out those start-up ventures with counter-marketing, so the inventor is forced to market the IP assets to create an effective ROI for their investors. A smart inventor always arranges for their investors and partners to be routed to their ROI by either selling the product in retail or commercial markets or selling/licensing the IP.
A savvy inventor has no intention of ending up like Philo Farnsworth, Robert Kearns, Preston Tucker or the folks in this link. They intend to be alive and enjoying the benefits of the things they built so they will always fight for fairness, against the bullies who take things, who believe they are too big to be spanked.
TO SEE AN ACTUAL EXAMPLE OF A TAKE DOWN ATTACK ON AN INVENTOR – CLICK HERE
The Copy Cat Playbook
If you make something that actually makes a difference in the world, it will often be attacked by the people who make the thing that it competes with.
The standard Playbook play they will use against you is:
A. Big company hears about a competing effort
B. Big company orders a hit on competing effort
C. Hit-team thugs, working for big company, launche counter-measure campaign consisting of:
1- Attack articles creating non-existent questions about the new technology are generated
2- Attack articles character-attacking the creators of the new technology are generated
3- Phone calls, and fake negative “whitepapers” to potential investors in the new technology to leverage them from investing
D. After stalling competing effort, big company copies competing technology directly or sets up “front company” they later “acquire”.
The people attacking you want to minimize your power to achieve. They will use every dirty trick in the book to stop you from affecting their profits if you have a product or service that is actually good. For example; they will author a character assassination blog, article or letter and then call your employers HR department and say: “Hey, did you see this thing about one of your employees”, and you will be mysteriously fired the next day. Then they will post links and references to it in all of the employment databases to make it very hard for you to get another job.
The upside is that anybody who denies you a job because of this can be subpoenaed, all of their phone calls and files can be subpoenaed, their workmates can be subpoenaed. If you can find that you lost any income or work because of anything the character attackers did, you can sue them and win.
Inventors+ Who Changed the World and Got Screwed in Return
By Karl Smallwood, Mike Floorwalker March 03, 2013
As we’ve discussed before, just because your hard work and perseverance led you to create something that changes the world, it doesn’t mean that you’ll get fame, fortune, or the slightest bit of recognition out of it. In fact, some inventors get so little credit that we completely forgot about them in our previous article, and since we really don’t like angering the ghosts of people who could probably invent a way to punch us from beyond the grave, here they are.
#6. Siegel and Shuster, Superman’s Creators
Jerry Siegel and Joe Shuster created Superman, the most famous superhero ever, perhaps with the exception of Spider-Man or that kid who changes the channel with his eyes in X2.
Debuting in 1938, Superman was an instant success. DC Comics soon followed up the “man in underpants punches criminals” concept with Batman, and that was it, there was no turning back: Siegel and Shuster’s creation had started a multibillion-dollar industry that is still going strong today, spawning toys, T-shirts, and, oh yeah, some of the highest-grossing movies of all time.
Nice one, Siegel and Shuster!
Alan Light “Take it from us, kids: Work hard, change the world, and you too can see absolutely no reward from it!”
But Then They Got Screwed
“Nice one, Siegel and Shuster” is exactly what DC must have said, in a sarcastic tone, when the duo famously sold them all rights to Superman for a measly $130, a check that’s now ironically worth hundreds of thousands of dollars.
At the time, no one suspected that the guy in blue pajamas that they’d been drawing would turn into a cultural icon — so when he did, and Siegel and Shuster continued getting squat, the pair embarked on perhaps the longest clusterfuck in copyright history.
The duo spent the better part of their lives unsuccessfully trying to reclaim some part of their creation, only to be rebuffed time and time again. While DC raked in billions from Superman alone, Siegel and Shuster lived the lives of paupers. They were given a yearly pension in the late 1970s by Warner Bros. (which had purchased DC), but only because the studio couldn’t afford the bad publicity with a Superman movie on the way.
In 1999, three years after Siegel died, his family successfully won the rights to his half of his creation. A happy ending, right? Nope! This meant dick to Warner Bros., who still refused to pay them a penny, leaving them to fight in court for another 10 fucking years. And the superdickery continues: More recently, documents disappeared from Siegel’s daughter’s attorney’s office and somehow wound up in the hands of Warner Bros. executives.
#5. Philo T. Farnsworth, the Farm Boy Who Invented Television
Philo Farnsworth, besides having the supreme honor of inspiring a Futurama character, was a serial inventor with a list of credited patents longer than his forehead.
Among those patents was the one that made television possible: an “image dissector” that could capture images as a series of lines to be displayed electronically. If that isn’t impressive enough for you, consider the fact that Farnsworth came up with the idea at age 14, while growing up on a farm in Idaho, and first demonstrated it at 21, in 1927. If that didn’t make you feel bad about yourself, it should have.
But Then He Got Screwed
When the young inventor applied for a patent at age 20, David Sarnoff of the Radio Corporation of America took notice. Radio had a pretty cozy spot at the center of the American living room at this point, and Sarnoff wasn’t interested in letting that change. And if it did, then he would at least make sure that RCA would be the one getting rich from it.
Sarnoff kept Farnsworth tied in a series of legal battles over the next decade using a number of bullshit tactics, likehiring a Russian inventor to spy on him or using said inventor’s earlier patents (which they could never get to work) to argue that he had invented TV. At one point Sarnoff just said “Fuck it” and started making TVs without paying Farnsworth. RCA was eventually forced to pay him a one-time $1 million licensing fee, but it wasn’t worth the emotional stress that had left the man crippled.
Then the whole television business was put on hold when the ’40s rolled around and the government told everyone to focus on building things that could kill Germans. The final blow came when Farnsworth’s patents expired just as World War II ended … and, what do you know, television sales skyrocketed. RCA, or anyone else for that matter, no longer had to even pretend to give a shit about paying Farnsworth for his invention.
It wasn’t until 20 years after his death that the government decided that Farnsworth probably deserved some recognition. No shit.
Following Farnsworth’s final wishes, his statue is about to insert something into Sarnoff’s anus.
#4. Edwin H. Armstrong, the Father of FM Radio
When is the last time you listened to AM radio? Intentionally? The sound quality is so bad that most of the programming is reduced to things that already sound like shit, like conservative talk radio or a single, never-ending religious sermon in Spanish.
The much superior FM was invented by Edwin Armstrong, who created a system to reduce interference across radio bands in the 1910s. He continued his lifelong vendetta against crappy sound in the ’20s, when he came up with frequency modulation (FM) as a way to reduce static. We will now reiterate that he developed all this technology nearly 100 years ago, and it’s still present in all modern radios.
But Then He Got Screwed
Things seemed to be going swimmingly for Armstrong for a while, but it was at this point that a remarkably smug asshole came into the picture.
Yes, David fucking Sarnoff from RC-fucking-A proceeded to mess with the life of yet another world-changing inventor. Sarnoff had built his empire with AM radio, so he decided that if FM was the way of the future, then he’d do anything possible to pull a John Connor on that future. Since Armstrong wouldn’t relinquish his patent, Sarnoff made sure that RCA not only stopped supporting the development of the new technology, but actively tried to stop it.
In 1937, Armstrong used money from his own pocket to build the very first FM radio station. Another followed, then another, until by the mid ’40s a string of stations known as the Yankee Network were busy convincing everyone of the superiority of FM, just by existing. And then it all stopped.
In a dick move of epic proportions, Sarnoff successfully lobbied the FCC to move the FM band to a different place on the dial, from 42 to 50 MHz to 88 to 108 MHz. While there were somewhat valid technical reasons for this, a happy side effect for RCA was that it made all of Armstrong’s stations instantly obsolete.
It took decades for FM radio to recover. In the late ’70s, it finally surpassed AM, but Armstrong was long gone by then, having committed suicide in 1954 by jumping from the 13th floor of his office building, presumably screaming “FUCK SARNOOOOOOFFFF” all the way down.
#3. John Walker, Inventor of the Match
About 500 billion matches are used every year in the United States — that’s the kind of volume you can do when your product sets itself on fire with every use. Before the invention of self-igniting friction matches, people simply used sticks that caught on fire when you, y’know, put them near fire.
This changed when John Walker, an English chemist born in 1871, began coating sticks in a number of dangerous-sounding chemicals until he happened upon one that, when struck against a surface, erupted in flames. Other self-igniting matches had been tried before, but they were extremely impractical, by which we mean that a lot of people probably lost their eyebrows or worse using them.
And clearly, eyebrows were very important to this man.
Walker’s invention caught on fire, both literally and figuratively, and we still keep matches around today, despite the fact that we’ve all heard of lighters.
But Then He Got Screwed
Walker, unaware of the potential of his invention, worked on these new “friction lights” for about a year, then promptly forgot about the whole thing and stopped selling them. People close to him implored Walker to patent his friction light, since he’d just revolutionized the creation of fire and all. Walker declined, believing that his invention could better benefit mankind without a patent.
Others, however, believed that Walker’s invention could better benefit mankind by making them rich.
Getty- “How does fire help humanity if it doesn’t allow me to buy prostitutes?”
In 1829, another inventor named Isaac Holden independently came up with an improved version of Walker’s friction matches. Like Walker, Holden neglected to patent his idea … and that’s where one Samuel Jones came in. Jones, realizing that Walker and Holden had effectively created one of the most useful inventions in the history of civilization and weren’t making money from it, decided to do it on their behalf, because he was nice like that.
Almost immediately, Jones patented the exact same thing and began selling it under the name “Lucifers,” because fuck it — if you’re gonna be evil, you might as well go to the source. Soon other brands began offering improved versions of the same thing, all for a price, of course. It wasn’t until they were all dead that Walker was credited for his invention, and Jones for being a douchebag.
#2. Stephen Foster, the Father of American Music
There are some tunes that you’re just born knowing. If we somehow forced you to hum a melody right now, chances are that a great number of you would go with something like “Oh! Susanna”:
Or “Camptown Races” (you know, the one that goes “doo-da, doo-da”):
Or maybe something more nostalgic, like “Old Folks at Home”:
Man, can you imagine if all these songs had been written by the same guy, and that he’d been actively trying to get money from them? That dude would have been richer than Madonna and Bono combined.
Actually, all those songs and more were written by the same person, and he did try to cash in on them — the keyword being “try.”
Then “she” came around the mountain and snatched up all his royalties.
But Then He Got Screwed
In the 1800s, Stephen Foster wrote classics like “My Old Kentucky Home” and “Beautiful Dreamer” and over 200 other songs. Foster was a professional songwriter before those existed. Seriously: The profession literally did not existbefore Foster trailblazed it like a motherfucker.
Of course, the problem with being the first in his profession was that there were no such things as “enforcing copyright” or “not screwing over songwriters” back then. Today, Foster would have earned obscene amounts of money from “Oh! Susanna” alone, but in 1848, he got exactly $100 for the rights to publish the sheet music, while the publisher made $10,000 selling his work.
Even when Foster became a minor celebrity, he continued getting nothing but pennies for every copy of his work that was sold. For his dozens of hit songs, he saw around $15,000 in royalties in his whole life. In the 1860s, he was dumped by his wife, who had probably had enough of sticking around with this dude who wrote like a rock star, anddrank like a rock star, but was not rich like one. He died at the age of 37 after hitting his head on a washbasin, with around 40 cents in his pocket.
Some of which were melted down to make this statue.
His contributions can’t be overstated. Not only did he create most of the conventions of popular songwriting as we know them today, but he also demonstrated the need for intellectual property laws by getting repeatedly screwed.
#1. Gary Kildall, the Father of the Operating System
Gary Kildall is one of the guys we have to thank for the fact that you don’t need to be a genius to use the ultra advanced computer you are looking at right now to search for porn. Thank you, Gary.
In 1973, Kildall made life a lot easier for nerds everywhere when he created CP/M, a groundbreaking operating system for microcomputers (which is what they called any computer smaller than a semi truck back then). The program became the industry standard for the next decade. This guy was basically Bill Gates before Bill Gates was Bill Gates.
Michael Ochs Archives / Getty
“It’s cool, I’ll just donate a bunch of money to charity someday when I’m all old and prune-faced.”
But Then He Got Screwed
Of course, at the same time, Bill Gates was busy trying to become Bill Gates, and he eventually achieved that at Kildall’s expense.
In 1980, IBM was getting ready to launch its first personal computer and needed an operating system to operate the shit out of it. They first knocked on Microsoft’s door, but Microsoft wasn’t really into the OS-making business at that point, so they directed the IBM suits to Gary Kildall’s company. However, as nerd lore has it, Gary picked that day to go flying (he was an amateur pilot), blowing off IBM and his chance at history.
Accounts differ on whether Kildall met the IBM suits that day or not, but either way, the company went back to Microsoft, totally forgetting the whole “We don’t make OS’s here” part. Not one to miss out on an opportunity, Bill Gates turned to local programmer Tim Paterson, who had built a CP/M clone he called QDOS (for “Quick and Dirty Operating System”), bought it for a paltry 50 grand, then turned around and sold it to IBM under the name PC-DOS.
The term “user-friendly” meant something very different back then.
PC-DOS, later renamed MS-DOS, was included in every computer IBM made, and, long story short, that’s why roughly 90 percent of you are using Microsoft Windows right now.
Today, Kildall’s name is barely known, while Bill Gates will be a household name in the fucking 25th century. Most of Kildall’s innovations ended up being credited to other people — and he can’t even defend himself, having died in 1994 after falling down in a tavern, which pretty much just seems like his luck.
Today’s lesson is, if you’re an inventor, wear a freaking helmet.
Karl Smallwood wrote a book (yes, a real one), which you can read all about here. If you want to read words he’s written for free, feel free to follow him on Twitter. Mike Floorwalker has a website that’s like … whoa. Like, seriously, dude … whoa.
Robert William Kearns (March 10, 1927 – February 9, 2005) was an American inventor who invented the intermittent windshield wiper systems used on most automobiles from 1969 to the present. His first patent for the invention was filed on December 1, 1964.
Kearns won one of the best known patent infringement cases against Ford Motor Company (1978–1990) and a case against Chrysler Corporation (1982–1992). Having invented and patented the intermittent windshield wiper mechanism, which was useful in light rain or mist, he tried to interest the “Big Three” auto makers in licensing the technology.
But then he got screwed.
They all rejected his proposal, yet copied his idea and began to install intermittent wipers in their cars, beginning in 1969. march Abraham made the film: ” Flash of Genius” about him.
Preston Tucker was a car-crazy kid who hung around auto speedways and grew up to create an automobile–the Tucker–that was years ahead of its time. He was a man of pioneering spirit, ingenuity and daring, who revolutionized Detroit in the 1940s with his stunning “Car of Tomorrow.” It was streamlined, futuristic and fast–the car every American dreamed of owning, at a price most people could afford.
A man of endless enthusiasm, Tucker publicized his model all over the country to wild acclaim. He sold stock, set up a factory . . .
But then he got screwed.
…and then the auto industry launched a devastating anti-Tucker campaign in order to character assasinate, industrially spy on and sabotage his car. Francis Ford Coppola made a movie: “The Man and His Dream” about him.
Nikola Tesla helped established robotics, radar, remote control, and he helped expand ballistics, nuclear physics, and theoretical physics.
But then he got screwed.
Practically no one’s heard of him. Why? Because of a man named Thomas Edison, who is widely credited with the invention of the light bulb. Edison was an all-around pretentious ass, who totally tried to steal Tesla’s credit… which kinda worked, considering everyone remembers him and not Tesla.
Anyway, the two men had initially worked together — well, Tesla worked for Edison –and this is where Tesla was first screwed over by the man. Edison had offered $50,000 — over a million bucks, adjusted for inflation — to someone who could fix his crappy and inefficient motors. When Tesla did (probably by staring them down until they worked harder), Edison wrote his deal off as a joke, and continued to pay Tesla $18 per week. Keep in mind, Tesla was one of the most brilliant humans to have ever lived; it didn’t take long for him to flip Edison the bird and get his ass outta there to start his own company.
Soon enough, Edison’s electricity, direct current (DC) was competing with Tesla’s far superior electricity, alternating current (AC). Edison actually tried to discredit Tesla’s AC by having the first electric chair run on it; this was supposed to discourage people from putting it in their home. There are a few movies based on Nikola, one is: “The Prestige”.
Professional character assassins will create fake business accounts at, or bribe the staff of:
TalentShield
BeenVErified
GIS BackGround Checks
CVCertify
Social Intelligence
Dun And Bradstreet
EquiFax
Infortal
Kroll Backgrounds
Onesource
Checkpeople
…and numerous other database companies and input nasty lies, misrepresenations and red flag data in order to prevent you from ever getting hired again. This is a felony, though, and if you can find more than two cases of false input you have the start of good evidence for an arrest and to win a lawsuit. Search, find the bad data and file city, state and federal police reports and charges on those who did it to you. If any of your employers got a call from one of the attackers providing false information in an attempt to get you fired, or layed off, as we all now know, every communication in the world has been tracked for the last 10 years so it will be easy to catch them, now, with a subpoena.
Extreme Attack Techniques are Deployed by Corporations, Investor Groups and Political Groups as shown in the documentation at link below:
How Washington DC Politicos Have Reporters “HIT” and Intimidated!
Character assassination From Wikipedia, the free encyclopedia
This article relies largely or entirely upon a single source. Relevant discussion may be found on the talk page. Please help improve this article by introducing citations to additional sources. (December 2011)Character assassination is a deliberate and sustained process that aims to destroy the credibility and reputation of a person, institution, social group, or nation.[1]
Agents of character assassinations employ a mix of open and covert methods to achieve their goals, such as raising false accusations, planting and fostering rumours, and manipulating information.
Character assassination is an attempt to tarnish a person’s reputation. It may involve exaggeration, misleading half-truths, or manipulation of facts to present an untrue picture of the targeted person. It is a form of defamation and can be a form of ad hominem argument.
For living individuals targeted by character assassination attempts, this may result in being rejected by his community, family, or members of his or her living or work environment. Such acts are often difficult to reverse or rectify, and the process is likened to a literal assassination of a human life. The damage sustained can last a lifetime or, for historical figures, for many centuries after their death.
In practice, character assassination may involve doublespeak, spreading of rumours, innuendo or deliberate misinformation on topics relating to the subject’s morals, integrity, and reputation. It may involve spinning information that is technically true, but that is presented in a misleading manner or is presented without the necessary context. For example, it might be said that a person refused to pay any income tax during a specific year, without saying that no tax was actually owed due to the person having no income that year, or that a person was sacked from a firm, even though he may have been made redundant through no fault of his own, rather than being terminated for cause.
Contents [hide]
In politics[edit]In politics, perhaps the most common form of character assassination is the spread of allegations that a candidate is a liar. Other common themes may include allegations that the candidate is a bad or unpopular member of his family, has a bad relationship with his spouse or children or is not respected by his colleagues. Another theme claims that the person routinely engages in disturbing, socially unacceptable behavior, such as sexual deviancy. The person may also be portrayed as holding beliefs widely considered despicable within society, such as supporting racismor other forms of bigotry.
Charging an opponent with character assassination may have political benefits. In the hearings for Clarence Thomas’ nomination to the Supreme Court of the United States, supporters claimed that both Clarence Thomas and Anita Hill were victims of character assassination.[2]
The International Society for the Study of Character Assassination (ISSCA) specializes in the academic study and research of how character attacks and assassinations have been executed in both history and during contemporary times.[3]
Character assassination in a totalitarian regime[edit]The effect of a character assassination driven by an individual is not equal to that of a state-driven campaign. The state-sponsored destruction of reputations, fostered by political propaganda and cultural mechanisms, can have more far-reaching consequences. One of the earliest signs of a society’s compliance to loosening the reins on the perpetration of crimes (and even massacres) with total impunity is when a government favors or directly encourages a campaign aimed at destroying the dignity and reputation of its adversaries, and the public accepts its allegations without question. The mobilisation toward ruining the reputation of adversaries is the prelude to the mobilisation of violence in order to annihilate them. Official dehumanisation has always preceded the physical assault of the victims.[1]
See also[edit]
- Mudslinging
- Black propaganda
- Fair Game (Scientology)
- Pittura infamante
- McCarthyism
- Hollywood blacklist
- Damnatio memoriae
- Smear campaign
- Personal attack
References[edit]
- ^ Jump up to:a b Rojas, Rafael: Blanco, Juan Antonio; de Aragon, Uva; Montaner, Carlos Alberto; Faya, Ana Julia; Lupi, Gordiano (2012). Ready, Aim, Fire! Character Assassination in Cuba. Miami: Eriginal Books. p. 12. ISBN 978-1-61370-974-0.
- Jump up^ Walkowitz, Rebecca L.; Garber, Marjorie B.; Matlock, Jann (1993). Media spectacles. New York: Routledge. p. 32. ISBN 0-415-90751-9.
- Jump up^ http://characterattack.files.wordpress.com/
Readings involving character assassination in the modern period:
- Benz, Wolfgang, Feindbild und Vorurteil (München 1996)
- Fiebig-von Hase, Ragnhild & Ursula Lehmkuhl (eds.), Enemy Images in American History (Providence – Oxford 1997)
- Frei, Daniel, Feindbilder und Abrüstung. Die gegenseitige Einschätzung der UdSSR und der USA (Munich 1985)
- Goldstein, Robert Justin, Censorship of Political Caricature in Nineteenth-Century France (Kent, Ohio 1989)
- Hahn, Hans Henning (ed.), Historische Stereotypenforschung. Methodische Überlegungen und empirische Befunde (Oldenburg 1995)
- Hahn, Hans Henning (ed.), Nationale Wahrnehmungen und ihre Stereotypisierung (Frankfurt am Main 2007)
- Halfin, Yigal, Intimate Enemies: Demonizing the Bolshevik Opposition, 1918-1928 (Pittsburgh 2007)
- Hannover, Heinrich, Politische Diffamierung der Opposition im freiheitlich-demokratischen Rechtsstaat(Dortmund 1962)
- Neu, Jerome, Sticks and Stones: The Philosophy of Insults (Oxford – New York 2008)
- Jeismann, Michael, Das Vaterland der Feinde. Studien zum nationalen Feindbegriff und Selbstverständnis in Deutschland und Frankreich 1792 – 1918 (Stuttgart 1992)
- Keen, Sam, Faces of the Enemy (1986)
- Plum, Angelika, Die Karikatur im Spannungsfeld von Kunstgeschichte und Politikwissenschaft. Eine ikonologische Untersuchung zu Feindbildern in Karikaturen (Aachen 1998)
- Reichardt, Sven, ‘Feindbild und Fremdheit – Bemerkungen zu ihrer Wirkung, Bedeutung und Handlungsmacht’, in: Benjamin Ziemann (ed.), Perspektiven der Historischen Friedensforschung (Essen 2002) 250-271
- Satjukow, Silke & Rainer Gries (eds.), Unsere Feinde. Konstruktionen des Anderen im Sozialismus (Leipzig 2004)
- Schultz, Cindy & S. Mark Pancer, ‘Character attacks and their effects on perceptions of male and female political candidates’, Political Psychology 18-1 (1997) 93-102
- Walton, Douglas, Media Argumentation: Dialectic, Persuasion, and Rhetoric (Cambridge 2007)
- Bargh, J. A. (1997). The automaticity of everyday life. In R. S. Wyer Jr. (Ed.), The automaticity of everyday life:Advances in Social Cognition, vol. 10 (pp. 1-61). Mahwah, NJ: Erlbaum.
- Davis, Jerome (1950) Character Assassination . New York: Philosophical Library,1950
- Davis, Michael L., and Michael Ferrantino (1996). Towards a positive theory of political rhetoric:
- Why do politicians lie? Public Choice 88: 1-13.
- DeFrank, Thomas (2007). Write it when I am gone. Putnam Adult
- Dolan, Kathleen and Holbrook, Thomas M. (2001). Knowing versus Caring: The Role of Affect and Cognition in Political Perceptions Kathleen Source: Political Psychology, Vol. 22, No. 1, pp. 27-44
- Bloch, S., Reddaway, P. (1977) Psychiatric Terror: How Soviet Psychiatry Is Used to Suppress Dissent. New York, Basic Books, 1977.
- Davidson J.R, Connor K.M., Swartz M. (2006). Mental Illness in U.S. Presidents between 1776 and 1974: a review of biographical sources. The Journal of nervous and mental disease. January, 1941: 47-51.
- Doron, Gideon, and Uri On (1983). A rational choice model of campaign strategy. In Asher
- Arian, ed., The Elections in Israel, 1981. Tel Aviv: Ramot Publishing.
- Frank, Justin (2007). Bush on the Couch Rev Ed: Inside the Mind of the President. NY: Harper
- Fraser, Steven (1993). Labor Will Rule: Sidney Hillman and the Rise of American Labor, Ithaca: Cornell University Press.
- Kinder, D. R. (1986). Presidential character revisited. In R. R. Lau & D. O. Sears (Eds.), Political Cognition (pp. 233-255). Hillsdale, NJ: Erlbaum.
- LeDoux, J. E. (2000). Emotion circuits in the brain. In Annual Reviews Neuroscience (Vol. 23, pp. 155–184). Palo Alto: Annual Reviews
- Levy, Paul (2006). The Madness of George W. Bush: A Reflection of Our Collective Psychosis. Authorhouse.
- Lodge, M., and Steenbergen, M. (1995). The responsive voter: Campaign information and the dynamics of candidate evaluation. American Political Science Review, 89, 309-326.
- Marcus, George E.; Sullivan, John L.; Theiss-Morse, Elizabeth; Stevens, Daniel. (2005). The Emotional Foundation of Political Cognition: The Impact of Extrinsic Anxiety on the Formation of Political Tolerance Judgments. By: Political Psychology, Vol. 26 Issue 6, p949-963,
- Mathews, Nieves (1996). Francis Bacon: The History of a Character Assassination. New Haven, CT: Yale University Press
- McGraw, Kathleen M., Edward Hasecke, Kimberly Conger (2003). Ambivalence, Uncertainty, and Processes of Candidate Evaluation Author(s): Source: Political Psychology, Vol. 24, No. 3, pp. 421-448
- Morris, James P., Nancy K. Squires, Charles S. Taber, Milton Lodge (2003). Activation of Political Attitudes: A Psychophysiological Examination of the Hot Cognition Hypothesis Source: Political Psychology, Vol. 24, No. 4, Special Issue: Neuroscientific Contributions to Political Psychology, Vol 24., Dec., pp. 727-745
- Munro Robin. (2000). Judicial psychiatry in China and its political abuses. Columbia Journal of Asian Law 14:1-125
- Pierce, Patrick A. (1993) Political Sophistication and the Use of Candidate Traits in Candidate Evaluation.Political Psychology, Vol. 14, No. 1, (Mar., 1993), pp. 21-35
- Pancer, S. Mark, Steven D. Brown, Cathy Widdis Barr (1999). Forming Impressions of Political Leaders: A Cross-National Comparison. Political Psychology, Vol. 20, No. 2, (Jun., 1999), pp. 345-368
- Riker, William H. (1996). The Strategy of Rhetoric: Campaigning for the American Constitution.
- New Haven, CT: Yale University Press.
- Shlapentokh, Vladimir. (1986). Soviet Public Opinion and Ideology. New York: Praeger.
- Schultz, Cindy and Pancer, S. Mark (1997) Character Attacks and Their Effects on Perceptions of Male and Female Political Candidates Author(s): Source: Political Psychology, Vol. 18, No. 1, (Mar., 1997), pp. 93-102
- Sigelman, Lee and Mark Kugler Source. Why Is Research on the Effects of Negative Campaigning so Inconclusive? Understanding Citizens’ Perceptions of Negativity (2003). The Journal of Politics, Vol. 65, No. 1, pp. 142-160
- Simonton, Dean (2006). Presidential IQ openness, Intellectual Brilliance, and Leadership: Estimates and Correlations for 42 U.S. Chief Executives. Political Psychology. 27, 4, 511-526.
- Skaperdas, Stergios, and Bernard Grofman (1995). Modeling negative campaigning. American Political Science Review 89: 49-61.
- Soviet Archives at Info-Russ collected by Vladimir Bukovsky, prepared for electronic publishing by Julia Zaks and Leonid Chernikhov http://psi.ece.jhu.edu/~kaplan/IRUSS/BUK/GBARC/buk.html
- Zaller, J. R., & Feldman, S. (1992). A simple theory of the survey response: Answering questions versus revealing preferences. American Journal of Political Science, 36, 579-616.
- Psychiatric archive: http://psi.ece.jhu.edu/~kaplan/IRUSS/BUK/GBARC/pdfs/psychiat/psy-eng.html
Tabloids
Tabloids are trashy, unethical publications which make money off publishing made-up stories about celebrities and people in the news.
One of the more horrific aspects of tabloids is that almost every one of them hires a group of spies to break into the personal information of people in order to try to find out information which can be manipulated by their editors into salacious, malicious and artificial news about a person.
The ACLU, various investigations and main stream media have reported that these tabloid spies can, and do, break into anything that is electronic. It is extremely easy for them to break into devices. In many cases it only takes them a few clicks on commercially available black market software to enter your most personal data repositories. So far, little has been done to criminally prosecute these tabloids for their information theft. The things that tabloid spies can currently break into that expose your life, as reported in many published articles are:
“Any “smart device”; any “smart reader” output; toll bridge fastraks; Google; Twitter, Facebook, Netflix, Your GPS; ANY social media; any email system; your ATM; ANY bluetooth connection; your contact list on your phone or computer; your dating sites; public cameras, ANY cell phone, tablet or computer web camera can monitor even when you think it is turned off; any security camera; medical records; Youtube; Comcast,; Xfinity; ANY server; ANY router; ANY flash media; Fastrak; Any Java software; There are RFID tracking chips in many auto tires, RFID in your wallet; RFID in many product containers in Safeway; ANY network appliance; Almost any motherboard with AMD or Intel chips; ANY wireless network system in your car, ie: Onstar, Siri, Sync, etc.; ANY GPS data flow including controlling your GPS; ANY cell phone tower; Most browsers; Any lottery or contest entry; ANY credit card transaction…”
Is this legal? No! Are tabloids doing this? Yes, almost with impunity.
There are a number of quite awful feature news stories, every day, about tabloid editors who contract spies to engage in horrendous crimes, ie: The vast tabloid phone spying scheme in England which had a number of senior people arrested (Yet the same people and techniques still being used in America have, as yet, gone unprosecuted); the tabloid that broke into a dead girls voicemail in England in violation of her families mourning; The tabloid in Los Angeles that offers rewards for breaking into movie star’s voicemails; The New York tabloid that offered rewards for tracking the physical spying of stars; the list of transgressions numbers in the tens of thousands. Vast numbers of child suicides have now been attributed to tabloid-based harassment of fragile children caught in the crossfire. Children who are victims of trauma, who might otherwise not take their lives, are now at greater-than-ever risk because of tabloid harassment .
What can you do?
Create petitions and campaigns and take them to your state attorney general and all of the federal agencies and demand laws to outlaw tabloid spies! Demand that the tabloids off-shore funds are reviewed and accounted for and their secret payments to break-in experts are disclosed and their tax evasion techniques for these slush-funds are shut down. The feds have every illegal communication, for the last 8 years+, between tabloid editors, writers and break-in technicians but they need a legal demand by a state or federal attorney in order to prosecute using that data. Give them the reason they need.
Don’t let your friends buy tabloids. Contact the advertisers of each tabloid that engages in such actions. Don’t use any connected electronics unless they are essential and you are practicing good security hygiene with them. Check to see if you have been spied on by a tabloid.
After suicide of girl who was bullied online, David Cameron calls for boycott
Read more at: http://www.firstpost.com/world/after-suicide-of-girl-who-was-bullied-online-david-cameron-calls-for-boycott-1021373.html
London: British Prime Minister David Cameron today urged Internet users to boycott certain social networking sites, after a teenage girl who was bullied online committed suicide. Cameron described the death of 14-year-old Hannah Smith, who hanged herself last week after receiving abuse on the website ask.fm, as “absolutely tragic”. He blasted “vile” websites that allow bullying to take place. “There’s something all of us can do as parents and as users of the Internet and that is not to use some of these vile sites,” Cameron told Sky News television. ”Boycott them, don’t go there, don’t join them.” Hannah’s father has called for the website to face murder or manslaughter charges. Cameron urged website operators to do more to stop them from being used as forums for bullying.
Severe penalties for slanderous retweets in China
English.news.cn 2013-09-09
BEIJING, Sept. 9 (Xinhua) — People who post slanderous comments online in China will face up to three years in prison if their statements are widely reposted, according to a judicial interpretation issued on Monday. The document, released by the Supreme People’s Court and the Supreme People’s Procuratorate, stipulates that people will face charges of defamation if online rumors they create are visited by 5,000 Internet users or retweeted for more than 500 times. In China, people committing the crime of defamation face up to three years in prison or deprivation of political rights. Cyber attacks have consequences.
Google and Spain battle over privacy rights
By Aimee Ortiz / February 27, 2013
Google has had problems when it comes to the right to privacy in Europe for years. In the latest suit, Google is locked in a legal battle with Spain over “the right to be forgotten.”
On Feb. 26, the Court of Justice of the European Union (CJEU) heard arguments in Google’s latest case. Spain’s Data Protection Agency has ruled that Google breached individuals’ right to be forgotten. As a result, the search engine giant was ordered to take down links or information that can be deemed as harmful to an individual. Google, stating that such an action would set a precedent, has taken the trial to the CJEU.
Internet Law- Another victory in the battle against cyber-bullies.
Cheerleader’s defamation verdict against thedirty.com is upheld
Posted Aug 13, 2013 By Debra Cassens Weiss
A federal judge has upheld a $338,000 defamation verdict against thedirty.com obtained by a former Cincinnati Bengals cheerleader.
U.S. District Judge William Bertelsman said the website and its founder weren’t protected from liability because they played a significant role in developing the content, the Associated Press reports in stories posted here and here. The federal Communications Decency Act protects website operators from liability for content posted by third parties.
Former cheerleader and school teacher Sarah Jones sued the website and its founder over online allegations that she had sex with every member of the Cincinnati Bengals and that her ex-husband had obtained two venereal diseases after cheating on her.
Bertelsman said the website founder, Hooman Karamian, “intentionally encourages illegal or actionable third-party postings to which he adds his own comments ratifying or adopting the posts.” Karamian uses the name Nik Richie.
How to tell if your computer has been broken into by tabloid hackers:
How to Know if You’ve Been Hacked (with Pictures) – wikiHow How to Know if You’ve Been Hacked. There are many ways to find out if yourhacked but some ways hackers get in are surprising. Symptoms of being hacked are: *If programs and files won’t work or open. *Deleted files that you didn’t delete….
wikihow.com/Know-if-You’ve-Been-Hacked
About.com Internet / Network Security – Help! I Think I’ve … An article on incident response when you think you’ve been hacked. how do you collect clues and evidence of your perpetrator- when they attacked? what they did? How do you restore your system and how do you protect yourself from future occurrences??
netsecurity.about.com/cs/disasterrecovery/a/aa061603.htm
How do I know if my computer has been hacked? Steps on how to determine if your computer has been hacked by a hacker.
computerhope.com/issues/ch001296.htm
Windows Forensics: Have I been Hacked? – Bleeping Computer Table of Contents. Introduction; Why would someone want to hack me? Creating your Computer Forensics Tool belt; How can I tell if I have been hacked?
bleepingcomputer.com/tutorials/have-i-been-hacked/
GeekDrop – How To Tell If Your Facebook Account Has Been Hacked How To Tell If Your Facebook Account Has Been Hacked Here’s one very good method to stay on top of your Facebook account, and get immediately alerted via email and SMS text message (if you choose to) if someone accesses your account. Setting this up is
geekdrop.com/content/how-to-tell-if-your-facebook-ac…
How to do you know if you have been hacked? – Yahoo! Answers Best Answer: yor files wouldn’t work. you will ahve deleted files which you didn’t delete. sometimes some ppl hack you from e-mail and change your passsword and your computer …
answers.yahoo.com/question/index?qid=20080131125513AACJTve
YouTube – How can you can tell if your computer has been … This video will show you how you can remove established ports
youtube.com/watch?v=WzerXAi3Uok
How to tell if your phone or mobile device has been hacked … I have had a few phone calls and meetings over the past week from people asking if I can look at their phone and tell them if their mobile device has been hacked.
grassiagroup.com/how-to-tell-if-your-phone-or-mobile-dev…
The primary tool in politics is the character assasination tactic. It builds up as the elections get closer. If you are not deeply disturbed by the following, then you might want to re-examine your awareness –
Below is how some campaign managers operate. This is actually how they think. This is used by ALL of the political parties. This is a widely distributed“Political Operative’s Hit List” of tactics that are in common use by campaigns today:
” Never mention the name of the opposing party. Refer to the Candidate by name, only, in order to minimize their status.”
” Turn every fact into a negative. Everything you discover about the official or person you are targeting must be massaged into something that is bad. Turn every aspect into something awful. All facts have two sides to the story, your job is to interprete the bad side and then make it sound as bad as possible.”
” The average American has the intellect of a child or an ape. They are easily persuaded by the loudest voice, the most colorful object and the generalized movement of masses without respect to logic or circumspection. They will watch endless hours of “reality television” as long as it depicts equally stupid people. They will watch toilet humor movies with frat house prank actors forever as long as the actors are as childish as the audience is. It is easy to brainwash them into buying a product, needing a needless service or doing something they otherwise might not naturally do. Their willingness to think and consider all sides of a thing is very limited. Use flash, avoid substance, never be specific about anything and you win the election every time.”
” Use only our internal newspaper wire service, it will send out a political clipsheet every week, to thousands of “thought leaders,” and cartoons, editorials, and articles to 200,000 newspapers. Rural newspapers are so desperate for copy that many will print whatever our Service sends them, including documents that are basically press releases disguised as editorials endorsing whatever political position we advance.”
” Pretend that you are the Voice of the People. Use radio ads, sponsored by a false-front group with the word “Citizens” or “taxpayers” in the name.”
” Attack, attack, attack. You can’t wage a defensive campaign and win!”
” Keep it simple. Rhyming is a good tactic for the majority. The low intellect voter’s love rhymes. Never explain anything. The more you have to explain the more difficult it is to win support.”
” Humans are insanely easy to brainwash. Say the same thing over and over again. We have to get a voter’s attention seven times per slogan to control their intentions. Anybody that hears the same thing seven times is programmed to it for life.”
” Subtlety is your enemy. Words that lean on the mind are no good. They must dent it. Simplify, simplify, simplify. A wall goes up when you try to make Mr. and Mrs. Average American Citizen work or think.”
” Find any idiotic grammar or geography mistake a person said and play it over and over until the public thinks that their mix-up of the name of a state was a call to eat babies. Make every mistake sound like a federal crime”
” Fan flames. A good political engineer needs more partisanship in this country to operate effectively. Never shy away from controversy; instead, win the controversy. The average American doesn’t want to be educated; he doesn’t want to improve his mind; he doesn’t even want to work, consciously, at being a good citizen, But there are two ways you can interest him in a campaign, and only two that we have ever found successful. You can put on a fight or you can put on a Show. So if you can’t fight, PUT ON A SHOW! And if you put on a good show, Mr. and Mrs. America will turn out to see it. ”
” Winner takes all. If you launch a campaign for a new car, your client doesn’t expect you to lead the field necessarily in the first year, or even the tenth year, But in politics, they don’t pay off for PLACE OR SHOW! You have to win, if you want to stay in business.”
” This must be a campaign that makes people hear the beat of drums and the thunder of bombs. . . . This must be A CALL TO ARMS IN DEFENSE AMERICA!, that, above all things, will distract from any bad economic report, sex scandal, or other distraction.”
” Never tell the candidate what you are really doing. Let them think it is all bread and roses but behind the scenes you must use knives and shotguns. If you fail, you lose your car, your girlfriend and your house. You must win the campaign at all costs. YOU DO NOT WORK FOR THE CANDIDATE. THEY ARE JUST THE FACE IN FRONT. YOU WORK FOR THE CANDIDATE’S BACKERS. YOU WORK FOR THE BIG DONATION PEOPLE. Never, ever, ever forget this or you will starve! Listen to what the candidate says, smile and nod your head and then go do what the backers want and make the candidate think he is getting what he wants.”
” Where the men go, the women will follow. Focus on male trigger slogans first.”
” Always, and only, use our prescreened 15 minute talking script. Try not to speak for more than fifteen minutes—people get bored—and never for more than half an hour.”
” Look at dating sites, find anybody the opposition may have dated, everybody someone broke up with has something bad to say about them.”
” Talk to all of their ex bosses and ex co-workers, one of them must have been jealous or mad about them in the past.”
” Reject any issues that affect our supporters ability to make money. Say often: You can’t beat something with nothing,” and: “Political XXXX is bad XXXXX. (Insert the topic of controversy in the XXXX position)”
” Lobby your local newspaper editors. Have your staff make in-person drop-by’s to every newspaper office to persuade editors to change their positions. Many of these newspapers do a vast amount of advertising business with us and received hundreds of words of free copy, each week, from our news services. They will not risk losing our advertising dollars when the internet is killing their business. We can cut out all of the newspapers supporting any given issue in 70 days if we stay on our goal. This is a top 6 issue and we now have the budget to spend 10 dollars against every individual dollar the opposing campaign spends to push it.”
” Use Germany! In private conversations with Senators, use this talking point:“Please vote against all Compulsory XXXX Bills pending before the Legislature. We have enough regimentation in this country now. Certainly we don’t want to be forced to go to “A State XXXXX service,” or to pay for such a service whether we use it or not. That system was born in Nazi Germany—and is part and parcel of what our boys are fighting overseas to stop. Let’s not adopt it here.”
” This must be a campaign to arouse and alert the American people in every walk of life, until it generates a great public crusade and a fundamental fight for freedom, any other plan of action, in view of the drift toward socialization and despotism all over the world, would invite disaster.”
” The great need is to go on the offensive—and to attack, Best to forget anybody who wouldn’t vote for you even if you got the personal endorsement of every saint in heave.”
” Politics is just like show business. . . . You begin with a hell of an opening, you coast for a while, and you end with a hell of a closing.”
” The public is basically lazy, basically uninterested in making an effort to understand what we’re talking about, Reason requires a higher degree of discipline, of concentration; impression is easier, Reason pushes the viewer back, it assaults him, it demands that he agree or disagree; impression can envelop him, invite him in, without making an intellectual demand. . . . When we argue with him we demand that he make the effort of replying. We seek to engage his intellect, and for most people this is the most difficult work of all. The
emotions are more easily roused, closer to the surface, more malleable. Voters are, simply, idiots. Treat them as such and keep them amused by the shiny object.”
The above is a sample of the way political campaigns think and operate. Is this ethical?
Professional character assassins will create fake business accounts at, or bribe the staff of:
TalentShield
BeenVErified
GIS BackGround Checks
CVCertify
Social Intelligence
Dun And Bradstreet
EquiFax
Infortal
Kroll Backgrounds
Onesource
Checkpeople
…and numerous other database companies and input nasty lies, misrepresenations and red flag data in order to prevent you from ever getting hired again. This is a felony, though, and if you can find more than two cases of false input you have the start of good evidence for an arrest and to win a lawsuit. Search, find the bad data and file city, state and federal police reports and charges on those who did it to you. If any of your employers got a call from one of the attackers providing false information in an attempt to get you fired, or layed off, as we all now know, every communication in the world has been tracked for the last 10 years so it will be easy to catch them, now, with a subpoena.
FROM RT Newspaper- 11/27/13
“We can discredit them’
Snowden’s revelation’s turned a spotlight on the NSA and its warehousing of billions of pieces of information – emails, phone calls, photos and videos. However, in its effort to find the proverbial needle in a haystack, the NSA is scooping up millions of innocent people in its dragnet.
However, in the never-ending fight against terrorism, proponents of the NSA’s eavesdropping techniques, which have spied on everything from the offices of the United Nations to the Vatican, maintain a position of security over privacy.
Stewart Baker, former general counsel for the NSA, supported the idea of practicing what essentially amounts to character assassination against individuals who are believed to pose a risk to US security interest.
“If people are engaged in trying to recruit folks to kill Americans and we can discredit them, we ought to,” Baker said, as quoted by HP. “[D]ropping the truth on them,” as opposed to a drone missile attack, for example, is “fairer and maybe more humane.”
Who’s next?
Although the NSA document only mentions Muslims on its list of targets, critics of the clandestine data mining system worry that such tactics could be used against ordinary Americans for any number of reasons.
“This kind of dragnet surveillance is precisely what the Fourth Amendment was meant to prohibit,” said ACLU Deputy Legal Director Jameel Jaffer, who presented arguments against the NSA surveillance in a US federal court last week.
“The Constitution does not permit the NSA to place hundreds of millions of innocent people under permanent surveillance because of the possibility that information about some tiny subset of them will become useful to an investigation in the future,” Jaffer added.
Jaffer said it is right to ask if a “president will ask the NSA to use the fruits of surveillance to discredit a political opponent, journalist or human rights activist.”
“The NSA has used its power that way in the past and it would be naïve to think it couldn’t use its power that way in the future,” he said.
None of the individuals listed in the NSA document, all of whom are believed to reside outside the United States, is accused of being involved in terror plots against US interests, the article concluded. ”
If you are targeted by adversaries, here are other tactics they may use against you. Watch out for them and report them. Process against them, legally, if you identify these actions:
- Calling your employer to anonymously report false negative information about you.
- Placing false and damaging information about you in job agency databases, credit agency reports and background check services which affect your ability to get jobs in a pattern that is inconsistent with your previous job history.
- Placing their people as plants in your company.
- Hacking your computer or voicemail to get information on you or your contacts.
- Inviting you to a TV interview and then jumping you with a surprise guest: your arch enemy with targeted attack comments in hand.
How Washington DC Politicos Have Troublemakers and Reporters “Killed”!
Option #1: “The Full Monty”- Honey Trap/Brand Kill/Career Hit/ De-Googling/Hacking- Details below:
Option #2: “Actual” Death- Details below:
Option #3: “The Come On”- Details below
Option #4: “The Poor Boy”- Details below:
Option #5: “The Honey Trap”- Details below:
Option #6: “The Hack and Block”- Details below:
Option #7: “The Molasses Tactic”- Details below:
Option #8:” Having You De-Googled”– Details Below:
————————————————————————–
Option #1: “The Full Monty”- Combined: Honey Trap/De-Googling/Brand Kill/Career Hit/Hacking, AKA “The Works” –
For the sake of argument let’s assume Silicon Valley and Washington DC are sort of the same thing…
Relationship Status: Call My Lawyer
As he built TechCrunch into a multi-million-dollar empire, blogger-investor Michael Arrington became a one-man nexus of power in Silicon Valley. Now he’s on the defensive, denying accusations that he raped an ex-girlfriend and abused two other women. Welcome to the dark side of the Information Age.
By Maximillian Potter
left, by John Keatley/Redux; right, by Tom Foremski.
HE POSTS, SHE POSTS Left: TechCrunch founder Michael Arrington in 2010. Right: Jennifer Allen, Arrington’s ex-girlfriend, in 2012.Several times a year, the Center for Entrepreneurship and Technology at the University of California, Berkeley, persuades a “Distinguished Innovator” to give an on-campus lecture. Speakers are a Who’s Who of Silicon Valley and in recent years have included such titans of tech as the C.E.O. of Yahoo, Marissa Mayer, then a V.P. at Google, who had been the company’s first female engineer, and Ben Horowitz, co-founder of the V.C. leviathan Andreessen Horowitz, where he manages a multi-billion-dollar portfolio that has included Facebook, Skype, and Twitter. In September 2010 the Distinguished Innovator was someone Timemagazine had named one of the world’s 100 most influential people, along with President Obama, Rupert Murdoch, and the Dalai Lama: Michael Arrington, the founder of TechCrunch, the Web site of record for all of Silicon Valley’s deals, developments, and dubious ethics. The format of Arrington’s lecture was an interview conducted by Vivek Wadhwa, a scholar who focuses his research on the dearth of women in tech.
Arrington has the doughy physique of an N.F.L. lineman past his prime and the untucked style of a frat-house social chairman. Onstage that day, he sat with his shoulders slumped, legs outstretched, bags under his eyes. Then 40, he was dressed in khakis and a blue button-down oxford. Wadhwa began by asking him to share a bit of his biography. Anyone else would have recognized the question as a chance to charm the crowd.
Arrington said he had attended Berkeley his freshman year but transferred to Claremont McKenna College because he “didn’t love having classes of 900 people” at Berkeley. The audience grumbled, but let the dig pass. Then Arrington said he got his law degree from Stanford University, adding, “Clearly the best school in California,” and the crowd let loose a barrage of rhetorical tomatoes. Wadhwa, a round, bearded Indian-American with a gentle way about him, turned to the audience, grinned, and, in a tone of for-those-of-you-who-don’t-know, said, “Mike has a habit of doing that—pissing off half of the world in one fell swoop.”
Crunch. That’s what Arrington is known for. From a rented house in Silicon Valley, he built a media-tech-venture-capital Empire of Crunch. First, the TechCrunch blog. Then its spin-offs, like CrunchBase—a database for investors and entrepreneurs—and the globally influential TechCrunch conferences, including its most famous, Disrupt. The very month Arrington was on that Berkeley stage, AOL was in the midst of paying him some $30 million to acquire TechCrunch.
Crunch has not only been Arrington’s brand, it has been his M.O. Mess with Arrington and you get crunched. He’s provoked personalities ranging from Hollywood star and venture capitalist Ashton Kutcher to former Yahoo C.E.O. Carol Bartz into telling him—to his face, mind you—to “fuck off.” Even Arrington’s colleagues who respect him say he is inclined to volatile mood swings. He’ll scream, he’ll shout. Sarah Lacy, one of Arrington’s former employees, says, “The worst place to be is between Michael Arrington and something he wants.” In Arrington’s honor, someone went as far as to create a Web site: ismikearringtonadick.com.
“Let’s talk about women,” Wadhwa said. The topic was inevitable. The Wall Street Journal had published a column bemoaning the lack of women in tech in which TechCrunch was mentioned because its conferences featured too few women. Arrington had responded with a column of his own, titled, “Too Few Women in Tech? Stop Blaming the Men.” He elaborated to Wadhwa, saying, “Women in my world are respected as much as men.” He pointed out that the C.E.O. of TechCrunch was a woman, as were almost half of his employees.
Arrington then called on a woman in the audience. He identified her as his girlfriend, Jenn. He asked her to please stand. Arrington explained that Jenn had just started a company, Rtist, a Web-based broker of original art. He said Jenn had hired a team and launched the Web site, and it was doing well. Looking in her direction, he asked, “Have you ever felt like, Wow, I feel like I’d be doing better if I was a man?”
Without pause, her soft voice infused with defiance, Jenn responded, “Not yet.”
Arrington shifted in his chair, and, after a few moments, launched into a soliloquy.
“If we want to get beyond this whole I’m-cool-because-I-care-about-women thing, what we really need to do is we have to start encouraging women to get engineering degrees in college. We have to start encouraging women to get into math and science early on in life. . . . But to just say TechCrunch is perpetuating the problem because there aren’t enough women speakers at our events is just a way to get attention and not solve the problem. So do we want to solve the problem or do we want to just pick on me?”
That Berkeley moment now seems astonishingly surreal, as Arrington has been accused not only of sexual assault but also of rape. In other words, the de facto king of Silicon Valley, who has insisted that the tech industry is a non-discriminating meritocracy, stands accused of misogynistic crimes—with the allegations coming not through a lawsuit or criminal charge but from a series of public accusations on social media. Arrington has sued the alleged victim for defamation. The source of these allegations? Jenn Allen, his ex-girlfriend, whom Arrington called on that day to help him make his case that he and the Valley culture he has been so instrumental in creating treat women fairly.
It was while working in the Valley as a young associate at the law firm Wilson Sonsini Goodrich & Rosati that Arrington realized he didn’t want to be an attorney pushing the paperwork for done deals; rather, the only child of a Bank of America data-processing executive and a stay-at-home mom, Arrington decided he wanted to be the mover-shaker doing the deals. One of the firm’s clients hired Arrington away and gave him his chance, on one start-up and then another. By 2005 the Valley had just about wiped the popped bubble from its face. Eighty-five percent of eligible college kids were on something called Facebook; Google and Yahoo were on a buying spree, targeting acquisitions like the photo-sharing site Flickr. YouTube was in its infancy. Twitter had not yet tweeted. Over at Apple, Steve Jobs was at work on a secret project: creating a touch screen that might eliminate the need for a keyboard. Anything and everything once again seemed possible. V.C.’s were itching to invest. The Valley was like Churchill Downs on Derby Day: packed dense with flush gamblers wanting to lay bets—only, Arrington realized, there was no Racing Form.
His first official TechCrunch post was on June 11, 2005. Within a few months, Arrington was churning out kisses-and-cupcakes coverage on start-ups and news items big and small. He got the idea of throwing a business-warming party. He invited sources, friends, fans, subjects he covered, whatever you wanted to call them—such distinctions made no difference to him. He didn’t consider himself a journalist. He was a blogger. Before anything else, an entrepreneur. The party was a brilliant move. His first “Meetup” was in September 2005. About 20 people showed up in his backyard, in Atherton, for beer and burgers. One of his guests was Chad Hurley, the co-founder of YouTube.
One of the early BBQs had a corporate sponsor, Eurekster. That company’s marketing-and-development person, Jenn Allen, had approached Arrington with the idea. The party drew hundreds, all in all a cross section of the Valley: V.C.’s from the likes of Kleiner Perkins, Greystone Ventures, and Accel Partners; entrepreneurs and engineers; rich geeks, broke geeks; high-school dropouts and M.B.A.’s; publicists and marketers, who tended to be pretty girls, like Jenn Allen. Dark hair, striking eyes; and trite as it may sound, she exuded a sweetness. At least that’s what Arrington thought at the end of the night when they agreed to go on a date the following weekend. More Meetups followed and went later and later into the early morning. “These were proper parties,” says Arrington’s friend Nik Cubrilovic. The old-fashioned networking fed Arrington’s intel on high tech, and TechCrunch became a must-read. Its Web traffic and page views skyrocketed, and in no time it dominated all other tech blogs.
In October 2006, Arrington landed the scoop that changed everything. He reported a rumor that Google was going to acquire YouTube. The New York Times, The Wall Street Journal, other blogs, all did a double take. Just like that, Arrington had “journalistic” cred. What’s more, TechCrunch had so much clout that if Arrington wrote favorably about a start-up or product it was almost guaranteed venture-capital interest. Aspiring entrepreneurs literally banged on the door and windows of his ranch-house office. Venture capitalists wanted to stay in Arrington’s good graces. Arrington had become a one-man nexus of ego, money, and information in the Valley. A month after Arrington broke the Google-YouTube story, The Wall Street Journal ran a story headlined: TECHCRUNCH SITE MAKES ARRINGTON A POWER BROKER.
A week after exchanging numbers at the TechCrunch Meetup in 2005, Arrington and Allen went on their first date to the bar in the Ritz-Carlton in San Francisco. Allen ordered a bottle of Veuve Clicquot, Arrington a beer. He drank his beer. She drank a single glass of the champagne, and they decided to call it a night. Arrington picked up the tab. Before they left, Allen opened up the little leather folder with the signed bill inside, to make sure Arrington left a decent tip.
A relationship blossomed, or, perhaps, erupted. It was volatile throughout. On again and off again, from 2005 until at least 2010, when Arrington called on Allen at the Berkeley lecture. At an officially unofficial annual gathering of Silicon Valley players in Hawaii, called the Lobby, a friend of Arrington’s, Cyan Banister, says she spent a lot of time hanging out with Allen because Arrington was so busy being Arrington. Banister remembers Allen and Arrington constantly texting. “It was like a high-school relationship,” Banister told me. “I was surprised that this was the kind of girl Mike was interested in.”
Not long after Allen and Arrington started dating she was let go from her job at Eurekster, according to the company’s C.E.O., Steven Marder, who said Allen had been “dropping the ball.” From what Marder recalls, it got to a point where her colleagues were coming to him and saying that something had to be done because “she seemed a bit lost.” Allen declined numerous requests to comment for this story.
Arrington’s Meetups evolved into a traveling Silicon Valley Super Bowl trade show called “TechCrunch50.” At these days-long conferences in cities around the world, investors, entrepreneurs, marketers, publicists, and tech journalists gathered. Featured attractions were panel discussions, one-on-one interviews conducted by Arrington, who abrasively poked his subjects, and a contest called “Startup Battlefield,” which is pretty much just what it sounds like.
For the first three years of the conferences, Arrington’s partner in planning, hosting, and executing was Jason Calacanis, a serial entrepreneur with a track record of success and relentless self-promotion. It was Calacanis who persuaded Arrington that they should unite and launch TechCrunch50. They struck an agreement wherein they split the revenue 50-50. In 2007, Arrington hired Heather Harde away from Fox Interactive Media to be C.E.O., and she began to expand the TechCrunch conferences globally. As the TechCrunch brand grew, and its staff was doing much of the work in organizing, the terms of the deal with Calacanis were revisited. The negotiations became acrimonious and fell apart, as did the partnership with Calacanis. Soon TechCrunch50 was dead, and the newly christened TechCrunch Disrupt Conference was born.
In early 2010, Tim Armstrong, the C.E.O. and chairman of AOL, attended a Disrupt and asked if Arrington would be interested in selling TechCrunch. Within a matter of months there was a deal memo, finalized in September 2010. As part of the $30 million sale, Arrington would remain at TechCrunch, which he believed would retain editorial independence from AOL. A year later, in September 2011, Arrington launched CrunchFund, a V.C. firm. In other words, Arrington would be a major force in an industry in which he himself was now even more financially invested. AOL would invest $10 million in CrunchFund. At some point, Arrington added a disclaimer to his bio on TechCrunch: “Sometimes I have so many financial conflicts of interest that I can’t even keep them straight. So when you read what I write … understand that I’m conflicted. A lot.”
What Arrington was doing with CrunchFund was only more of what he had been doing all along: from virtually day one of TechCrunch he had been an active investor-player in the Valley. But in early 2011, AOL had bought the Huffington Post and made its founding owner-publisher-editor, Arianna Huffington, the editor in chief of all AOL content. Upon learning of Arrington’s CrunchFund side pursuit, Huffington demoted him. Within 48 hours, Arrington wrote a blog response to his demotion in which he demanded that Armstrong honor TechCrunch’s editorial independence or else sell TechCrunch back to him. According to a Forbes story, Huffington counter-demanded that Armstrong support her, as she wanted to “make an example of Arrington.” Huffington won, and Arrington got the boot.
Furious, Arrington did two things: He started his own blog, Uncrunched, and he helped one of his former TechCrunch editors, Sarah Lacy, launch her own tech blog, PandoDaily. CrunchFund invested $100,000, and, according to Lacy, Arrington agreed to write and work exclusively for her site in exchange for a seat on the board. Shortly thereafter, representatives of the new AOL TechCrunch reached out to Arrington. They wanted him back. Or at least back onstage. In the wake of his departure, TechCrunch had hemorrhaged many of its best-known staffers; the AOL TechCrunch team realized the main event, the lucrative Disrupt conference, needed Arrington’s master-of-ceremonies cachet, not to mention his own abrasive star power. According to AOL TechCrunch sources, Arrington got the sort of offer he couldn’t refuse, and agreed to sign on for the May 2012 Disrupt in New York. Lacy was furious and felt betrayed. She fired him. Six months later Arrington returned to TechCrunch as a writer.
TECHCRUNCH FOUNDER’S EX-GIRLFRIEND CLAIMS HE PHYSICALLY ABUSED HER. That was the headline on a story that broke last April 1 on the Web site Gawker. Under the headline, there was a picture of Arrington and Jenn Allen, both smiling, with a text overlay of the catchy pull-quote: “It hurts when you love someone and they threaten to murder you.”
When Heather Harde, Arrington’s friend and former TechCrunch C.E.O., saw it, she thought the post might be the site’s idea of an April Fools’ joke. The main source material in Gawker’s scoop by Adrian Chen was a Facebook status update. Three days earlier, from her mobile phone, Allen had posted this status update to her Facebook page:
Last post on someone i’m completely over. I’ve never been lonelier in my entire life. To all my friends who loved me for who I am—thank you. Power hungry people, I loved Michael Arrington for 8+ years starting when i implemented Eurekster search at the time on Techcrunch in 2006 and throughout the years i didn’t know he cheated on me multiple times, then tells people it was me immediately after he did it. It hurts when you love someone borderline and they can’t feel anything at all for you, and threaten to murder you if you told anyone about the physical abuse—all for keeping his reputation. The emotional abuse was equally bad. On a positive note, it can’t get any worse than this and I can’t get myself of [sic] this bed.
Neither Allen nor Arrington was quoted in the story. As Gawker reported, they “did not immediately respond to requests for comment.”
Within minutes, there were dozens of comments, well on the way to more than 100. It was in the comments section that the Allen-Arrington story escalated. Allen herself posted three times, something she confirmed in her response to Arrington’s lawsuit, accusing Arrington of even more despicable crimes. Posting under the name “JennNella,” she alleged that five months earlier he had raped a friend of hers, whom she did not name. Someone going by “DisgustedByJennAllen” claimed to know Arrington and wrote, “First you accuse the man of abusing you and now you accuse him of rape? Really Jenn? You are truly a disgusting human being and a disgrace to the thousands of women who actually HAVE suffered such horrific tragedies.” Switching to the handle “youreinthemovie,” Allen went further and accused Arrington of raping her: “He did rape me, on March 5 last year … ”
Opinion and judgment of Arrington and Allen spread like a World Wide Web virus.
On April 5, Gawker published a follow-up report. Nick Denton, the founder and owner of Gawker, tweeted a link to the story with this rather definitively phrased tease: “Two more women roughed up by Michael Arrington, the Silicon Valley kingmaker.” This second story, once again reported by Chen, unearthed a decade-old accusation of sexual abuse made by a former co-worker of Arrington’s at RealNames, a start-up he had worked at. (The company shut down in 2002.) And Chen offered a more recent allegation that Arrington had physically abused another former girlfriend, New York-based blogger Meghan Asha.
According to Gawker, the alleged Asha incident occurred on September 12, 2009. Asha had flown from New York City, where she lived, to San Francisco. As Gawker reported it, “This coincided with the start of the TechCrunch50, a Bay Area tech conference that Arrington organized with his former business partner Jason Calacanis.” Gawker reported the allegation that Arrington attacked Asha on the last night of the conference, throwing her against the wall in a hotel room.
The day after that report, on April 6, Asha not only issued a blanket denial of everything Chen had reported but also gave her statement to Arrington’s former home team of TechCrunch:
None of the claims made on my behalf over the past week are accurate. I’m not inclined to comment on my personal life, Mike and I remain friends. I’m focused on business and my career. I hope we can all get back to the business of building innovative companies in the spirit of what makes this industry great. I wish everyone well who is involved. I have no further comment on the matter.
As far as the incident with the co-worker, Gawker’s lone named source was Cecile DeSmet Sharp, who had been the director of human resources at RealNames.
Shortly after the story was posted, the former C.E.O. of RealNames, Keith Teare, also a co-founder of TechCrunch, posted a comment on Facebook: “Mike was indeed the subject of an accusation at RealNames. . . . An outside party was hired to conduct an investigation The investigation concluded that there was no behavior to answer for. Mike was never reprimanded in any way. Both parties asked for confidentiality and to date this has been honored.”
On April 7, Arrington responded to all the accusations in a—what else—Uncrunched blog post: “There have been some extremely serious and criminal allegations against me over the last week. All of the allegations are completely untrue.” He went on to say that he had hired a law firm to pursue legal action.
Six days after the second Gawker story, on April 11, Eric M. George, a Los Angeles–based attorney representing Arrington, sent a letter via e-mail and U.S. mail to Jennifer Allen. George demanded she retract her statements or Arrington would pursue litigation against her for making “false and defamatory statements that caused significant harm to his good name.” Along with the letter, George sent Allen a packet of material: e-mails, photos, text messages, and Facebook postings. In keeping with the digital media circus/virtual trial, Arrington published the materials on his Uncrunched blog.
Included was a document noting the date and location in San Francisco that Allen presented in her accusation where she claimed Arrington raped her on the evening of March 5, 2012. Arrington’s attorney offered as one of the “provable facts” that Arrington was in Washington, not San Francisco, at that time.
Furthermore, George alleged that Allen herself was out with friends late that very same evening, into the early morning. George’s Attachment A is a photo of Allen taken at 1:05 A.M. on March 6, which a friend of Allen’s had posted to Facebook. In the photo, Allen is standing in the center of four friends at a San Francisco bar. That photo has since been removed.
In the third of the three comments Allen had posted to Gawker following its first report, she wrote that the last time she had seen Arrington was March 5, the night of the alleged rape, and that since then she had attempted to contact him only once, to request that he return a painting. “In fact,” George alleged in his letter, “you attempted to repeatedly communicate with Michael—by telephone, text message and tweets.” The very day following the alleged rape, Allen e-mailed Arrington three photos of herself, according to George. In at least one, she appears to be lying on a bed, and wrote, “The others are showing too much to email. Maybe if you beg. :)”
George’s letter included several examples of messages that Allen had allegedly sent Arrington from late March through the late summer—weeks and months after the date she claimed he had raped her. The letter and accompanying materials were later included in the defamation suit filed by Arrington. George wrote that the communications “do not portray you as a victim of abuse or murder threats, but rather as a person who is distraught at a break up and angered that her ex-boyfriend entered into a new relationship.”
On March 22, for example, 17 days after the day on which she alleged that Arrington had raped her, Allen e-mailed Arrington asking him to invest in her business.
Then, on April 21, 2012, Allen wrote to Arrington that she was “feel[ing] betrayed and slighted by you and, wish I wasn’t alone since you decided to be with someone else so quickly. Not sure how I’m going to teach myself how to love and trust again.”
And on July 21, she wrote, “You, Mike, seem happy with the most boring fake personalitied [sic] person on the planet, who you treat the way I should have been treated. If you can’t treat me with respect publicly, still, then you fall into the selfish whorish male prostitute category that will always hurt me during and in the end. Hope you’re enjoying the weather.”
In August 2012, Allen tweeted at Arrington for all of the world to see: “Mike @arrington last chance to reconcile. I [sic] you’re not feeling what I’m feeling, with the same heart, than [sic] fuck you.”
George also included some earlier correspondence between Arrington and Allen. On May 18, 2011, just about two years before Allen made her rape claim, and less than a year before the alleged rape had occurred, she e-mailed Arrington to say, “I’m getting an abortion tomorrow. On my birthday. please don’t contact me ever again. I can’t imagine you care—but if you do—just keep flirting and fucking. and dating the … meghans of the world. anything that might help your image, to make yourself feel better. and then fake a relationship like you did with me to make your parents happy. have a nice life and fuck you.”
Three months later, according to the material included in Arrington’s suit, Arrington and Allen had the following text exchange:
Arrington: do you want to see me?
Allen: Im open to talking to you but i’m dating someone if that’s what you mean. I’m in a relationship. it’s “facebook official”—so I could meet you for coffee. somewhere or at your office. but please don’t be last minute if you still want to meet.
Arrington: I wanted to talk about this pregnancy. I never really understood if it was real or not. or if you were still pregnant. I’m assuming there’s no chance of that. I’m happy for you that you’re dating someone and can talk about it online. I know how much that means to you. If you aren’t pregnant with my child, then we don’t really have anything further to talk about. Be well.
Michael Arrington refused to speak to me on the record for this story. Jenn Allen ignored at least a half-dozen of my requests to be interviewed for this story. One morning, I rang the buzzer of her apartment building in San Francisco, and a nice landlady, Shirley, relayed to me a message from Allen that she had received my voice mails and e-mails. Shirley said, “When I told Allen you were here, that’s all she said; I don’t think she’s coming down to talk with you.”
Another address I found for Jenn Allen is that of her childhood home, where her parents still reside. The house is in a gorgeous, idyllic, old-money neighborhood of San Francisco. Allen’s father was a successful attorney. He’s now retired and, according to a neighbor, does Tai Chi in the park across the street from their home.
On the afternoon I knocked on the door, a modest white sedan was parked in the driveway; a sticker from Mills College, which is where Allen went to school, was in the rear window, faded it seemed, like anything resembling childhood innocence. It was hard not to imagine Jenn’s mom and dad driving their little girl off to school in that car.
After several knocks, Allen’s mother opened a window above me. I recognized her from a photo that Allen had posted online. It seems Allen documents a lot of her life on the Web. Including photos of her only sibling, a sister who is in an elite Ph.D. program, and who also politely declined to speak with me. Looking down at me from the window, Allen’s mother said, “My other daughter warned me you would probably try to contact me. We can’t talk to you.” In her eyes there was an exasperation, an anguish, an agony—a mother’s petition for mercy and privacy. I nodded and started down the steps to leave, and she closed the window.
On May 7, 2013, Michael Arrington filed suit against Allen, seeking damages for defamation. In her answer to Arrington’s complaint, filed in June, Allen did not retract her statements, though she did revise at least one major aspect of her allegation. She said that she had been mistaken when she said he had raped her on March 5. Later she would tweet that it actually happened on March 30.
According to her answer, Allen is represented by two law firms, one of them, Allred, Maroko & Goldberg, the firm headed by feminist superlawyer Gloria Allred, who herself was a victim of rape. To date, Allen has not filed a criminal charge against Arrington. Nor have the two other women. A trial has been set for next October.
More than two dozen sources I spoke with were quick to point out the intensity of the rivalry that existed between Michael Arrington and Valleywag, which is essentially a Gawker dedicated to Silicon Valley. Gawker’s Nick Denton launched Valleywag in 2006, shut it down in 2008, then relaunched it this year. Arrington had called Denton “evil” in the San Francisco Chronicle around the time Valleywag launched and “a total dick” in Portfolio in 2008, and he wrote a TechCrunch column that same year lambasting the site for being irresponsible: “Today I read all the sordid details about the alleged sexual encounter between a notable technology visionary and a woman who appears to be looking for as much publicity as possible. Where did I read it? On the Silicon Valley gossip blog Valleywag. The posts include private IM chats and various rumors, all designed to make the person mentioned look like as much of a fool as possible. That’s not new, of course. Valleywag is making a business out of digging into people’s personal lives and publishing it for all to see (me included, regularly).” (Denton didn’t respond to numerous requests for comment.)
In his column, published in March 2008, Arrington noted that a business executive had recently committed suicide after being written about in a blog (not owned by Denton), and then asked:
So how long will it be before Valleywag drives someone in our community to suicide? My fear is that it isn’t a matter of if it will happen, but when. Valleywag and Nick Denton, though, will likely look forward to the event, and the great traffic growth that will surely follow. There’s a market for this kind of content, obviously. And nothing can stop it except significant changes to our libel and defamation laws. That isn’t something I support. But the valley was a much nicer place to live and work before the days of Valleywag.”
There are just as many people in the Valley who would say it was a lot nicer place before the days of Arrington. The allegations lobbed at him are the result of the very same blog/social media/Silicon Valley “innovative journalism” that he himself has championed. In 2009, Arrington wrote a blog post on TechCrunch in defense of his site’s practice of publishing rumors as part of the process to get to the “absolute truth.” Digitally savvy journalists have academically dubbed this “process journalism.”
“Some people ask why we don’t just wait until we have the whole story before posting,” Arrington wrote. “The fact is that we sometimes can’t get to the end story without going through this process. . . . When a story is up and posted, it’s amazing how many people come out of the woodwork to give us additional information. . . . And readers love it. The only people who don’t like it are competitors who like to point out that a story was partially wrong, and that they got it right later. But the fact is that they didn’t even know there was a story to begin with. Our original post kicked off the process, and they, like us, started digging for the absolute truth.”
You might say process journalism was applied to the accusations against Arrington, and this sordid mess is the necessary by-product of a pursuit of the absolute truth. Regardless of the absolute truth of what Arrington did or did not do to Jenn Allen, the whole affair makes this much clear: while the Valley is busy incubating a lot of shiny new start-ups and promising innovations and social networks that generate all kinds of value propositions and tremendous revenue possibilities, behind the scenes of that eco-system there’s another part of the culture, where someone is always trying to screw somebody over, where it’s crunch or be crunched. The big question the luminaries of the Valley might want to ask themselves is the question Arrington himself posed that day at Berkeley: Does the Valley want to solve the problem, or does it want to pick on Mike?
—————————–
(G.H.- See More About GAWKER, HERE>>>)
(F- LAT- Payback’s a Bitch, VC’s)
(F- Daily Caller- The Silicon Valley VC’s are the DNC‘s bankroll. When they go, the DNC goes.)
(FGH- Here’s the problem with the Venture Capitalists character assassinating someone clever and entrepreneurial like Arrington. When you end someone’s life with a character attack you create a highly motivated enemy. They, and their friends, will come after you forever. When you do it to a publisher with lots of friends you double your pleasure/payback. When you do it to someone who is clever, a publisher and you do it on the internet where all of the other kids, adults, etc. who got attacked, themselves, can catch some affinity; you (VC/illuminati) pretty much shoot yourselves in the foot. Combine doing it to Greenwald, Assange, Arrington, Manning and the others at the same exact historical time-span and you are pretty much fucked, you VC’s. Good luck with a pissed off Arrington, Silicon Valley. You were better off with just a blabby Arrington. You should have let sleeping dogs sleep.)
(SD- The Arrington/D. McClure/R. Conway payback scheme will be Epic)
(GH-j- Elon Musk hit Martin Eberhard, and most of Musk’s enemies, with most of “The Full Monty” in order to force a settlement from him. According to his ex-wives and ex-girlfriends, he also threatened them with “trouble” if they didn’t accept a quick settlement, too as discussed HERE>>>)
(MA- Gawker is a stealth front for Jay Carney and Robert Gibbs in the WH Press Office. If it is too dirty for a WH press syndicate release they have Nick Denton do the hit on somebody (usually the GOP) and, in exchange, avoid looking at his overseas accounts)
(G- Per the quote in the article about waiting for “Valleywag to drive someone in the -Silicon Valley- community to suicide..” It Has!!! Silicon Valley Has Committed Suicide in Self-Disgust. Goodbye Silicon Valley and the Arrogant Hipsters and Douche Bag VC’s.
MARTIN EBERHARD, of Tesla, got the FULL MONTY.
———————————————————————————–
Crovitz: Silicon Valley‘s ‘Suicide Impulse’ – WSJ.comIn The Wall Street Journal, Information Age columnist Gordon Crovitz writes that the tech industry’s affection for Washington keeps growing—with Facebook …
online.wsj.com/ news/ articles/ SB10001424127887323539804578266290231304934 – View by Ixquick Proxy –Highlight
Suicide in Silicon Valley – ToobBox.comJul 14, 2013 … The recent suicides of Jody Sherman, Aaron Swartz and Ilya Zhitomirskiy are tragic but all too familiar stories. Some might also recall the …
http://www.toobbox.com/blog/suicide-in-silicon–valley/ – View by Ixquick Proxy– Highlight
The Story Of A Failed Startup And A Founder Driven To SuicideApr 4, 2013 … A few months ago, on Sunday, January 27, an entrepreneur named Jody Sherman had plans to see a movie with a friend. But that afternoon …
http://www.businessinsider.com/jody-sherman-ecomom-2013-4 – View by Ixquick Proxy – Highlight
(DFG- THISLINK has Arrington’s big blow-out disclosure on the VC’s.)
But once in awhile, Reporters win! See the Movie: “Big Boys Gone Bananas”:
————————————————————————————–
Option #2: “Actual” Death-
Known as “Wet-Work” and done by hired mercenaries, who mainstream news calls: “Contractors” (See George Clooney’s movie “Micheal Clayton”to see how it is done). Killing you dead with, formerly, untraceable creepy technology… Internet lore holds that Brietbart is thought to have been taken out this way.
…they can actually, ACTUALLY, kill you like THIS!>>> as shown in THESE ARTICLES
————————————————————————————–
Option #3: “The Come On”-
They ask to look at your technology, then steal it, then they say: “Ha! We are going to give it away, or just use it without paying you, to kill your market. What are you going to do about it, Sue us? Ha! Suckers…“
Except, …now you CAN sue them, and win!
.. they can sabotage your business like THIS!>>>
————————————————————————————–
Option #4: “The Poor Boy”-
Political operatives hack into, or pay friends to access, each of the career databases and credit reporting companies to falsely crash your background and credit checks so you can’t get a job. The companies they mostly use are:
TalentShield
BeenVErified
GIS BackGround Checks
CVCertify
Social Intelligence
Dun And Bradstreet
EquiFax
Infortal
Kroll Backgrounds
Onesource
Checkpeople
and others…
—————————————————————————————-
Option #5: “The Honey Trap”-
They send somebody to sleep with you, or charge you for sex, or get pregnant or all of the above and cause all kinds of hell in the media…
The creepiest Honey Trap system is the one we heard about at ProPublica where the owners of Match.com/OKCupid.com are closely connected to certainpolitical “interests”. A source claimed that they allow those interests to scan their database with photo-comparison software. If the dating profile picture you posted on Match.com or OkCupid is a match for a person the “interests” want to run a Honey Trap on, the “interests” send in a fake date person to try to get info from you or get you in a compromising situation. Very often the hot blonde you think you are writing to is some hairy fat male political operative in New Jersey. Both sites already have a number of legal actions for fake profiles. If true, and you are controversial, I suppose you can’t date anymore… bummer!
Ed- PP
—————————————————–
To see some of the HONEYS. CLICK HERE>>>
——————————————————-
Julian Assange in the Honey Trap by Justin Raimondo — Antiwar.comDec 8, 2010 … Anyone who doubts the unmitigated evil of the US government and its international enablers has only to look at the disgraceful persecution of …
original.antiwar.com/ justin/ 2010/ 12/ 07/ julian–assange-in-the-honey–trap/ –View by Ixquick Proxy – Highlight
We are Women Against Rape but we do not want JulianAssange …Aug 23, 2012 … WikiLeaks founder JulianAssange on the balcony of the … internet; they have been trashed, accused of setting a “honeytrap“, and seen their …
http://www.theguardian.com/ commentisfree/ 2012/ aug/ 23/ women-against-rape-julian–assange – View by Ixquick Proxy – Highlight
Was Assange Lured into ‘Honey Trap?’ – The TruthseekerFeb 27, 2013 … Eyewitnesses report “an astounding swarm of women” aroundJulianAssange. Lucky guy but the fact that they were journalists from …
http://www.thetruthseeker.co.uk/?p=66167 – View by Ixquick Proxy – Highlight
“CIA Honeytrap” Ardin Deleted Twitter Posts PraisingAssange Alex …Dec 10, 2010 … Anna Ardin, described in court documents as “Miss A,” had deleted Twitter messages speaking highly of Wikileaks founder JulianAssange, the …
http://www.infowars.com/ cia-honeytrap-ardin-deleted-twitter-posts-praising-assange/ – View by Ixquick Proxy – Highlight
IBA – IBA interview with Mark Stephens, lawyer forJulian Assange25.10mins: Stephens denies claims Assange has seen the full report of the sex allegations against him. 28.20mins: ‘The honey–trap has been sprung’ …
http://www.ibanet.org/ Article/ Detail.aspx?ArticleUid=160c30de-e4db-4837-a0fe-466c951a23f9 – View by Ixquick Proxy – Highlight
Was it a CIA honeytrap after all? – DaddysMar 17, 2011 … This information raises questions about CIA and ASIO (australian spy organisation), and whether the sexcharges against JulianAssange was …
http://www.daddys-sverige.com/ 3/ post/ 2011/ 03/ was-it-a-cia-honeytrap-after-all.html – View by Ixquick Proxy – Highlight
Was Anna Ardin a “CIA Honeytrap”? | Operation ProtestDec 16, 2010 … In computer terminology, a honeytrap or honeypotis a trap set to detect, … seen the proof says JulianAssange‘s lawyer” Source: dailymail.co.uk …
Commentary: Sex is Russian ‘honey trap‘ for spies – The Santa Fe …Jul 19, 2013 … And in a briefing at the International Spy Museum in Washington, D.C., recently, Melton spilled some of sexpionage’s greatest secrets.
http://www.santafenewmexican.com/ opinion/ commentary/ article_384c8f16-b025-5767-8744-5f8bdebc0e68.html – View by Ixquick Proxy – Highlight
VAWA And Variants On The “Honey Trap” by Charles E. Corry, Ph.D.Jul 28, 2012 … In popular fiction a “honeytrap” usually implies a woman entrapping … Reston, Virginia and other installations near Washington, D.C., among …
http://www.ejfi.org/DV/dv-34.htm – View by Ixquick Proxy – Highlight
Honey Trap: Dozens of G20 Diplomats Get Hacked After They Click …HoneyTrap: Dozens of G20 Diplomats Get Hacked After They Click on a Link … elites in WashingtonDC are competent super-managers of sterling character …
Russian spy Anna Chapman was luring U.S. cabinet member into …Apr 3, 2012… of President Obama’s inner circle in a seduction “honeytrap” when FBI … born at the Smithsonian’s National Zoo in Washington D.C. on Aug.
http://www.nydailynews.com/ news/ national/ russian-spy-anna-chapman-luring-u-s-cabinet-member-sexy-honey–trap-re port-article-1.1055088 – View by Ixquick Proxy – Highlight
Should You Set Up a Honey Trap? – Catching a Cheating SpouseWhat is a honeytrap? Simply, a honeytrap (sometimes called a honey pottrap) is a kind of “sting operation” in which a person hired by you approaches your …
http://www.catchyourcheatingpartner.com/should_you_set_up_honey_trap.php – View by Ixquick Proxy – Highlight
—————————————————————————————-
OR, just Bully Them To Death with “Swiftboating”, “Character Kills”…
(This is why good candidates don’t run for office, nobody wants to get character assassinated except the ones that are so dirty they just don’t give a damn– GH)
Sen. Rand Paul’s wife hesitant about White House bid – USA TodaySep 18, 2013 … Democrat LBJ won the Whitehouse by a gigantic landslide on an anti-war … As far as character assassination, with all the ammo that he has …
http://www.usatoday.com/ story/ onpolitics/ 2013/ 09/ 18/ rand-paul-wife-2016-presidential-race/ 2832395/ – View by Ixquick Proxy – Highlight
KNIGHT: Foiling the left’s character assassination – Washington TimesSep 23, 2013 … KNIGHT: Foiling the left’s character assassination … that was so much a part of our country’s life and certainly our time in the WhiteHouse.”.
http://www.washingtontimes.com/ news/ 2013/ sep/ 23/ knight-foiling-the-lefts-character-assassination/ ?page=all – View by Ixquick Proxy – Highlight
Romney: Obama engaged in “character assassination” – CBS NewsSep 26, 2012 … “This is a campaign, not about character assassination, even though that’s … the economy going while in the WhiteHouse, and will twist things.
http://www.cbsnews.com/ 8301-250_162-57521036/ romney-obama-engaged-in-character-assassination/ – View by Ixquick Proxy – Highlight
The character assassination of Hillary Clinton – Washington PostJan 1, 2013 … The rush to character assassination seems to be our only bipartisan … She is slated to appear before the House Foreign Affairs Committee in …
articles.washingtonpost.com/ 2013-01-01/ opinions/ 36103279_1_benghazi-attacks-clot-ambassador-christopher-stevens – View by Ixquick Proxy – Highlight
Character assassination on the campaign trail – Washington PostJul 15, 2012 … WhiteHouse to get aggressive on climate change · The Plum Line | Greg …. Character assassination is a diversion, not a policy. Personal Post …
articles.washingtonpost.com/ 2012-07-15/ opinions/ 35489376_1_character-assassination-economic-growth-obama – View by Ixquick Proxy – Highlight
The character assassination of Trayvon Martin – Question EverythingJul 19, 2013 … This Wednesday they sent a 16-year-old intern to question theWhiteHouse about whether the President of the United States was providing …
http://www.qwstnevrythg.com/ 2013/ 07/ the-character-assassination-of-trayvon-martin/ – View by Ixquick Proxy – Highlight
Washington Post Column: The character assassination of Hillary …Jan 1, 2013 … Washington Post Column: The character assassination of Hillary Clinton ….. The WhiteHouse claimed the firings were done because financial …
http://www.freerepublic.com/focus/news/2974085/posts – View by Ixquick Proxy– Highlight
Barack Obama attacked Hillary Clinton in negative campaign leaked …Jan 23, 2012 … Barack Obama agreed to using character assassination tactics against Hillary Clinton during his 2008 presidential campaign, WhiteHouse …
http://www.telegraph.co.uk/ news/ worldnews/ northamerica/ usa/ 9032170/ Barack-Obama-attacked-Hillary-Clinton-in-negative-campaign-leaked-mem os-show.html – View by Ixquick Proxy – Highlight
50 years after jfk’s death, gop engaging in characterassassination of …Nov 23, 2013… sought to bring grace, history, and good works to the WhiteHouse. … if character assassination and ideology hadn’t ended his Camelot in …
http://www.politicususa.com/2013/11/23/brand-presidential-assassination.html –View by Ixquick Proxy – Highlight
Beck’s Character Assassination Campaign Against Van Jones Was …Sep 9, 2009 … Last month, Fox News’ Glenn Beck engaged in a characterassassination campaign to demonize WhiteHouse environmental adviser Van …
http://www.thinkprogress.org/economy/2009/09/09/59758/beck-kerpen-jones/ –View by Ixquick Proxy – Highlight
Asad Rauf accuses Mumbai police of ‘characterassassination’ over …Sep 28, 2013 … Asad Rauf accuses Mumbai police of ‘character assassination’ over IPL …. WhiteHouse makes Twitter typo, sparks Obamacare photo meme …
news.yahoo.com/ asad-rauf-accuses-mumbai-police-character-assassination-over-05381012 4.html – View by Ixquick Proxy – Highlight
Limbaugh: Supreme Court Used “Character Assassination” In …Jun 26, 2013 … They, the majority in this decision, used character assassination as a … Tucker Carlson: WhiteHouse Saying It’s Your Fault If You Lost Your …
http://www.realclearpolitics.com/ video/ 2013/ 06/ 26/ limbaugh_supreme_court_used_character_assassination_in_doma_decision. html –View by Ixquick Proxy – Highlight
AP Starts the 2016 Character Assassination of Rick Perry, Part 1 …Jul 10, 2013 … NBC: ‘Escalating Battle’ Between WhiteHouse and Press Corps Over … AP Starts the 2016 Character Assassination of Rick Perry, Part 1: ‘Five …
http://www.newsbusters.org/ blogs/ tom-blumer/ 2013/ 07/ 10/ ap-starts-2016-character-assassination-rick-perry – View by Ixquick Proxy – Highlight
Romney Calls ‘Disgraceful’ Obama Team’s Plan forCharacter …Aug 9, 2011… personal assault ” and character assassination on Romney, who it … a prominent Democratic strategist close to the WhiteHouse told Politico.
http://www.foxnews.com/ politics/ 2011/ 08/ 09/ romney-calls-disgraceful-obama-teams-plan-for-character-assassination / – View by Ixquick Proxy –Highlight
The Zionist Character Assassination Of Mel Gibson – RenseWhether or not the planned and intended character assassination evidenced by … harlots and their supportive whores in Congress and the WhiteHouse.
http://www.rense.com/general72/zoch.htm – View by Ixquick Proxy – Highlight
Althouse: Character assassination attempted on 5th Circuit Judge …Jun 5, 2013 … Character assassination attempted on 5th Circuit Judge Edith Jones. ….. (she was sent out the side door of the WhiteHouse and put in a cab).
althouse.blogspot.com/ 2013/ 06/ character-assassination-attempted-on.html –View by Ixquick Proxy – Highlight
Frisk judge’s attorney says city using ‘characterassassination’ – NY …Nov 10, 2013 … Frisk judge’s attorney says city using ‘character assassination’. Judge Shira …. WhiteHouse widens Obamacare insurance exemptions.
http://www.nydailynews.com/ news/ crime/ frisk-judge-attorney-city-character-assassination-article-1.1512570 – View by Ixquick Proxy – Highlight
AP Starts the 2016 Character Assassination of Rick Perry, Part 2: ‘A …Jul 10, 2013 … But his WhiteHouse run flamed out spectacularly, culminating in a debate in Michigan where Perry remembered that he’d pledged to shutter …
http://www.newsbusters.org/ blogs/ tom-blumer/ 2013/ 07/ 10/ ap-starts-2016-character-assassination-rick-perry-part-2 – View by Ixquick Proxy –Highlight
My Turn: Donald Rumsfeld a subject of characterassassination …Oct 14, 2013 … My Turn: Donald Rumsfeld a subject of character assassination …. Right are finding common cause – namely, an amateur is in the whitehouse.
http://www.taosnews.com/ opinion/ article_8894cbc4-31cd-11e3-a383-0019bb2963f4.html – View by Ixquick Proxy – Highlight
Character Assassination of Manning is Defense of Criminal U.S. …Aug 4, 2013 … Character Assassination of Manning is Defense of Criminal U.S. Foreign Policy …. Glenn Greenwald Tells MSNBC Host Put Down WhiteHouse …
http://www.youtube.com/watch?v=piF_EhvknU8 – View by Ixquick Proxy –Highlight
Character assassination – Wikipedia, the free encyclopedia[edit]. In politics, perhaps the most common form of characterassassination is the spread of allegations that a candidate is a liar.
https://en.wikipedia.org/wiki/Character_assassination – View by Ixquick Proxy –Highlight
Daily Mail’s character assassination was a political act – The GuardianOct 5, 2013 … Will Hutton: The Ralph Miliband article demeans the Mail’s campaigning on bank bonuses and other issues.
http://www.theguardian.com/ commentisfree/ 2013/ oct/ 06/ miliband-daily-mail-damage-democracy – View by Ixquick Proxy – Highlight
character assassination – The Free DictionaryInformation about characterassassination in the free online English dictionary … The BJP is pursuing politics of characterassassination to mislead the people.
http://www.thefreedictionary.com/character+assassination – View by Ixquick Proxy – Highlight
Character Assassination – batstar.netCharacterassassination is slandering another person intending to destroy public trust … (4) In fact it is a conundrum of American politics that one way to beat an …
http://www.batstar.net/piper/char.htm – View by Ixquick Proxy – Highlight
2015: The Dark Art of Political Character Assassination– Nigeria …Nov 17, 2013 … This blackmail, or rather politicalcharacterassassination, always has a victim. It is not the target that is the ultimate loser of such acts- it is …
http://www.nigeriavillagesquare.com/ articles/ 2015-the-dark-art-of-political–character–assassination.html – View by Ixquick Proxy – Highlight
What Is Character Assassination? – wiseGEEKDec 3, 2013 … In general, the goal of characterassassination is to cause some harm to the target as a result of the stories or rumors. For instance, in apolitical …
http://www.wisegeek.com/what-is-character–assassination.htm – View by Ixquick Proxy – Highlight
Character Assassination | This American LifeIn context of the Presidential contest between George W. Bush and Al Gore, we hear stories of characterassassination…political and non-political.
http://www.thisamericanlife.org/ radio-archives/ episode/ 160/character–assassination – View by Ixquick Proxy – Highlight
Character Assassination – Changing MindsCharacterassassination is a common technique used in propaganda. … Politicians are famed for their attacks on their political opponents, from sly innuendo to …
http://www.changingminds.org/ techniques/ propaganda/character_assassination.htm – View by Ixquick Proxy – Highlight
The Deadly Art of Character Assassination – The Real Truth MagazineMudslinging, especially during election campaigns, has become political … Therefore, expect characterassassination to rear its ugly head during the 2004 U.S. …
http://www.realtruth.org/articles/167-tdaoca.html – View by Ixquick Proxy –Highlight
The Political Economy of Character Assassination » CounterPunch …Jan 14, 2011 … The Political Economy of CharacterAssassination. by JONATHAN M. FELDMAN. “I drew and painted out of protest and tried, through my work, …
http://www.counterpunch.org/ 2011/ 01/ 14/ the-political-economy-of-character–assassination/ – View by Ixquick Proxy – Highlight
Tanzania and the Politics of Character Assassination – JamiiForumsOf late, there have been a growing trend or emerging pattern in Tanzanian politics which is constructed on the worst style of political blackmail.
http://www.jamiiforums.com/ great-thinkers/ 564220-tanzania-and-the-politics-of-character–assassination.html – View by Ixquick Proxy – Highlight
The character assassination of Hillary Clinton – Washington PostJan 1, 2013 … The rush to characterassassination seems to be our only bipartisan imperative and is a blight on our political system. In this brooding age of …
articles.washingtonpost.com/ 2013-01-01/ opinions/ 36103279_1_benghazi-attacks-clot-ambassador-christopher-stevens – View by Ixquick Proxy – Highlight
Ramjattan practising politics of deception, characterassassination …Dec 11, 2013 … Ramjattan practising politics of deception, characterassassination … for “ practicing politics of deception and characterassassination”. Finance …
http://www.guyanachronicle.com/ ramjattan-practising-politics-of-deception-character–assassination/ – View by Ixquick Proxy – Highlight
Sonia rails against Nehru’s ‘character assassination‘ – Times Of IndiaNov 17, 2013 … Sonia rails against Nehru’s ‘characterassassination‘. TNN Nov … falsehood and marked by a “political intent aimed at characterassassination“.
articles.timesofindia.indiatimes.com/ 2013-11-17/ india/ 44161327_1_character–assassination-jawaharlal-nehru-memorial-lecture- narendra-modi – View by Ixquick Proxy – Highlight
Michael Hiltzik Turns From Reporting To CharacterAssassination …Sep 19, 2013… moves from reporting the news to writing characterassassinations. … These economists span the political spectrum — from Jeff Sachs to …
http://www.forbes.com/ sites/ kotlikoff/ 2013/ 09/ 19/ michael-hiltzik-turns-from-reporting-to-character–assassination/ – View by Ixquick Proxy – Highlight
Our Publications | Character AssassinationCharacterAssassination: An Interdisciplinary Approach Eric Shiraev George Mason University, USA Any competition in social, professional, and political life …
characterattack.wordpress.com/our-publications/ – View by Ixquick Proxy –Highlight
Hit lists, dirty deeds and character assassination – InformanteMay 22, 2013 … Political opportunism has reached its lowest point and the only comfort is … of political backstabbing and characterassassination are clearly to …
http://www.informante.web.na/ index.php?option=com_content &view=article &id=12044:hit-lists-dirty-deeds-and-character–assassination &catid=16:off-the-desk &Itemid=102 – View by Ixquick Proxy – Highlight
AP Starts the 2016 Character Assassination of Rick Perry, Part 2: ‘A …Jul 10, 2013 … AP Starts the 2016 CharacterAssassination of Rick Perry, Part 2: ‘A Political Punchline on Par With Dan Quayle’ …
http://www.newsbusters.org/ blogs/ tom-blumer/ 2013/ 07/ 10/ ap-starts-2016-character–assassination-rick-perry-part-2 – View by Ixquick Proxy –Highlight
Character Assassination – Huffington PostThe term “swiftboating” is an expression that has become synonymous with deceptive and untrue political attacks that were originally used with devasta.
http://www.huffingtonpost.com/news/character–assassination – View by Ixquick Proxy – Highlight
Is ‘The Kennedys’ Miniseries a ‘Political CharacterAssassination …It’s Surnow whom Greenwald blames for what he calls the script’s “politicalcharacterassassination” of the Democratic icon. True to form, Greenwald has made a …
http://www.bravenewfilms.org/is_the_kennedys_miniseries_a_political_character_assassination – View by Ixquick Proxy – Highlight
s Hilary Clinton undergoing a character assassination? | Debate.orgYes, I believe that Hillary Clinton is undergoing a characterassassination. If you look beyond a year ago in the past, Hillary Clinton’s political and personal …
http://www.debate.org/ opinions/ is-hilary-clinton-undergoing-a-character–assassination – View by Ixquick Proxy – Highlight
The Politics of Character Assassination by LTC Allen West | African …Sep 19, 2010 … “The Politics of CharacterAssassination”. “If you push a negative hard and deep enough it will break through into its counterside”…..Eleventh …
http://www.africanamericanconservatives.com/ 2010/ 09/ 19/ the-politics-of-character–assassination-by-ltc-allen-west/ – View by Ixquick Proxy –Highlight
Conlin vs. Sawant: The Politics of CharacterAssassinationOct 13, 2013 … Characterassassination is easy. The great thing about it is you don’t actually have to prove anything. You can use any number of techniques.
http://www.waliberals.org/ conlin-vs-sawant-the-politics-of-character–assassination/ 2013/ 10/ 13/ – View by Ixquick Proxy – Highlight
Assassination Quotes – BrainyQuoteEvery two years the American politics industry fills the airwaves with the most virulent, scurrilous, wall-to-wall characterassassination of nearly everypolitical …
http://www.brainyquote.com/quotes/keywords/assassination.html – View by Ixquick Proxy – Highlight
character assassination – WiktionaryNow she has stunned the political class with an open letter to Fillon in Le Monde, a scathing characterassassination accusing him of the “lone ambition” of a …
en.wiktionary.org/wiki/character_assassination – View by Ixquick Proxy –Highlight
Character assassination – Merriam-Webster Onlinenoun. : the act of saying false things about a person usually in order to make the public stop liking or trusting that person. Full Definition of CHARACTER …
http://www.merriam-webster.com/dictionary/character%20assassination – View by Ixquick Proxy – Highlight
Nitish Kumar’s dig at Narendra Modi: social media used for …Oct 23, 2013… were using social media as a tool for “characterassassination. … It was a barely concealed swipe at arch political rival Narendra Modi, who is …
http://www.ndtv.com/ article/ india/ nitish-kumar-s-dig-at-narendra-modi-social-media-used-for-character-a ssassination-436430 – View by Ixquick Proxy –Highlight
Character assassination-Jean Seberg and information control by …Characterassassination — … and Marilyn Monroe — in Jean Seberg’s private life , films, and political victimization, the personal really becomes the political.
http://www.ejumpcut.org/archive/onlinessays/JC28folder/Seberg.html – View by Ixquick Proxy – Highlight
KNIGHT: Foiling the left’s character assassination – Washington TimesSep 23, 2013 … It was 10 years ago that Hillary Rodham Clinton famously lamented “the politics of personal destruction.” The former first lady and future …
http://www.washingtontimes.com/ news/ 2013/ sep/ 23/ knight-foiling-the-lefts-character–assassination/ ?page=all – View by Ixquick Proxy – Highlight
Gujarat BJP complains to EC against Modi’s characterassassination …Nov 25, 2013 … “It is pertinent to note that Arjun Modhwadia, while giving apolitical … The phrase is used to describe a person of bad/loose character,” BJP …
Dave McClure says Silicon Valley is ‘functionally illiterate’ at …Jul 1, 2013 … In a series of tweets that appear to have been sent out of frustration, prominent SiliconValley VC, Dave McClure let it all rip on what he thinks of …
http://www.ventureburn.com/ 2013/ 07/ dave-mcclure-says-silicon–valley-is-functionally-illiterate-about-mar keting/ – View by Ixquick Proxy – Highlight
Bravo’s Start-ups: Silicon Valley Debuts Clips; DaveMcClure …———————————————————————–
Option #6: “The Hack and Block”-
Did you ever think you were doing everything right and things inexplicably go south right at the last minute? If you are a reporter or a public service person, you might be under the watch of a Hack and Block Operative. These technical hackers are already inside your phone and computer via embedded backdoors and spyware. Most of the time they do not even have to watch as you type. They just program their spyware to look for a selection of keywords that may have something to do with what they want to block. For example, if you are working on a story about stuffed animals and toxins, they might program their spyware to resend them anything with the words: “teddy bear, mattel, stuffed, stuffing, elmo, toys, investigation…etc” and on and on for thousands of words. The second you type one of these things, the political operative gets a text about it and goes to work. Did you just set up a meeting with an investor? That investor suddenly gets an anonymous tip with damaging info about you and the meeting is “rain-checked”.. Did you just set up a date online? Your dategets a disturbing message about you and suddenly she is “busy”. Did you just try to source a great tip for an interview? Suddenly the tip source “wants to think about it some more”? Your Operative got mail and you got Blocked.
State Dept. whistleblower has email hacked, deleted | New York Post15 hours ago … WASHINGTON — The personal e-mail account ofa StateDepartmentwhistleblower was hacked, and four years worth of messages — some …
http://www.nypost.com/ 2013/ 12/ 30/ state-dept-whistleblower-has-email–hacked-deleted/ – View by Ixquick Proxy – Highlight
State Dept. whistleblower has email hacked, deleted Alex Jones …10 hours ago … The personal e-mail account of a StateDepartmentwhistleblower was hacked, and four years worth of messages — some detailing alleged …
http://www.infowars.com/state-dept-whistleblower-has-email–hacked-deleted/ – View by Ixquick Proxy – Highlight
State Dept. Whistleblower Has Email Hacked – Breitbart9 hours ago … A whistleblower who had helped expose misconduct by Hillary Clinton’s security detail had his Gmail account hacked and key evidence …
http://www.breitbart.com/ Big-Government/ 2013/ 12/ 30/ Whistleblower-Who-Exposed-State–Department-Wrongdoing-Has-Email-Hacke d – View by Ixquick Proxy – Highlight
Also known as “Hack-And-Extort”!
Ideal counter measures are: Massive disinformation output, never keep anything connected to any network (ie: unplug all power cords and network cables), only write fake meeting dates in electronic calendars, encrypt, relay, tor, create false lead traps that end up at your litigation firm’s office, put black electrical over every camera lens, phone lens, tablet lens, webcam lens, smart tv lens, computer lens, etc.
One of the more horrific uses of Hack and Block is this story, an act whichevery American is now at risk of if you don’t put black electrical tape over every camera lens on your phone, tablet and computers:
http://guardianlv.com/2013/12/apple-inc-and-other-webcams-hacked-miss-teen-usa-nude-photos-taken/
Apple Inc. And Other Webcams Hacked – Miss Teen USA Nude Photos TakenAdded by Brent Matsalla on December 21, 2013.
Saved under Apple, Brent Matsalla, Technology
Tags: apple inc, top
Researchers at the Department of Computer Science at Johns Hopkins University say that Apple Inc.’s iSight camera system among other webcams can be vulnerable to hijack hacking. However, 19-year-old Miss Teen USA, Cassidy Wolf, found out the hard way when she received an anonymous email containing two nude photos of herself that were taken by her own hacked webcam.
The email demanded more nude photos from Wolf or the anonymous sender threatened to release her photos to the public if she didn’t comply. More demands were also made in the email, but the details of these demands were not shared.
The nude photos were taken over several months by Wolf’s own laptop webcam. Wolf said that her webcam light never came on during this period, which would have tipped her off that her webcam was in use. It was never confirmed whether the webcam light had been disabled by the hacker, or if Wolf just didn’t realize the LED light being on. The hacker was spying on her and through up to 150 other webcams in the area.
The FBI says suspected hacker, Jared Abrahams, breached the privacy of people by hacking into their webcams with his sophisticated network and peeping software. Abrahams has now pled guilty to extortion charges.
Earlier this month the FBI also revealed that they have been using a malicious software program called “malware” as a spying technique on suspects through the suspect’s own webcams. The malware program was able to allow surveillance without toggling on the “in-operation” LED light located on a suspect’s webcam. This is a similar sounding observation described by Miss Teen USA when her webcam was hacked and the nude photos were taken. Apple Inc.’s and other webcams have a hardware interlock between the LED light and the webcam. When the webcam is in operation, the LED light is always supposed to be toggled to the on position automatically.
Assistant professor and co-author of the Johns Hopkins’ paper – iSeeYou, Stephen Checkoway, says that he and his partner were able to hack into Apple Inc.’s iSight camera system and disable the LED light when the camera was operating. Checkoway and his paper’s co-author, Matthew Brocker, were able to independently control the camera to record audio, video, and snap pictures without enabling the camera’s integrated LED light. The team was able to accomplish their feat by reprogramming the microcontroller contained within the iSight camera system.
Checkoway and Brocker notified Apple Inc. about their ability to exploit the iSight camera system, and although Apple did not reply to requested comments, Apple sources say they took this very serious. The researchers did follow up with Apple several times, but were not informed by any possible plans for mitigation. Checkoway did note that the exploit now only works on older 2008 Apple products.
The federal government made agreements with seven computer rental companies last year, when it was discovered that they were unlawfully spying on their customers. The companies were allegedly capturing photos of their customers through the rental computer’s webcam.
Miss Teen USA is only one case where nude photos have been taken from a hacked webcam. Apple Inc. and other webcam manufacturers will always remain vulnerable to malware hacking programs. The Federal Trade Commission says that currently many thousands of people may be getting spied on from webcam software named PC Rental Agent. This program had previously been installed on approximately 420,000 computers across the world. When it’s not in use, covering the webcam with a piece of paper remains to be the best security from any hacked webcam.
By Brent Matsalla
Sources:
New York Times
Techland
Washington Post
(PS: GHI- A number of auto execs/agency heads have quit, or are sleeping in fear, because they believe they got Hack & Blocked doing bribery, WITH VIDEO, and their numbers may be about to come up in federal investigations. I’d say keep on eye out for Mother Jones or ProPublica’s next video undercover exclusive from the tipsters …… )
Personal Privacy Security 2014:
(What a drag…)
- Get rid of your credit cards. Only use cash.
- Tape over every digital camera lens. Don’t buy devices with built-in cameras.
- Unplug both the power cord and network cord of any device that network connects, when not in use. Routers, gamebox, appliances, Smart TV’s, etc. They all watch you.
- Never leave your wifi unit in the “on” position.
- Keep your cell phone in “flight” mode or “airplane” mode until you are ready to use it and then turn it off after use.
- Always remove the battery from your phone when you go into a meeting or drive between locations.
- Try to buy devices that do not have a GPS chip in them.
- Don’t “sync” any device.
- Phone, computer and other wall charger/adpaters often have bugs built into them.
- Delete your contact list, calendar, taks & memos from any mobile device. Carry them on paper or on a device with no modem, wifi or bluetooth.
- Never use a “social network” site. Delete all data and cancel all existing sites.
- Remember: “If it has a plug, it has a bug”.
- Use TOR and peer to peer hardware and software certified by the open source community.
- Never post your picture online. If you do, make sure it is only used once per site and has your own steganography ID in it but your data meta tags stripped out.
- Don’t own anything with an RFID chip. Even your car tires have them in them.
- Cover your mouth when saying something important. Surveillance cameras read lips.
————————————————————————–
Option #7: “The Molasses Tactic”-
AKA: The slow burn delay tactic
Lawyers and administrators PRETEND to be doing their jobs but, in actuality, they are intentionally delaying and “bottom drawer-ing” actions for years until you run out of money, time, patience, resources and sanity. Specific to reporters, their FOIA (Freedom of Information Act) request will sometimes be held off until the last possible minute.
Sometimes, a law-firm or lawyer will approach you because they “heard about your situation and want to help you”. Be sure they do not, secretly, work for the other side and they are there to make sure you lose the case or that it runs so slow, it has no effect.
————————————————————————–
Option #8:” Having You De-Googled”– CLICK HERE FOR DETIALS
Paying Google to Remove your name, company name or political campaign from Google Web searches or associating a search of your name with artificially created horrible things as was done with Rick Santorum’s name being “search-frozen” by Google to always bring up a disgusting sexual term.
————————————————————————–
See Additional suppression techniques: CLICK HERE>>>
WHEN WHITE HOUSE STAFF ABUSE THEIR ROLES:
WHITE HOUSE HIT SQUADS
Isn’t it sad that, sometimes, the people who you pay part of your paycheck to, to take care of you, sometimes turn around and bite the hand that feeds them?
Oh those politicians… Sometimes they forget that they are the employees of the public.
Recent Freedom of Information Act revelations show that When the Monica Lewinsky scandal happened, The White House put a senior White House adviser named Sidney Blumenthal on the job as character assassination lead. He was mission-ed with defaming Monica Lewinsky, Lucianne Goldberg, Bill Kristol and seeking to destroy Vanity Fair’s Christopher Hitchens, for writing about the scandal.
This is now well documented in the mainstream media and studied in university social ethics classes. Robert Gibbs and Jay Carney are now accused of running the modern day equivalent.
While this may seem horrific for the “highest office in the land”, it is more of the rule than the exception.
Some people work in the White House merely to steer hundreds of billions of dollars of taxpayer money to their friends pockets, or campaign backer/employers pockets. Campaign backers are, more often than not, insane ego-maniacal billionaires who think they are untouchable because they have bought all of the power they want.
These kinds of people ignore the law, morality or ethics and exist purely to show off to the other insane billionaires in their good
ole’ boys club. They will stoop to anything; a character assassination, or even a real assassination, is not out of the question for them.
The procedure uses an axillary unit of the White House press office. The axillary unit never uses official emails. They
conduct their work with personal text messages, personal emails and lunch meetings. They trade access for a hatchet job article on an enemy. They maintain a secret, but direct, link with tabloids, such as the Nick Denton and The Gawker Media Syndicate, in order to machine gun an opponent with fake blogger comments and hit-job articles. ( “Ah.. If only some spy agencies had kept a running archive of every phone call and email White House staff had made in, and out, of the office…..OOOOPSIE… They Did, This Time Around! Well, I bet it will be fun when the subpoenas start rolling out…)
They have “special project IT Consultants” go into the career databases at Axciom, Dun and Bradstreet, and all of the other services recruiters use, and put fake negative comments about the target so they can kill their career. They have a thousand “trade-craft” tools in their dirty war-chest. Some of them are ex CIA.
Is it illegal? VERY MUCH SO!
Can you catch them? The answer used to be no…but, now that everybody knows that every email, restaurant camera, text message and other communication system since 2001 has been recorded, logged, archived and analyzed by multiple federal agencies; maybe now you can!
The HuffPost Puts Sidney Blumenthal On Trial For Media Sins
Posted by Ryan S. Jackson
Is the man who once coined the term “vast ring wing conspiracy” now an integral part of the monster he once decried, willingly abetting a yellow journalism vendetta against Barack Obama?! Peter Drier, of the American Prospect and the Los Angeles Times (amongst others), brings forth the case against Clintonista Sidney Blumenthal:
Former journalist Sidney Blumenthal has been widely credited with coining the term “vast right-wing conspiracy” used by Hillary Clinton in 1998 to describe the alliance of conservative media, think tanks, and political operatives that sought to destroy the Clinton White House where he worked as a high-level aide. A decade later, and now acting as a senior campaign advisor to Senator Clinton, Blumenthal is exploiting that same right-wing network to attack and discredit Barack Obama. And he’s not hesitating to use the same sort of guilt-by-association tactics that have been the hallmark of the political right dating back to the McCarthy era.
Amongst the questionable media narratives Drier accuses Blumenthal of pushing (there are many, and it is a long and winding piece):
• Obama’s high school exposure to a Hawaiian Marxist poet, who Obama mentions briefly in Dreams from My Father and who has since been elevated to an Obama father-figure by hard-right press critic Cliff Kincaid.
• The recent ‘Obama as Radical Black Nationalist’ narrative, and his Chicago connections to Weather Underground member William Ayers.
• A National Review article which accuses Obama of being an integral part of Chicago machine-style politics, which notes: “Blacks adapted to both the tribalism and the corrupt patronage politics.”
• A plethora of different Tony Rezko stories.
• And lest anyone forget, the circa February ‘Obama as Cult Leader’ narrative penned initially by Washington Post columnist Charles Krauthammer.
Hardball politics or cavorting with the enemy? Read the piece and draw your own conclusions:
Peter Dreier
Sidney Blumenthal Uses Former Right-Wing Foes To Attack Obama
Former journalist Sidney Blumenthal has been widely credited with coining the term “vast right-wing conspiracy” used by Hillary Clinton in 1998 to describe the alliance of conservative media, think tanks, and political operatives that sought to destroy the Clinton White House where he worked as a high-level aide. A decade later, and now acting as a senior campaign advisor to Senator Clinton, Blumenthal is exploiting that same right-wing network to attack and discredit Barack Obama. And he’s not hesitating to use the same sort of guilt-by-association tactics that have been the hallmark of the political right dating back to the McCarthy era.
Almost every day over the past six months, I have been the recipient of an email that attacks Obama’s character, political views, electability, and real or manufactured associations. The original source of many of these hit pieces are virulent and sometimes extreme right-wing websites, bloggers, and publications. But they aren’t being emailed out from some fringe right-wing group that somehow managed to get my email address. Instead, it is Sidney Blumenthal who, on a regular basis, methodically dispatches these email mudballs to an influential list of opinion shapers — including journalists, former Clinton administration officials, academics, policy entrepreneurs, and think tankers — in what is an obvious attempt to create an echo chamber that reverberates among talk shows, columnists, and Democratic Party funders and activists. One of the recipients of the Blumenthal email blast, himself a Clinton supporter, forwards the material to me and perhaps to others.
These attacks sent out by Blumenthal, long known for his fierce and combative loyalty to the Clintons, draw on a wide variety of sources to spread his Obama-bashing. Some of the pieces are culled from the mainstream media and include some reasoned swipes at Obama’s policy and political positions.
But, rather remarkably for such a self-professed liberal operative like Blumenthal, a staggering number of the anti-Obama attacks he circulates derive from highly-ideological and militant right-wing sources such as the misnamed Accuracy in Media (AIM), The Weekly Standard, City Journal, The American Conservative, and The National Review.
To cite just one recent example, Blumenthal circulated an article taken from the fervently hard-right AIM website on February 18 entitled, “Obama’s Communist Mentor” by Cliff Kincaid. Kincaid is a right-wing writer and activist, a longtime critic of the United Nations, whose group, America’s Survival, has been funded by foundations controlled by conservative financier Richard Mellon Scaife, the same millionaire who helped fund attacks on the Clintons during their White House years. Scaife also funds AIM, the right-wing media “watchdog” group.
The Kincaid article that Blumenthal circulated sought to discredit Obama by linking him to an African-American poet and writer whom Obama knew while he was in high school in Hawaii. That writer, Frank Marshall Davis, was, Kincaid wrote, a member of the Communist Party. Supported by no tangible evidence, Kincaid claimed that Obama considered his relationship to Davis to be “almost like a son.” In his memoir, Dreams from My Father, Obama wrote about meeting, during his teenage years, a writer named “Frank” who “had some modest notoriety once” and with whom he occasionally discussed poetry and politics. From this snippet, Kincaid weaves an incredulous tale that turns Davis into Obama’s “mentor.”
Kincaid’s piece had been previously circulating within the right-wing blogosphere, but Blumenthal sought to inject the story into more respectable opinion circles by amplifying it in his email blast.
In the same piece, Kincaid, expanding his guilt-by-association tactics, also wrote that Obama “came into contact with more far-left political forces,” including former Weather Underground member William Ayers. Until a few weeks ago, Obama’s tangential connection with Ayers — whose 1960s anti-war terrorism occurred when Obama was in grade school — was echoing among right-wing bloggers.
Some Clinton supporters who also knew about Ayers have been discreetly trying to catapult the story out of the right-wing sandbox into the wider mainstream media. On April 9, Fox News’ Sean Hannity interviewed fellow right-winger Karl Rove, who raised the Ayers-Obama connection. The next day, ABC News reporter Jake Tapper wrote about Ayers in his Political Punch blog. The following week, on his radio show, Hannity suggested to his guest, George Stephanopoulos, that he ask Obama about his relationship with Ayers at the upcoming Philadelphia presidential debate. Stephanopoulos, who was Bill Clinton’s press secretary, replied, “Well, I’m taking notes.” The following night during the April 16 nationally televised Presidential debate, Stephanopoulos dutifully asked Obama about Ayers, who is now a professor of education at the University of Illinois at Chicago.
One can only speculate how much influence Blumenthal did or did not have in elevating the Ayers story into the mainstream media and into the national political debate. What is certain is that Blumenthal sought to keep this classic red-baiting controversy alive.
Blumenthal’s April 24 email dispatch featured a two-year old article by Sol Stern, published in City Journal, sponsored by the right-wing Manhattan Institute. The article, from the journal’s Summer 2006 issue, doesn’t mention Obama. Why would Blumenthal resurrect it now? The article, entitled “The Ed Schools’ Latest–and Worst–Humbug,” was, instead, a frontal attack on Ayers’ views on educational theory and policy. Blumenthal obviously wasn’t trying to offer enlightenment on educational policy or Obama’s positions on school reform as much as he was presumably trying to keep Ayers’ name, and his controversial past, in the public eye.
As a follow-up punch, Blumenthal again dipped directly into the “vast right wing conspiracy” by retrieving and circulating an article from the current issue of National Review — the staunchly conservative opinion journal founded by William F. Buckley. The piece, titled “The Obama Way,” was penned by Fred Siegel who, like Sol Stern, is a former 60s leftist who has moved to the opposite end of the political spectrum, serving at one point as a political advisor to Rudy Giuliani. Siegel’s piece links Obama to corrupt Chicago machine politics, observing that “Blacks adapted to both the tribalism and the corrupt patronage politics” of Chicago’s Democratic Party. In the process, he manages to throw in as many spurious ad hominem attacks on Obama as he can, calling him a “friend of race-baiters” and a “man who would lead our efforts against terrorism yet was friendly with Bill Ayers, the unrepentant 1960s terrorist.”
When Blumenthal worked in the White House, a big thorn in Bill Clinton’s side was the Weekly Standard, the right-wing magazine edited by William Kristol and owned by Rupert Murdoch. But in mid-February, Blumenthal’s email attack featured an article, “Republicans Root for Obama,” written by Weekly Standard executive editor and Fox News talking head Fred Barnes. That same month, Blumenthal also offered up a piece by Scott McConnell, titled “Untested Savior,” that appeared in The American Conservative (a magazine founded by Pat Buchanan) claiming that Obama “would probably lead them [Democrats] to disaster in November.”
When Blumenthal isn’t relying directly on anti-Obama smears from the extreme right, he’s pumping up more traditionally sourced material, from the Washington Post, New Republic, and other publications, to question and damage Obama’s character and electability. On several occasions, Blumenthal has circulated articles from the Chicago Sun Times and the Chicago Tribune about Obama’s ties to developer Tony Rezko, a relationship Obama has said he regrets. In one email, Blumenthal wrote: “The record on Obama’s fabled ‘judgement’? So how would he conduct himself in those promised summits without preconditions with Ahmadinejad, Kim Jong Il, Chavez, Castro, and Assad? Let’s look at how he did with Tony Rezko.”
Earlier this year, one theme pushed by Clinton supporters and buoyed by Blumenthal’s efforts, was that Obama’s appeal was similar to that of a messianic cult leader. Obama’s capacity to inspire people was reframed as a kind of malevolent force, as though his followers would somehow willingly drink poisoned Kool-Aid if Obama so demanded. In his February 7 Time magazine column, “Inspiration vs. Substance,” writer Joe Klein, who, like Blumenthal, worked on the Boston alternative paper, The Real Paper, in the 1970s, wrote: “There was something just a wee bit creepy about the mass messianism — ‘We are the ones we’ve been waiting for’ — of the Super Tuesday speech and the recent turn of the Obama campaign.” That same morning, Blumenthal sent the Klein column to his email list. Later that day, in his Political Punch blog, ABC News reporter Jake Tapper wrote, “The Holy Season of Lent is upon us. Can Obama worshippers try to give up their Helter-Skelter cultish qualities for a few weeks?” (Update: In response to OffTheBus, Tapper is categorical in denying that he in any way relied upon Blumenthal or was influenced by Blumenthal in the production or in the writing of this story or his reports on William Ayers or the Obama “cult”)
The following day, in the Los Angeles Times, columnist Joel Stein wrote: “Obamaphilia has gotten creepy. What the Cult of Obama doesn’t realize is that he is a politician.”
After this idea had bounced around the media echo chamber for a few days, the liberal watchdog group Media Matters for America, run by David Brock, posted a summary on February 8 of the sudden outbreak of “cult” references about Obama. It was headlined: “Media figures call Obama supporters’ behavior ‘creepy,’ compare them to Hare Krishna and Manson followers.” The next day, Blumenthal sent the Media Matters piece to his email list. A few days later, the New York Times’ Paul Krugman, a Clinton supporter, weighed in with a column, “Hate Springs Eternal,” in which he wrote, “I’m not the first to point out that the Obama campaign seems dangerously close to a cult of personality.” Nor would he be the last. Four days later, Washington Post columnist Charles Krauthammer, an arch conservative, penned a column entitled, “The Audacity of Selling Hope” in which he simply quoted Klein, Tapper, Stein, and Krugman.
One of Blumenthal’s associates scoffs at the notion that there’s anything vaguely conspiratorial about these emails and that a number of the people on the list-serve are also the authors of the pieces he sends out. “They’re just Sid’s friends,” he told me. This is, in fact, the very definition of an echo chamber. People in the opinion-shaping business also seek to influence other opinion-makers, who then bounce their ideas through their overlapping outlets — newspapers, magazines, talk shows, websites, blogs, and social and political fundraising circles. The connections are so incestuous that it’s hard to untangle where the “feedback loop” begins and ends.
Among those whose names show up as recipients of Blumenthal’s emails are writers and journalists Craig Unger, Edward Jay Epstein, Thomas Edsall (Politics Editor of the Huffington Post), Joe Conason, Gene Lyons (Arkansas Democrat-Gazette columnist and author of The Hunting of the President: The Ten Year Campaign to Destroy Bill and Hillary Clinton), John Judis, Eric Alterman, Christine Ockrent, David Brock, Reza Aslan, Harold Evans, and Josh Marshall; academics and think tankers Todd Gitlin (Columbia U sociologist), Karen Greenberg (NYU law school), Sean Wilentz (Princeton historian), Michael Lind, William M. Drozdiak, and Richard Parker; and former Clinton administration officials John Ritch, James Rubin, Derek Shearer, and Joe Wilson.
Not all of Blumenthal’s recipients, or those who, like me, receive the emails second-hand, are Clinton supporters.
Before and after his service in the Clinton White House, Blumenthal wrote for the New Yorker, New Republic, Washington Post, the Guardian, and Salon, where he was often accused of engaging in partisan journalism.
In the Clinton administration, Blumenthal was primarily a behind-the-scenes strategist, but often found himself speaking in front of the cameras and on the record. In both roles, he was known as a committed Clintonista who played hardball. He’s demonstrated those same traits since joining Hillary’s campaign as a senior advisor last November.
Presidential politics can get down and dirty, and Blumenthal is a master at the game. Some Obama supporters might even wish that his campaign would resort to similar tactics. If it did, there would be no shortage of anti-Hillary screeds by the “vast right-wing conspiracy” activists and writers, such as surfacing the photo of Rev. Jeremiah Wright with Bill Clinton at a prayer breakfast at the White House in 1998, invited by the president in the midst of his Lewinsky scandal. Indeed, the right-wingers probably hate Hillary more than they dislike Obama. But so far the Obama camp has avoided slinging the right-wing mud, at least with any of the enthusiasm and diligence demonstrated by Sid Blumenthal.
Follow Peter Dreier on Twitter: www.twitter.com/peterdreier
media character assassination | Tumblr
www.tumblr.com/tagged/media-character-assassination – View by Ixquick Proxy – Highlight
When The Media Treats White Suspects And Killers Better Than Black Victims … almost from the start of his time in the White House, by the tea party, with its …
NAACP President: “Postmortem Character Assassination” Of …
www.realclearpolitics.com/ video/ 2014/ 08/ 17/ naacp_president_postmortem_character_assassination_of_michael_brown.h tml – View by Ixquick Proxy -Highlight
Aug 17, 2014 … Here we have a postmortem character assassination, very troubling. … I have received calls from the White House late at night, early in the morning. … The NAACP has been working with the FBI agents to identify and bring …
Great news: Democrats on board with Reid’s McCarthyite character …
www.hotair.com/ archives/ 2014/ 07/ 08/ great-news-democrats-on-board-with-reids-mccarthyite-character-assass ination-strategy/ – View by Ixquick Proxy – Highlight
Jul 8, 2014 … Considering their ‘dear leader’ in the White House consults Alinky’s book on a …. If you wanted to compare the leftist character assassination of …
More Character Assassination: “Gentle Giant” Had Pot in System …
www.rushlimbaugh.com/ daily/ 2014/ 08/ 18/ more_character_assassination_gentle_giant_had_pot_in_system_cop_s_ver sion_of_story_comes_to_light -View by Ixquick Proxy – Highlight
Aug 18, 2014 … Home > Archives (Aug 18, 2014) > More Character Assassination: “Gentle … With the aid of the Washington Post, I have just participated in a smear …. to grandmother’s house — was accosted by a typically white racist cop and …
Police accused of ‘character assassination’ – Video on NBCNews.com
www.nbcnews.com/video/all-in-/55876972 – View by Ixquick Proxy – Highlight
Aug 15, 2014 … Chris Hayes speaks with Brown family attorney Anthony Gray and St. Louis … Michael Brown’s family condemns what they call character assassination after the Ferguson police … The ‘WhiteHouse jumper’ story gets scarier.
Andrew Johnson | The White House
www.whitehouse.gov/about/presidents/andrewjohnson – View by Ixquick Proxy – Highlight
..
www.politicususa.com/2013/11/23/brand-presidential-assassination.html – View by Ixquick Proxy – Highlight
Nov 23, 2013 … During NBC’s tick-tock march through those terrible Friday hours 50 years … sought to bring grace, history, and good works to the White House.
Democrats turn on Debbie Wasserman Schultz – Edward-Isaac …
www.politico.com/ story/ 2014/ 09/ democrats-debbie-wasserman-schultz-111077.html – View by Ixquick Proxy- Highlight
HOW GOOGLE BECAME A “POLITICAL HIT-Job” PROVIDER:
WALL STREET JOURNALInside the U.S. Antitrust Probe of Google Key FTC staff wanted to sue Internet giant after finding ‘real harm to consumers and to innovation’ Updated March 19, 2015 7:38 p.m. ET 49 COMMENTS WASHINGTON—Officials at the Federal Trade Commission concluded in 2012 that Google Inc. used anticompetitive tactics and abused its monopoly power in ways that harmed Internet users and rivals, a far harsher analysis of Google’s business than was previously known.The staff report from the agency’s bureau of competition recommended the commission bring a lawsuit challenging three Google practices. The move would have triggered one of the highest-profile antitrust cases since the Justice Department sued Microsoft Corp. in the 1990s.Related
- How Google Skewed Search Results
- Digits: Excerpts from FTC Staff Report on Google’s Search Practices
- Google Dodges Antitrust Hit (Jan. 3, 2013)
- EU Prepares to Step Up Google Investigations (July 22, 2014)
The 160-page critique, which was supposed to remain private but was inadvertently disclosed in an open-records request, concluded that Google’s “conduct has resulted—and will result—in real harm to consumers and to innovation in the online search and advertising markets.”
The findings stand in contrast to the conclusion of the FTC’s commissioners, who voted unanimously in early 2013 to end the investigation after Google agreed to some voluntary changes to its practices.
It is unusual for the commissioners to not take staff recommendations. But in this case, they were wrestling with competing recommendations, including a separate report from the agency’s economic bureau that didn’t favor legal action.
AdvertisementThen-Chairman Jon Leibowitz said in a written statement at the time that Google’s voluntary changes deliver “more relief for American consumers faster than any other option.”
Google General Counsel Kent Walker said in a statement Thursday that the FTC ultimately “agreed that there was no need to take action on how we rank and display search results.” He added: “Speculation about potential consumer harm turned out to be entirely wrong. Since the investigation closed two years ago, the ways people access information online have only increased, giving consumers more choice than ever before.”
On one issue—whether Google used anticompetitive tactics for its search engine—the competition staff recommended against a lawsuit, although it said Google’s actions resulted in “significant harm” to rivals. In three other areas, the report found evidence the company used its monopoly behavior to help its own business and hurt its rivals.
ENLARGE The report undercuts Google’s oft-stated contention that the FTC found no evidence of wrongdoing. “The conclusion is clear: Google’s services are good for users and good for competition,” said David Drummond, Google’s senior vice president and chief legal officer, when the FTC closed the matter.
It could prompt new complaints from some Google competitors, such as Yelp Inc., who allege the company still engages in anticompetitive behavior, and renewed focus by antitrust authorities in Europe, who are pursuing their own look into Google.
“This document appears to show that the FTC had direct evidence from Google of intentional search bias,” said Luther Lowe, the vice president of public policy for Yelp.
ENLARGE The Wall Street Journal viewed portions of the document after the agency inadvertently disclosed it as part of a Freedom of Information Act request. The FTC declined to release the undisclosed pages and asked the Journal to return the document, which it declined to do.
“Unfortunately, an unredacted version of this material was inadvertently released in response to a FOIA request,” an FTC spokesman said in a statement to the Journal. “We are taking steps to ensure this does not happen again.”
Embedded in the document and in detailed footnotes are an array of previously unknown details about Google’s business, many of which come from senior officials such as Executive Chairman Eric Schmidt, former executive Marissa Mayer and co-founders Larry Page and Sergey Brin.
Data included in the report suggest Google was more dominant in the U.S. Internet search market than was widely believed. The company estimated its market share at between 69% and 84% during a period when research firm comScore put it at 65%. “From an antitrust perspective, I’m happy to see [comScore] underestimate our share,” the report quoted Google Chief Economist Hal Varian as saying, without specifying the context.
An antitrust suit against Google would have pitted Obama administration appointees against one of the White House’s closest corporate allies. Google was the second-largest corporate source of campaign donations to President Barack Obama’s re-election effort. Google executives have visited the White House scores of times since Mr. Obama has been in office, according to visitor logs.
“The FTC is an independent agency and we respect their independent decision-making,” said Jennifer Friedman, a White House spokeswoman.
In its investigation, FTC staff said Google’s conduct “helped it to maintain, preserve and enhance Google’s monopoly position in the markets for search and search advertising” in violation of the law. Google’s behavior “will have lasting negative effects on consumer welfare,” the report said.
Google has long disputed any characterization that it is a monopoly, saying that competition is “just a click away.”
In discussing one of the issues the FTC staff wanted to sue over, the report said the company illegally took content from rival websites such as Yelp, TripAdvisor Inc. and Amazon.com Inc. to improve its own websites. It cited one instance when Google copied Amazon’s sales rankings to rank its own items. It also copied Amazon’s reviews and ratings, the report found. Spokesmen for TripAdvisor and Amazon declined to comment.
When competitors asked Google to stop taking their content, it threatened to remove them from its search engine.
“It is clear that Google’s threat was intended to produce, and did produce, the desired effect,” the report said, “which was to coerce Yelp and TripAdvisor into backing down.” The company also sent a message that it would “use its monopoly power over search to extract the fruits of its rivals’ innovations.”
In its final agreement, the commission secured a promise that Google would allow websites to opt out of having their content included in its competing search products.
The staff said Google also broke antitrust law by placing restrictions on websites that publish its search results from also working with rivals such as Microsoft’s Bing and Yahoo Inc.
The commission made no mention of this issue in its final report, nor did it secure any commitments from Google to change its policies.
In a third area, the FTC staff said Google violated antitrust law by restricting advertisers’ ability to use data garnered from Google ad campaigns in advertising run on rival platforms.
The FTC report cited a Google employee who said the company once wanted to do away with the unnecessary restriction but was overruled by Mr. Page, who is now Google’s chief executive. A Google spokeswoman declined to make Mr. Page available for comment.
Ultimately, Google changed this policy voluntarily in 2013 at the behest of the agency.
On the most important issue, that of Google’s prized search engine, the FTC report said Google altered it to benefit its own services at the expense of rivals. The report said Google “adopted a strategy of demoting, or refusing to display, links to certain vertical websites in highly commercial categories.”
In what it termed “a close call,” the staff said the FTC shouldn’t issue a complaint against the company because of legal hurdles and Google’s “strong procompetitive justifications.”
‘[Google’s behavior] helped it to maintain, preserve and enhance Google’s monopoly position in the markets for search and search advertising’
—FTC staff report The “evidence paints a complex portrait of a company working toward an overall goal of maintaining its market share by providing the best user experience, while simultaneously engaging in tactics that resulted in harm to many vertical competitors, and likely helped to entrench Google’s monopoly power over search and search advertising,” the staff said.
On Jan. 3, the five FTC commissioners voted to close the investigation. A few months later, now FTC Chairwoman Edith Ramirez told a Senate committee that a majority of commissioners didn’t support a case against Google on any of the allegations under investigation. Write to Brody Mullins at brody.mullins@wsj.com, Rolfe Winkler at rolfe.winkler@wsj.com and Brent Kendall at brent.kendall@wsj.com
PATIENT ZERO – THE FIRST INTERNET CHARACTER ASSASSINATION KILL ORDER
“Monica Lewinsky Speaks: ‘It’s My Mission To End Cyberbullying …”
Clare O’Connor Forbes Staff
Monica Lewinsky has broken a decade-long silence to announce her campaign to end cyberbullying and today’s toxic culture of internet shaming.
In her first ever public address, the former mistress of President Bill Clinton revealed her plan to launch a “cultural revolution” against the sort of online harassment she experienced firsthand in the late 1990s.
“I was Patient Zero,” said Lewinsky, now 41, to an auditorium full of 1,000-plus high-achieving millennials at Forbes’ inaugural 30 Under 30 summit in Philadelphia. “The first person to have their reputation completely destroyed worldwide via the Internet.”
“There was no Facebook, Twitter TWTR +2.85% or Instagram back then,” she said. “But there were gossip, news and entertainment websites replete with comment sections and emails which could be forwarded. Of course, it was all done on the excruciatingly slow dial up. Yet around the world this story went. A viral phenomenon that, you could argue, was the first moment of truly ‘social media’.”
Lewinsky described her life since the 1998 sex scandal that resulted in Bill Clinton’s impeachment as one marred by a deep sense of shame and even suicidal thoughts.
She became emotional telling of the miserable months after then-unknown gossip website the Drudge Report broke the news of her relationship with Clinton — a public humiliation exacerbated by the release of the Starr Report online later that year, offering intimate details of their trysts.
“Staring at the computer screen, I spent the day shouting: ‘oh my god!’ and ‘I can’t believe they put that in’ or ‘That’s so out of context,’” she said. “And those were the only thoughts that interrupted a relentless mantra in my head: ‘I want to die.’”
In the immediate aftermath of the Clinton saga, Lewinsky tried to capitalize on her notoriety, first designing handbags and then hosting a reality dating show. She moved to the U.K., where she attended the London School of Economics and got a master’s degree in social psychology. Still, nothing could remove the specter of her public shaming.
It was only years later in 2010 when she read of the tragic suicide of Rutgers freshman Tyler Clementi that Lewinsky stumbled on what she now sees as a calling.
Clementi’s college roommate secretly filmed him kissing another man in their dorm room and streamed the video via webcam. Derided and ridiculed online, the 18-year-old jumped off the George Washington Bridge to his death.
“That tragedy is one of the principal reasons I am standing up here today,” said Lewinsky. “While it touched us both, my mother was unusually upset by the story, and I wondered why. Eventually it dawned on me: she was back in 1998, back to a time when I was periodically suicidal; when she might very easily have lost me; when I, too, might have been humiliated to death.”
Lewinsky met with Clementi’s parents, who set up the Tyler Clementi Foundation for vulnerable youth, LGBT youth and their allies. She intends to share her story with victims of cyberbullying and online harassment. There are many of them: almost 54% of young Facebook users describe being bullied or harassed online. The recent web hacks that exposed nude photos of A-list celebrities like Jennifer Lawrence serve as a reminder that no one is immune.
“Having survived myself, what I want to do now is help other victims of the shame game survive, too,” she said. “I want to put my suffering to good use and give purpose to my past.”
Follow Lewinsky’s plans on Twitter, at her brand new handle: @MonicaLewinsky.
Killing Monica….From: Keep It Constitutional February 04, 1999The House impeachment managers who are prosecuting President Clinton before the Senate have asked all the questions they cared to ask of the three witnesses they chose to call and apparently learned little of help to their case. That won’t stop them from appealing to the Senate today to compel public testimony from Monica S. Lewinsky, Vernon Jordan, the president’s chum, and Sidney Blumenthal, a political hit man for Bill and Hillary Clinton. Clearly the House managers are ready to prolong this trial until the last senator keels over from terminal boredom, but even senators who want to convict Clinton of high crimes and misdemeanors are signaling they have had enough. The trial phase of this proceeding is effectively over, and today’s vote on the witnesses should say so.Though it may have added only marginally to the stupefyingly voluminous record, this week’s videotaped questioning of the three witnesses should nonetheless be made public. Repetitious and unilluminating though the testimony may be, it is part of a historic event and deserves to be released in full. For the same reason, the Senate’s pending debate on whether to convict or acquit Clinton on charges of perjury and obstructing justice should take place before the eyes of the nation and not in a closed chamber.Even if the Senate deservedly rejects the House managers’ plea to hear witnesses, its route toward ending the trial by Feb. 12 will remain rocky. No one any longer believes that 67 votes can be found to convict Clinton and end his presidency. Recognizing that, Republicans continue to search for a variation on their leadership’s notion of a “finding of fact” that, in so many words and by a simple majority vote, would declare Clinton guilty of willfully lying under oath and trying to obstruct justice.We have held from the onset of the impeachment process that Clinton’s behavior in the Lewinsky affair has earned him the strongest condemnation. That could be expressed, without any question of its being extra-constitutional, in a joint congressional resolution. Conversely, the notion of a “finding of fact” to brand Clinton guilty of the same crimes of which an impeachment vote surely would acquit him is a brazen effort to circumvent the letter and spirit of the Constitution. Republicans have always insisted that the impeachment process is solely about upholding the sanctity and dignity of the law. A partisan, constitutionally unsanctioned “finding of fact” would make a mockery of that standard.
BOB WOODWARD: ALL THE PRESIDENTS “HIT JOBS”:
Exchange between Bob Woodward and White House official in spotlight
Posted by CNN Political Unit (CNN) – An email exchange between two old Washington hands – one, a longtime journalist, and the second, a source in the Obama administration – is at the center of a political controversy Thursday as two sides read the messages differently.
The veteran journalist is Bob Woodward, who broke the Watergate scandal and wrote a book about the debt ceiling negotiations in the summer of 2011. The Obama administration source is Gene Sperling, a senior economic aide to President Barack Obama and a veteran of the Clinton administration.
They traded emails, Woodward said, as he prepared to report that President Barack Obama was “moving the goal posts” around the forced spending cuts, known as the sequester.
That irked the White House, he said Wednesday on CNN’s “The Situation Room with Wolf Blitzer,” and led to the email exchange between Woodward and Sperling.
“They’re not happy at all,” with what he was reporting, Woodward said.
“It was said very clearly, ‘You will regret doing this,’ ” he continued, intimating a threat.
Politico published the emails on Thursday, which a Democrat with knowledge of identified as between Woodward and Sperling. White House Press Secretary Jay Carney did not dispute that the published emails were accurate.
The part of the email from Sperling to Woodward that used the word “regret” said: “But I do truly believe you should rethink your comment about saying saying [sic] that [Obama] asking for revenues is moving the goal post. I know you may not believe this, but as a friend, I think you will regret staking out that claim.”
“The idea that the sequester was to force both sides to go back to try at a big or grand barain [sic] with a mix of entitlements and revenues (even if there were serious disagreements on composition) was part of the DNA of the thing from the start.”
The two were trading words over the deal White House and Congress struck in the summer of 2011, an agreement to increase the federal debt limit in exchange for the spending cuts – a draconian measure which was never expected to take effect but are now set to trigger on Friday. Instead, the forced spending cuts were designed to incentivize further deficit negotiations.
Woodward reported that the White House was agreeing with the forced spending cuts to negotiate in the future a deal which replaced the broad and indiscriminate spending cuts in the sequester with more palatable cuts and without additional funds through tax increases.
Obama has stumped for a sequester replacement which balances spending cuts with additional tax revenue gained through eliminating tax loopholes.
“[W]hen the president asks that a substitute for the sequester include not just spending cuts but also new revenue, he is moving the goal posts,” Woodward wrote in an op-ed published by The Washington Post late last week.
“His call for a balanced approach is reasonable, and he makes a strong case that those in the top income brackets could and should pay more. But that was not the deal he made.”
He spoke by phone with Sperling, a conversation which was apparently heated.
After the email from Sperling, which included an apology for the sharp phone call, Woodward wrote back not taking offense, “You get wound up because you are making your points and you believe them. This is all part of a serious discussion.”
A White House official said Wednesday evening – after the CNN interview – that the email Woodward referenced “was sent to apologize for voices being raised in their previous conversation. The note suggested that Mr. Woodward would regret the observation he made regarding the sequester because that observation was inaccurate, nothing more. And Mr. Woodward responded to this aide’s email in a friendly manner.”
“Of course no threat was intended” in that email, the official said.
And former Obama adviser David Axelrod tweeted that the e-mails were “cordial.”
But Woodward said on CNN that the White House objection to his reporting has no basis in facts.
“It’s irrefutable. That’s exactly what happened,” he said. “I’m not saying this is a moving of the goal posts that was a criminal act or something like that. I’m just saying that’s what happened.”
Carney spoke about the emails specifically and the Obama administration’s approach to working with the press on Thursday, saying “the president expects us to fully explain his policies, to answer questions about his positions and to make clear when we believe factual errors are being stated, which is what we do.”
“Gene Sperling, in keeping with a demeanor I have been familiar with for more than twenty years, was incredibly respectful, referred to Mr. Woodward as his friend and apologized for raising his voice,” Carney said. “I think you can not read those emails and come away with the impression that Gene was threatening anybody.”
Sharyl Attkisson’s Story: DOES THE WHITE HOUSE PUT “HITS” ON CITIZENS?… YEP…
Document Dump Shows DOJ Worked With White House To Target ‘Out of Control’ Sharyl Attkisson For Fast and Furious Coverage Katie Pavlich | TOWN HALL
A Department of Justice document dump to government watchdog Judicial Watch, made public yesterday, shows former DOJ Spokeswoman and Holder Flack Tracy Schmaler talking to the White House about “out of control” investigative reporter Sharyl Attkisson. Attkisson was covering Operation Fast and Furious for CBS News at the time.
An email was sent by Schmaler to White House Deputy Press Secretary Eric Schultz on October 4, 2011 and shows she planned to call Attkisson’s editor and longtime CBS anchor Bob Scheiffer to get a handle on her reporting.
Emails also show Schultz responding to Schmaler with, “Good. Her [Attkisson] piece was really bad for the AG.”
The specific story by Attkisson that Schmaler and Schultz are referring to was about memos showing Holder was briefed about Operation Fast and Furious nearly one year before he claimed he’d heard about the program under oath in front of Congress in May 2011.
Keep in mind that in 2011, when this email exchange occurred, the White House had denied any discussion about Operation Fast and Furious with the Department of Justice. This email not only proves they were jointly targeting Attkisson, but working together to mitigate the scandal. At one point during her pursuit of Fast and Furious Attkisson was screamed at by Schultz, who used profanity, over the phone.
It seems top brass over at CBS gave into DOJ pressure. Attkisson left CBS News last year after 20 years of working at the outlet, citing difficulty in getting stories critical of the Obama administration on the air.
In addition to going directly to the bosses of reporters for intimidation purposes, during her tenure Schmaler regularly worked with far left smear machines like Media Matters to attack other reporters and DOJ whistleblowers.
Internal Department of Justice emails obtained by The Daily Caller show Attorney General Eric Holder’s communications staff has collaborated with the left-wing advocacy group Media Matters for America in an attempt to quell news stories about scandals plaguing Holder and America’s top law enforcement agency.
Emails sent in September and November 2010 show Schmaler working with Media Matters staffer Jeremy Holden on attacking news coverage of the New Black Panther Party voter intimidation scandal.
Holden attacked former DOJ Civil Rights Division attorneys J. Christian Adams and Hans von Spakovsky on Sept. 20, 2010 for what he called an attempt “to reignite the phony New Black Panther Party scandal.”
Throughout the email exchanges TheDC obtained through the FOIA request are numerous examples of Gertz and other Media Matters staff sending the full text of Media Matters blog entries attacking the DOJ’s political opponents in the media.
Among others, Gertz sent Schmaler attack pieces he wrote about Townhall Magazine’s Katie Pavlich, who also authored a book on Operation Fast and Furious; Breitbart.com writers Joel Pollak and Ken Klukowski; Fox News Channel’s William LaJeunesse, Judge Andrew Napolitano, Megyn Kelly, Martha MacCallum, Bill Hemmer, Bill O’Reilly and Sean Hannity; Sipsey Street Irregulars blogger Mike Vanderboegh; DirectorBlue blogger Doug Ross; National Review’s Andrew C. McCarthy; and this reporter. Schmaler left DOJ in February 2013. Under a court order, DOJ turned over 42,000 pages of Fast and Furious documentation to Judicial Watch last week. The documentation was held for years under President Obama’s claim of executive privilege. Because of the vast amount of information, Judicial Watch is asking the public for help reviewing them and with looking for evidence of wrongdoing and corruption.
Attkisson recently published a book, Stonewalled: My Fight for Truth Against the Forces of Obstruction, Intimidation, and Harassment in Obama’s Washington, about her experiences.
Topics:
READ THE ORIGINAL EMAILS ABOUT COORDINATING ATTACKS ON ATTKISSON BY WHITE HOUSE AND DOJ STAFF (Download the following files provided by congressional investigators):
| she-is-out-of-control.pdf |
Former CBS News Reporter Sharyl Attkisson Claims Existence of Obama Enemies’ List
“I kind of assume I’m on a list. I don’t think I’m the only one”Sharyl Attkisson is an investigative journalist who became the story when she quit CBS News after two decades amid allegations that the network refused to run some of her stories that were critical of President Barack Obama. Ahead of the Tuesday release of her book Stonewalled: My Fight for Truth Against the Forces of Obstruction, Intimidation, and Harassment in Obama’s Washington, she spoke to The Hollywood Reporter about her struggles with CBS executives and her assertion that her computers were hacked, possibly by Obama operatives.
THR reached out for a response from CBS News, but the organization declined to comment.
Who did you tell at CBS that your computers were hacked?
The first person I spoke to was Washington bureau chief Chris Isham.
Did he believe you?
He appeared to.
Did CBS care? Did they do anything about it?
God, you know, there’s a lot of people there. He seemed to care. He hired a separate computer forensics firm to look at the computers. They, too, agreed that there had been highly sophisticated remote intrusion of my computers. They decided to dig deeper and embark upon a process that spanned a number of months, during which time the situation with the Associated Press and the government spying on Fox News reporter James Rosen was disclosed, as well as Edward Snowden’s NSA information.
Did they ever find out who hacked your computers and spied on you?
I don’t believe their computer forensics team concluded who spied on me.
Did they ask anybody in the Obama administration if they were the culprits?
Not to my knowledge. Executives discussed with me that they assumed that was the case. And we discussed how to proceed with that information and what we could do about it.
So what did you do about it?
It seemed to fall off the radar after the forensics report was delivered to CBS. And so I hired a — I have a legal and forensics team that began work.
Did they conclude anything yet?
Yes. Her work is still very much active, but they have told me they have evidence of highly sophisticated remote intrusions into my personal and work computers by someone using software proprietary to a government agency.
CBS executives suspect that the government hacked your computer, and CBS computers, but there’s been no accountability? CBS just dropped the matter?
As far as I know, although what they told me was they wanted to heavily pursue it and find out who was responsible. I discovered on my own they have a computer security specialist working for CBS … But nobody ever questioned me, came to my house, checked the security of my system, asked me for more information, or followed up with me.
Do you believe that people working for the president of the United States hacked your computer and spied on you?
The way you phrase the question makes me want to couch it a little bit. I have been told by two computer forensics experts that a highly sophisticated entity using abilities outside non-government resources, using software proprietary either to the DIA, CIA, FBI or NSA made repeat remote intrusions into both my computers over a period of time. And we have evidence of a government computer connection into my computer system.
And why do you think they would target you as opposed to more partisan voices, like Rush Limbaugh or Glenn Beck?
The question carries the assumption that they haven’t targeted others. I kind of assume I’m on a list. I don’t think I’m the only one, along with James Rosen and the Associated Press, that garnered special attention. There’s probably a list of people.
So an enemies list, like in the Nixon administration?
I’ve been told there is such a list, yes.
And who do you suspect is on that list?
Well, there’s an internal email that indicated reporters who were working with leakers in government agencies or perceived as enemies of the White House are being targeted. So I think that’s probably accurate — anybody that they perceive as harmful to their agenda or working with leakers and whistle-blowers, which I did a lot of.
Do you have sources who told you the names on that list? Is Rush Limbaugh on that list, for example?
Another reporter told me — I can’t remember who — that they thought he was on some sort of target list, but I don’t know that to be the case. I have someone who told me the existence of a list but not the names on it.
You’re being accused of being a partisan right-winger. Have you reported negative stories about conservatives?
Most of my reporting has not been political in nature. Some of the stories that were politicized, I don’t consider political stories, but they were made out to be by people who obviously didn’t want them reported, and I would put Fast and Furious and Benghazi in that category. But other stories include the one I won an investigative Emmy Award for last year, which was a series of stories from the time I went undercover to investigate freshmen Republican fundraising. I also did a story that MSNBC’s Rachel Maddow complimented in a seven-minute long segment, exposing Congressman Steven Buyer, a Republican from Indiana, and his possible and allegedly fraudulent charity, which was followed shortly thereafter by his resignation from Congress.
Did your colleagues give you grief about your negative stories on Obama?
Not my reporter colleagues.
But you have said your bosses kind of shut down a lot of your reporting?
Some of them did. It was very complicated. All of them encouraged my reporting initially, and then as time went on some of them encouraged it and some of them discouraged it.
Who were the ones discouraging it?
Nobody ever discouraged it to my face, they just would not run the stories or would have other stories they wanted to put on every time the stories were offered. That was CBS News with Scott Pelley and his executive producer Pat Shevlin primarily, but there may have been others.
You’ve said they did this because of liberal bias?
I’m not sure I’ve ever said that. But I think there was a complex list of reasons why a lot of stories did and didn’t make it on the air the last couple of years. But in a general sense, I noticed a tendency to avoid stories that would draw pushback form people they didn’t want to have pushback from, whether it’s corporations, advertisers or politicians.
Has CBS ever cared about pushback from politicians before, or only under this administration?
I don’t know how these same people would have acted under a different administration. They came in shortly after the Obama administration.
Do you think CBS was unlikely to run negative stories about President George W. Bush for fear of pushback?
They might have been just as likely to be fearful of stories that drew controversy or pushback from corporate entities, charities, politicians, whatever the special interest might be.
Since when has CBS ever been afraid to air controversial political stories? It ran those memos claiming Bush was trying to avoid the Vietnam War. That wasn’t controversial?
CBS is hundreds of people and they’ve changed over the years. It’s not a monolithic organization that has one viewpoint, and that’s why for everything you try to put into a box there are exceptions. For example, they assigned me to cover Benghazi, that wasn’t my idea. And they were very enthusiastic about the story for a period of time. Why they changed on that, I tried to figure out many times and I can’t say, I can only say what my experiences were.
You must have a theory as to why, right?
They simply didn’t want stories on any controversies, whether that involved corporations, advertisers, charities or other special interests. They were not impossible to get on the air, but very difficult. So we just concluded that there was not the same appetite as there had been in the past.
You’re acting like it was a monetary decision on the part of CBS, like it didn’t want to risk its advertising. But these were government stories we’re talking about.
No, I’m trying to explain to you it wasn’t just government stories, although that’s what the media tended to focus on.
Okay, then, name the corporations that wanted to kill your stories.
I don’t think any corporations killed my stories. I said CBS had a tendency, in the last couple years especially, to appear to want to avoid controversies or stories that they felt would get pushback from certain corporations and politicians and special interests and charities.
Can you tell me the names of these corporations, charities and politicians?
I hate to tick them off because I feel like the story should be told in some context for legal reasons, but I think that you can pull some ideas from the book.
Does CBS go after liberal policies that are failing with as much gusto as they do conservative policies that are failing?
Well, whether something’s failing is a matter of somebody’s opinion. But I would say, as Lisa Myers has observed, as USA Today has observed, the media in general has been less enthusiastic about government accountability under the Obama administration. And I concur with those observations.
Why is that the case?
In my view, trying to avoid the pushback, and the fallout, and the headaches that come with doing stories on whatever the topic may be that the powers-that-be don’t like.
So, in journalism today, it works to bully the reporters and they’ll lay off? ‘Speak truth to power’ — that saying from the 1960’s — that doesn’t apply to journalism anymore?
Reporters want to, as you say, ‘speak truth to power,’ but it’s harder to get those types of stories past the gatekeepers.
So what good is CBS News if it’s just going to bow down to the bullies who tell them to shut up?
Those were your words, but I think they do a great job on some controversies and investigations. 60 Minutes still does some great work. So I’m not saying there aren’t very good journalists and work being done, but on the whole, as many other journalists have observed recently and publicly, the media is not as good at holding the powers that be accountable, for whatever reason.
And that reason has nothing to do with political bias?
It’s a complex set of factors involving politics, relationships with corporations and advertisers and, at times, just the idea that they’d rather not have the headache of doing a story that they have to defend.
You seem to be going way out of your way not to label the media biased. But in your book you talk about how one of your bosses insisted on labeling conservative analysts but not labeling the liberal ones, and if they really didn’t like an analyst, they’d label him or her ‘right-wing.’ So if that’s not bias, what is it?
I didn’t say that nobody is ever biased. I’m not trying to be cagey. It’s not one factor at play … I never told CBS when I wanted to leave that I thought anybody was liberally biased. I never argued that point. People kind of drew that conclusion because it served a certain narrative on both sides. It served the narrative of conservatives who were happy to feel like someone was spilling the family secret and it served the narrative of liberals who didn’t like some of my reporting and thought it could be explained away if I were a right-wing conservative. So everybody sort of adopted that line and that’s something that I never said.
So whose rule was it at CBS that analysts who were conservative be labeled as such and analysts who are liberal not be labeled?
I’m not going to name her. And it was some time ago, but she did say after I brought it up, she’d think about it, and she agreed that what I brought up was a good point and she changed — at least with me — what she’d been doing.
And who at CBS got mad at you for going on Laura Ingraham’s radio show because Ingraham is right wing?
I don’t want to say her name, either.
It sounds like you criticize Obama officials by name but you won’t say names when you’re criticizing CBS. Why the double standard?
I said a lot of names in the book, and I have my reasons why … I described it in the book as I wished to describe it.
Did anybody at CBS get mad when reporters went on liberal outlets, like MSNBC?
I can only speak for myself. I saw other reporters go on conservative and liberal outlets and I never heard that they received blowback. So I don’t know if it was just me. But in my experience, they did tell me to not go on the Laura Ingraham Show.
Just the Laura Ingraham Show or all conservative shows?
That’s a good question. At the time it was, ‘just don’t ever go on her show again.’ And then they denied other interview requests on both liberal and conservative outlets after that — a lot, but not all the time.
Are there any celebrities mentioned in your book?
Sheryl Crow and Sinbad. I traveled with them on a trip to Bosnia with Hillary Clinton. They were entertaining the troops. But First Lady Hillary Clinton and her daughter were on a work trip and I was there covering it. I mention them briefly in light of the fact that I did the story that exposed that Mrs. Clinton’s account that we’d been fired at by snipers was not true. I mentioned that Sinbad and Sheryl Crow were on the plane with us.
Was there any pushback on your Hillary-Bosnia report?
No. That sort of highlights the changes that had occurred because that was a different executive producer who, as far as I know, is actually friendly with the Clintons but nonetheless was very gung-ho on the story because he was like most journalists — able to get outside of his own friendships and belief systems and just be a newsman.
Who at CBS did you tender your resignation to?
The first time I tried to leave, a year before I left, I had my agent call CBS president David Rhodes.
What was your interaction with David Rhodes like?
Well, for most of my tenure at CBS he was very supportive. We met privately a lot about how he wanted my stories to get exposure.
When did that change?
As I tried to leave, there were some tense times. But it ended up cordial.
Why did you want to leave?
The bottom line is, the last couple of years it was clear for me that there was nothing meaningful left for me to do at CBS, and I just wanted to move on. They had plenty of talented reporters but, for what I did, investigative and original reporting, there was no appetite for that.
What are your politics personally?
I don’t talk about my politics, but I would say I’m like a lot of Americans. I’m mixed. I can honestly see two valid sides of a debate. That’s not to say I don’t have positions and thoughts on things, of course I do, but I don’t let those things get in the way of my work.
The primary issues in your book are Benghazi, Fast and Furious, the alleged green energy scandals and Obamacare. Which of those four needs further reporting?
Wow. There’s a great deal of reporting to be done on all of them. I can’t pick one. At CBS, I would have continued on all of them, if I was able to.
It sounds like you’ve been telling me that journalists at CBS who don’t toe a certain line have something to fear there. Is that the case at other networks, too?
I’m not sure we have anything to fear, it’s just that if you want to keep working there, you may not be doing what you want to do. In my case it was not being willing to do what they wanted me to do, or disagreeing with it so much that I just would rather move on. I don’t think reporters are fearful, per se, but I think they will tell you at the other networks that it’s getting more difficult to get original and hard-nosed stories on, especially if they don’t fit with the narrative that the gatekeepers in New York are trying to portray.
You were accused by some at CBS of agenda-driven news stories against Obama. Has anyone at CBS ever accused a reporter of agenda-driven stories against Sarah Palin, or George W Bush, or anyone prominent on the right?
When I did stories that clearly were not positive toward Republicans, I was never accused of being a crazy liberal or having an agenda. That only happened when I did stories that were perceived as being negative toward Democrats.
Did your executive producer, Patricia Shevlin, accuse you of not being supportive enough of green energy because of your stories about taxpayer money given to Solyndra before it went bankrupt?
She never told me that — that was her answer to another executive who raised the question: ‘Shouldn’t we be doing these stories on evening news?’
Why is that anecdote about Shevlin significant?
She is a well-known liberal ideologue who let that get in the way of her decisions and judgment. Whether people will say that to you or not, that was the consensus. That was discussed sometimes daily at CBS.
You also said somebody hacked your TV. How would you know? Why would someone want to hack someone’s TV?
I didn’t say that. What I said was the anomalies that were occurring in my house all seemed to be associated with my FIOS line … I think that the work that they were doing to get into my computer system may have interfered with the other systems in the house.
The progressive watchdog group Media Matters for America is leading the charge against you, it seems.
Media Matters has acknowledged targeting me, yes. Not with a computer intrusion, just with trying to discredit the stories I did as much as possible.
Do you think they were paid to do so?
They said they weren’t, but the question has certainly crossed my mind.
Do you know of any occasions where Media Matters was given money earmarked to targeting somebody?
David Folkenflik of NPR told me they were paid to target Rush Limbaugh. He may have misspoken on that, because someone told me it may have been Glenn Beck. He gave me two instances in which they were paid to target. He also said that they were paid to target Fox News. I’m not sure if that’s correct. It was just another reporter relaying that information to me.
(David Folkenflik did not respond to a request for comment. Media Matters president Bradley Beychok told THR: “Media Matters has never taken a dime to target Sharyl Attkisson.”).
Do you think Media Matters has libeled you?
That’s a good question. I haven’t had a legal review of what they’ve said. I actually read little to zero of what they write. They have definitely said many, many, false things. But I’m not sure it qualifies as libel under the law.
They’re a media watchdog. They tell the truth about what the media is reporting, right?
I don’t think they have an obligation to, no. Anyone can say they’re a media watchdog and then give their opinions … most people understand it’s a propaganda blog. They are very close to the Obama administration, Hillary Clinton and Democratic interests.
What does the press think of Media Matters?
Like anybody that reaches out to us, we may take under consideration an idea that they propose. But I never get asked about their conservative counterparts, such as Media Research Center or Accuracy in Media. In my experience, no one ever takes their criticism as if it is something legitimate to be answered, but when Media Matters says something, many people in the media almost treat them as a neutral journalism organization.
Is that biased?
That probably is the result of an unintentional bias.
As we’re talking, I got an email from Media Matters that says a video you released of your computer being hacked is probably just a stuck backspace key.
It’s what I would call a video anecdote, something that happened along the way. It has nothing to do with the forensic evidence and the analysis. It’s just something interesting, a punctuation mark of things that were happening. And, certainly, I expect Media Matters to say that the backspace key was held down.
What story were you working on when your backspace key started operating by itself?
I was preparing questions for my interview with Ambassador Thomas Pickering about Benghazi and the Accountability Review Board.
So of all the stories you did that were seen as negative against Obama, Benghazi was the one that really irritated them?
I think green energy got under their skin first, and the remote intrusions into my computer pre-dated Benghazi.
From what you told me thus far, it sounds like you’re accusing CBS of cowardice more than liberal bias. Is that correct?
I haven’t used that word, ever. CBS is hundreds of people. It’s not a monolithic organization. That’s the hard part about trying to make a statement or draw conclusions. I would use the word ‘fearful,’ rather than ‘cowardice.’ Some people in the decision-making process, not necessarily reporters at the ground level, but some of those deciding what goes on television have become very fearful of the sponsors and would just prefer to avoid conflict and controversy, which means you’re not going to do a lot of original investigative reporting.
You mentioned your former boss David Rhodes. His brother is Ben Rhodes, a security adviser to the president. Is there at least an appearance of a conflict of interest there when he’s telling you to lay off Benghazi while his brother works for the president?
David didn’t tell me to lay off Benghazi, and I don’t really have an opinion of his relationship with his brother, and how that might have affected things.
Did anyone tell you to lay off Benghazi, or did they just stop using your stories on TV?
They started not using my stories. I don’t know what goes on in the decision-making process, but in general the shows’ producers and managing editors and so on would be the ones that decide what goes on the broadcasts and what doesn’t. I certainly had people joining me at CBS and pushing for stories to get on television that didn’t get on. And they were stopped, as far as I was concerned, somewhere in New York.
What reasons did they give you for not airing your stories?
They would just say — and they didn’t talk to me personally, this was to senior producers — they would just say things like, ‘There is no time on the show for it tonight;’ ‘That’s a great story but maybe we’ll get to it tomorrow;’ ‘Not today, but tell us when there are other developments, we’ll consider it again.’
Why would the administration blame the murders in Benghazi on a YouTube video if that was untrue?
Some of the information the administration is withholding from public release involves a meeting or meetings that occurred in which this was presumably discussed. So, we can only wonder, but the body of evidence that’s come out in the two years since would lead a reasonable person to conclude they wanted to steer the public’s direction away from the idea that this was definitely an act of terror, technically on U.S. soil if it was U.S. property overseas. It occurred on the president’s watch, very close to an election, at a time when he had claimed Al Qaeda was on the run.
But that reason sounds fairly pathetic and unworthy of such a huge lie. Doesn’t it?
From whose viewpoint? I mean, it’s apparently important enough for them to deflect opinion, and I’m not sure if that is indeed why they did it, that’s just the best reason most of us can come up with, looking at the evidence that has come out since. Maybe there is a better reason why they did it, I don’t know. I have a feeling we won’t ever have the full story.
What news network do you think you’ll land with next?
I certainly haven’t decided I’ll ever work at another network or even necessarily work full-time again. When I decided to leave CBS, the discussion I had with my husband was, I have to be prepared to walk out and not work anywhere ever again, and we were fine with that.
Have you had offers?
Yes, but I don’t want to discuss them.
Media Matters and others say that you’re pushing a media-is-biased narrative to curry favor with conservatives.
Anyone who knows much of anything about me knows that I don’t curry favor with people. Period.
Being targeted, allegedly, by the Obama administration, and your stories allegedly being shunned at CBS — were those ultimately good things for you?
I don’t think those were pleasant things, but where I sit today I would say, ‘fine, I’m exactly where I ought to be.’ And I will tell you, before all this stuff happened, I did hope to, and thought I would, work the rest of my career at CBS doing as much as I had been doing over most of the last 20 years. It didn’t work out that way, but I’m not sorrowful over it … I think there is a cultural change in journalism that’s going on — a turn away from the kind of reporting that just holds the powers-that-be accountable. It’s not just a CBS thing.
The major news networks are just afraid of the powerful all of a sudden?
Well, when you put it that way, it makes it sound silly, and that’s what I’ve written about in the book. I don’t think there was a sudden switch.
Nobody was saying that the media was afraid of George W. Bush, now all of a sudden they are afraid of Barack Obama?
There were times when people said that — inside CBS, after Rather-Gate.
Were there some depressing days for you at CBS toward the end?
I was very disheartened when my producer and I would have great stories, and in some cases, whistleblowers we convinced to go out on a limb and tell their story, only to then have to go back to them and say nobody’s interested. So, we’ve had to do that more times in the past few years than I’ve had to do in the previous 30.
An Obama spokesman called you “unreasonable.” Are you?
I’m probably one of the most reasonable reporters out there. But their definition of unreasonable is when they answer a question, if it doesn’t make sense or if it contradicts other facts, I don’t just accept it and go away. What have I not asked you about yet that you deem important?
What haven’t I asked you about that you think is important to mention?
A couple people have told me that CBS News has started a whisper campaign to say that I’m paranoid, crazy, and a liar?
Are you paranoid?
I’d like to think not. It’s just a good word they use to discredit and “controversialize” reporters and stories they don’t like.
Assuming this whisper campaign against you is true, who is orchestrating it?
I was told that Chris Isham, the bureau chief in Washington, was a part of it.
Email: Paul.Bond@THR.com
Dr. Katherine Mitchell
Dr. Mitchell exposed one of the biggest abuses of Veterans in U.S. history, resulting in the largest re-organization of the VA in U.S. history. She was attacked and had multiple acts of retribution in exchange for her service to the Nation. That is unacceptable .
Protect the doctor who is protecting our vets
EJ Montini EJ Montini, columnist | azcentral.com
EDr. Katherine Mitchell just may be a hero.
And like many other heroes, she just may be treated like a villain.
Mitchell is the emergency room physician at the Phoenix VA who came forward after a co-worker said that records were being destroyed that at the Phoenix VA Health Care System.
She is the second physician to come forward, but the only one still working for the VA.
Her actions could cost her career.
“I am violating the VA ‘gag’ order for ethical reasons,” she wrote in a statement. “I am cognizant of the consequences. As a VA employee I have seen what happens to employees who speak up for patient safety and welfare within the system. The devastation of professional careers is usually the end result, and likely is the only transparent process that actually exists within the Phoenix VA Medical Center today.”
Two things must not be allowed to happen.
First, veterans must not be allowed to go untreated or neglected at the VA because the system is overwhelmed.
That’s unacceptable.
Also unacceptable would be for a whistleblower like Dr. Mitchell suffering any negative consequences for have the courage to come forward with her concerns.
There are federal investigations now going on to get to the bottom of the problems at the Phoenix hospital.
That’s a good thing. It’s a necessary thing.
It might not have happened had it not been for the issues raised by Dr. Sam Foote, a VA primary-care physician who retired in December, and now by Dr. Mitchell.
We pretend to shelter whistle-blowers but all too often we leave them to twist in the wind.
That can’t happen this time.
“I spent my whole professional life wanting to be a VA nurse, and then a VA physician,” Dr. Mitchell said. “(But) the insanity in the system right now needs to stop, and whatever I can do to accomplish that, I will.”
Our veterans need someone like that.
She has their backs.
We should have hers.
by Linda LewisThe Department of Veterans Affairs is embroiled in a scandal: Employees “cooked the books” to hide extraordinary delays in scheduling healthcare appointments. In Phoenix, 40 veterans reportedly died while waiting for appointments say sources who came forward last month. But, the existence of “inappropriate scheduling practices” was known to upper management four years ago.One of the sources, Dr. Samuel Foote, a retired VA physician, reported that VA managers focused on generating numbers that would make superiors and the VA look good. “There’s really no incentive for the upper management to get accurate numbers,” Foote said. (CNN, 5/21) Thus, Secretary Eric Shinseki was able to say, in December 2013, that wait times were down.Whistleblowers Break the SilenceEarlier intervention was thwarted when the agency tried to silence or discredit employees who voiced concerns.One who spoke up was Lisa Lee, then a VA scheduler in Fort Collins, Colorado. After refusing to comply with an order to hide appointment waiting times, management placed her on unpaid administrative leave for two weeks, she says, then transferred her to Cheyenne, Wyoming. Lee filed an internal grievance, to no avail. Next, she took her concerns outside the agency to the Office of Special Counsel. Lee refused an agency offer to compensate her for lost pay, she says, because it included a requirement to stop whistleblowing.Another who expressed concerns was Dr. Jose Mathews, head of psychiatry at the St. Louis hospital. He reported internally that doctors were shirking half of their caseload. Management responded by removing Mathews from his position and sending him to the basement.Dr. Katherine Mitchell, director of the Phoenix VA’s emergency department, says she contacted the office of Sen. John McCain (R-Ariz.) last September to have a “confidential complaint” about a variety of healthcare issues forwarded to the VA’s Office of Inspector General. AZCentral reports that “Records show her list of concerns was not submitted to the inspector general, who investigates systemic problems and wrongdoing, but to the Office of Congressional and Legislative Affairs — a political liaison department in Washington.” Days later, the agency put her on administrative leave.”Employees at other VA hospitals were inspired by the first whistleblower disclosures to share their observations, CNN reports, demonstrating that whistleblowing can be contagious if there is any encouragement.
Besides the toll on veterans, the VA’s whistleblower reprisals are striking for their banality. The same kinds of abuses occur in virtually every government agency, although VA appears to have more of them. Attorney Stephen Kohn says, “The VA is notoriously bad, and institutionally bad, and no one has taken any steps to fix it – Congress, the Office of Special Counsel, the inspector general.”
Congress has passed a succession of laws to protect whistleblowers, but each ultimately fails because legislators insist on funneling whistleblower cases through administrative courts that provide limited due process and little transparency, both essential to ensuring justice. Moreover, reprisal is rarely punished although whistleblowing is treated harshly.
“As a VA employee I have seen what happens to employees who speak up for patient safety and welfare within the system. The devastation of professional careers is usually the end result, and likely is the only transparent process that actually exists within the Phoenix VA Medical Center today.” – Dr. Katherine Mitchell [AZCentral]
The Administration RespondsPresident Obama has ordered an internal VA review and another to be led by a White House staffer. He has been supportive of Shinseki, saying, “’He has put his heart and soul into this thing and taken it very seriously,’” while saying that he’s waiting for results of an investigation. “[H]e made clear his main target for now was anyone who actually carried out improper practices at VA, rather than the retired Army general at the top,” reports CNN.
Shinseki has put three Phoenix officials on administrative leave, rescinded a bonus to the Phoenix VA Director, and accepted the resignation of the Undersecretary for Health. But, in claiming to be unaware of the extent of the problems, he implicates himself as one of them.
In TIME, Joe Klein writes that “An effective leader would have gone to Phoenix as soon as the scandal broke, expressed his outrage, held a town meeting for local VA outpatients and their families—dealt with their fury face-to-face—and let it be known that he was taking charge and heads were going to roll.” Klein’s strategy is fine for political damage control, but too little, too late for protecting veterans. A truly effective leader would have acted much earlier, to prevent harm in the first place. Forbes contributor Adam Hartung explains how in a discussion of Shinseki’s over-reliance on statistics.
When those long wait times were previously reported, the President publicly admitted to being appalled and told Secretary Shinseki to do something. The Secretary then declared a standard of no more than 125 days from incident to care had to be met. And he told employees of the VA to meet that goal, or they risked losing their jobs.
Shinseki failed to help employees develop a solution, Hartung notes. “He didn’t challenge his staff to find out the root cause of the problem and understand why these waits were so long. He didn’t hire outside consultants to evaluate the problem and propose solutions. He didn’t ask for “best practices” from industry.” (Republicans share the responsibility for any resource shortfalls, having thrown up roadblocks to funding VA services.)
If VA staff lacked resources and leadership to meet numerical goals, they might indeed resort to manipulating numbers. But, that doesn’t explain why Shinseki might be unaware that manipulation was (allegedly) taking place on a massive scale.
The previously mentioned reports of whistleblower reprisal and lack of transparency suggest that Shinseki failed also to provide leadership in terms of VA treatment of whistleblowers. Reports of waste, fraud and abuse do not flow naturally upstream, especially in an agency notorious for whistleblower reprisals. When subordinates thwart official policies by acting in their own interest and alter the official record, whistleblowers are critical to keeping upper management informed.
One of the first acts of any new department secretary, therefore, should be to immediately take steps to encourage and reward whistleblowers. In fairness to Sec. Shinseki, his own boss set a poor example.
# # #
Photo Credit: Vietnam Women’s Memorial, Washington, DC., from Wikipedia.
Linda LewisWriter, web editor for Whistleblowing Today. Former policy analyst (16 years) specializing in homeland security and emergency response.
SARAH LACY:
A View To A Kill. ORDERING UP ONE CHARACTER ASSASSINATION TO GO
Senior vice president Emil Michael floated making critics’ personal lives fair game.Michael apologized Monday for the remarks. Ben Smith A senior executive at Uber suggested that the company should consider hiring a team of opposition researchers to dig up dirt on its critics in the media — and specifically to spread details of the personal life of a female journalist who has criticized the company.The executive, Emil Michael, made the comments in a conversation he later said he believed was off the record. In a statement through Uber Monday evening, he said he regretted them and that they didn’t reflect his or the company’s views.His remarks came as Uber seeks to improve its relationship with the media and the image of its management team, who have been cast as insensitive and hyper-aggressive even as the company’s business and cultural reach have boomed.Michael, who has been at Uber for more than a year as its senior vice president of business, floated the idea at a dinner Friday at Manhattan’s Waverly Inn attended by an influential New York crowd including actor Ed Norton and publisher Arianna Huffington. The dinner was hosted by Ian Osborne, a former adviser to British Prime Minister David Cameron and consultant to the company.At the dinner, Uber CEO and founder Travis Kalanick, boyish with tousled graying hair and a sweater, made the case that he has been miscast as an ideologue and as insensitive to driver and rider complaints, while in fact he has largely had his head down building a transformative company that has beat his own and others’ wildest expectations.
A BuzzFeed editor was invited to the dinner by the journalist Michael Wolff, who later said that he had failed to communicate that the gathering would be off the record; neither Kalanick, his communications director, nor any other Uber official suggested to BuzzFeed News that the event was off the record.
Michael, who Kalanick described as “one of the top deal guys in the Valley” when he joined the company, is a charismatic and well-regarded figure who came to Uber from Klout. He also sits on a board that advises the Department of Defense.
Over dinner, he outlined the notion of spending “a million dollars” to hire four top opposition researchers and four journalists. That team could, he said, help Uber fight back against the press — they’d look into “your personal lives, your families,” and give the media a taste of its own medicine.
Michael was particularly focused on one journalist, Sarah Lacy, the editor of the Silicon Valley website PandoDaily, a sometimes combative voice inside the industry. Lacy recently accused Uber of “sexism and misogyny.” She wrote that she was deleting her Uber app after BuzzFeed News reported that Uber appeared to be working with a French escort service. “I don’t know how many more signals we need that the company simply doesn’t respect us or prioritize our safety,” she wrote.
At the dinner, Michael expressed outrage at Lacy’s column and said that women are far more likely to get assaulted by taxi drivers than Uber drivers. He said that he thought Lacy should be held “personally responsible” for any woman who followed her lead in deleting Uber and was then sexually assaulted.
Then he returned to the opposition research plan. Uber’s dirt-diggers, Michael said, could expose Lacy. They could, in particular, prove a particular and very specific claim about her personal life.
Michael at no point suggested that Uber has actually hired opposition researchers, or that it plans to. He cast it as something that would make sense, that the company would be justified in doing.
In a statement through an Uber spokeswoman, Michael said: “The remarks attributed to me at a private dinner — borne out of frustration during an informal debate over what I feel is sensationalistic media coverage of the company I am proud to work for — do not reflect my actual views and have no relation to the company’s views or approach. They were wrong no matter the circumstance and I regret them.”
The spokeswoman, Nairi Hourdajian, said the company does not do “oppo research” of any sort on journalists, and has never considered doing it. She also said Uber does not consider Lacy’s personal life fair game, or believe that she is responsible for women being sexually assaulted.
Hourdajian also said that Uber has clear policies against executives looking at journalists’ travel logs, a rich source of personal information in Uber’s posession.
“Any such activity would be clear violations of our privacy and data access policies,” Hourdajian said in an email. “Access to and use of data is permitted only for legitimate business purposes. These policies apply to all employees. We regularly monitor and audit that access.”
In fact, the general manager of Uber NYC accessed the profile of a BuzzFeed News reporter, Johana Bhuiyan, to make points in the course of a discussion of Uber policies. At no point in the email exchanges did she give him permission to do so.
At the Waverly Inn dinner, it was suggested that a plan like the one Michael floated could become a problem for Uber.
Michael responded: “Nobody would know it was us.” The White House Attack Dog: David Plouffe, is said to have been hired by UBER.