WordPress Used as Command and Control Server in Election Hacks
This entry was posted in Research, WordPress Security by Mark Maunder 13 Replies
On Friday evening the Department of Homeland Security released a report [PDF link] containing updated and broader analysis of Russian civilian and military intelligence organization’s attempts to interfere with the 2016 US election.
This Wordfence report is an analysis of the new ‘Enhanced Grizzly Steppe Report’ and the data it includes. We show that one of the websites used in the attack was a WordPress website that was (and still is) vulnerable to a SQL injection attack. We describe how it became part of the ‘cyber kill chain’ used in the attack described in the DHS Enhanced Grizzly Steppe report.
Background
‘Grizzly Steppe’ is the name that the United States intelligence community, specifically the FBI and DHS, have assigned to Russian civilian and military intelligence services associated with trying to hack the US 2016 election.
On December 29th, US intelligence released the first Grizzly Steppe report that provided several indicators of compromise or IOCs. These IOCs were indicators of the presence of hacking tools used by the attackers described in the Grizzly Steppe report.
The day after the original Grizzly Steppe report, we released our own analysis of the data in which we shared the actual sample of the PHP malware described in the report, which we had reverse engineered.
On Friday evening, February 10th, DHS released an ‘enhanced analysis’ of Grizzly Steppe with several new IOCs. The report includes 17 PHP malware samples. These all appear to be different variants of P.A.S. which is the malware in the original report which we reverse engineered.
The new report includes some additional data on 9 domain names that were used in the incidents that DHS analyzed and how Windows malware communicated with those domains. In the report below we focus on one domain specifically which is a WordPress site that was used as a command and control (C2) server as part of the attack.
Understanding the Cyber Kill Chain
The term Cyber Kill Chain is a term that Lockheed Martin came up with to describe a sequence of steps that an attacker needs to achieve their objective. It is a way for security analysts to think about and analyze an intrusion.
The diagram below is from Lockheed Martin and is an illustration of each of the steps in the Cyber Kill Chain. [Source: Lockheed Martin]
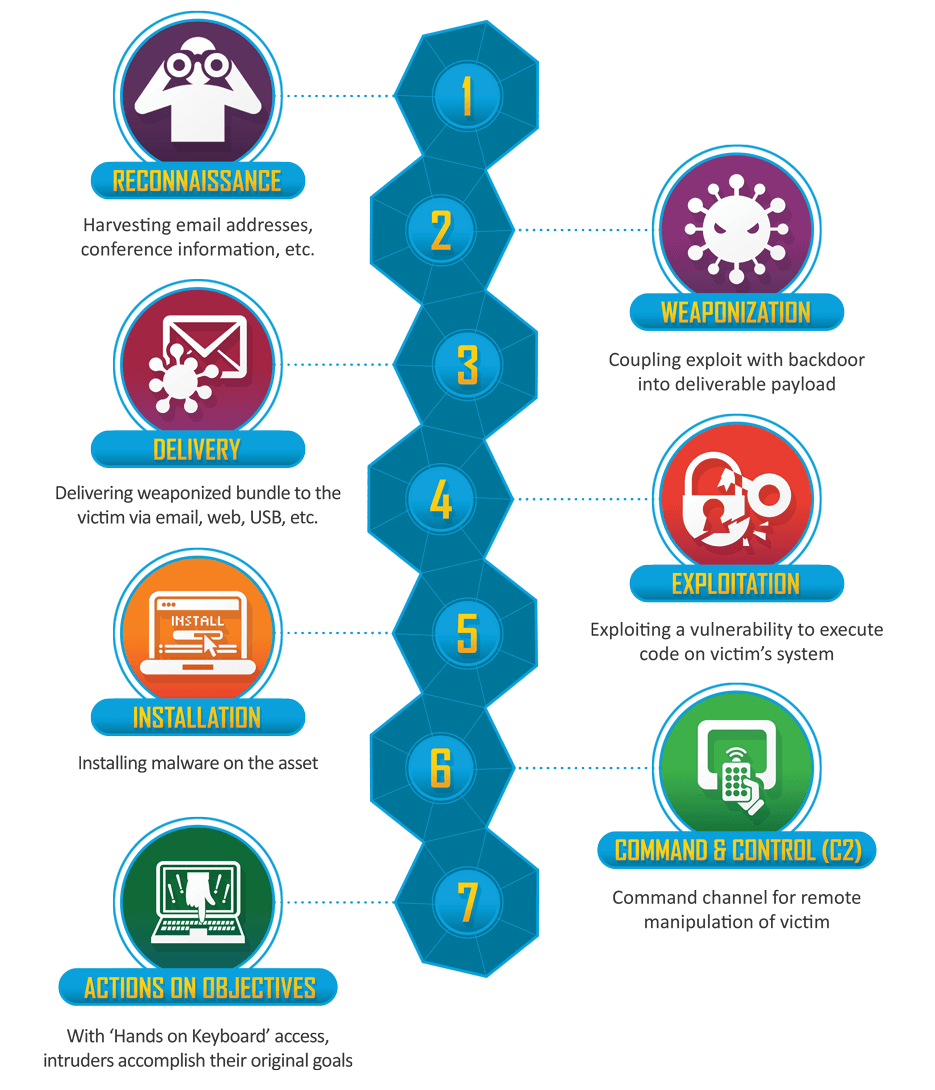
This metaphor is used widely in the intelligence community as a way to think about intrusions. It is also used in the latest DHS Grizzly Steppe report. So we will use it here to analyze how WordPress was part of a kill chain targeting an individual or group.
How WordPress Became Part of the Attack Chain
One of the malware samples included in the Enhanced Grizzly Steppe report is a Windows DLL.

The malware provides a range of capabilities to an attacker. According to the report:
“The program provides an operator access to a reverse shell on the victim system. Additionally, the malware provides an operator the capability to enumerate the victims Windows Certificate Store, and extract identified digital certificates, including private keys. The application also allows an operator to enumerate all physical drives and network resources the victim system has access to.”
The malware is relatively new in the security community and only appeared in VirusTotal on December 29th when the original Grizzly Steppe report was released.
This malware falls into the Installation step in the kill chain above. To be useful, it needs to be able to communicate with its operator. That is where a command and control or C2 server comes in.
WordPress as the Command and Control Server for Windows Malware
According to the enhanced Grizzly Steppe report, the malware above communicates with a website called cderlearn.com. The report goes on:
The application attempts to download data from a C2 server and write it to a randomly named .tmp file within the users %TEMP% directory. Some of the file names used to store this downloaded data within our lab environment are displayed below:
-—Begin Sample File Names—-
TEMPCab5.tmp
TEMPTar6.tmp
TEMPCab7.tmp
TEMPTar8.tmp
-—End Sample File Names—-
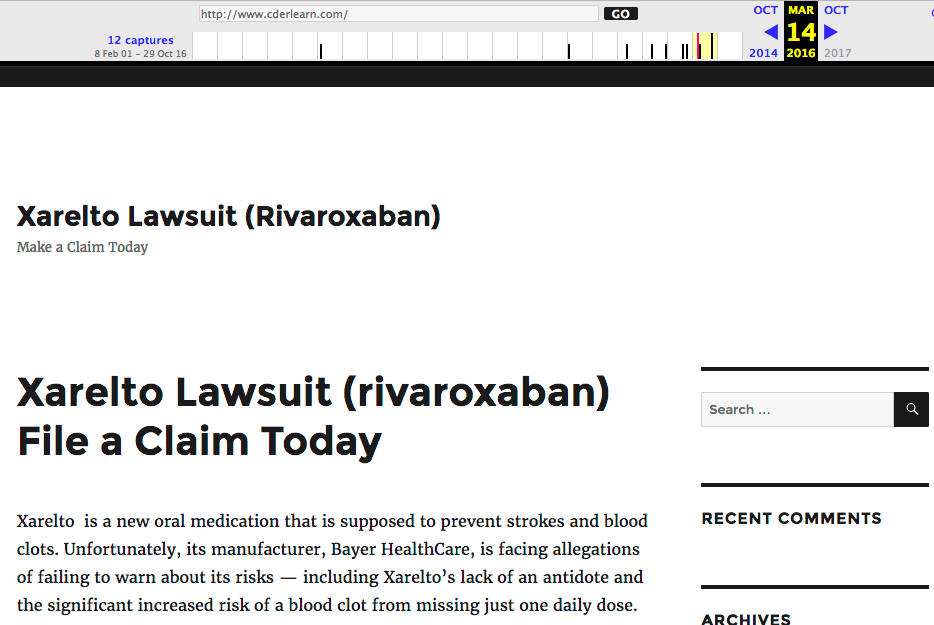
Our Analysis of ‘cderlearn.com’ – How it was Compromised and Used
The website this malware is communicating with is a WordPress site. Looking at archive.org, it has been a WordPress website at least since 14 March 2016.
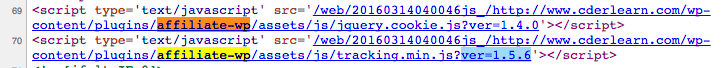
On that date, if you view source on the archive.org snapshot of cderlearn.com, you can see that it was running a plugin called affiliate-wp, version 1.5.6.
On March 16th, 2015, one year earlier, the vendor of Affiliate-WP announced that there was a serious SQL injection vulnerability in the plugin.
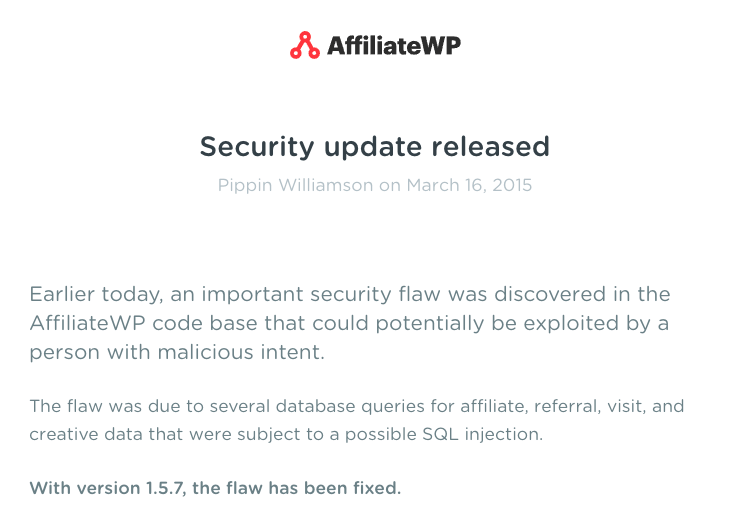
cderlearn.com was running a vulnerable version of Affiliate-WPin March of last year, which may have been used to compromise the site.
cderlearn.com was then used as a command and control server for malware that was designed to give an attacker remote control over a windows workstation. The DHS report provides a few samples of the network traffic between the Windows malware and cderlearn.com:
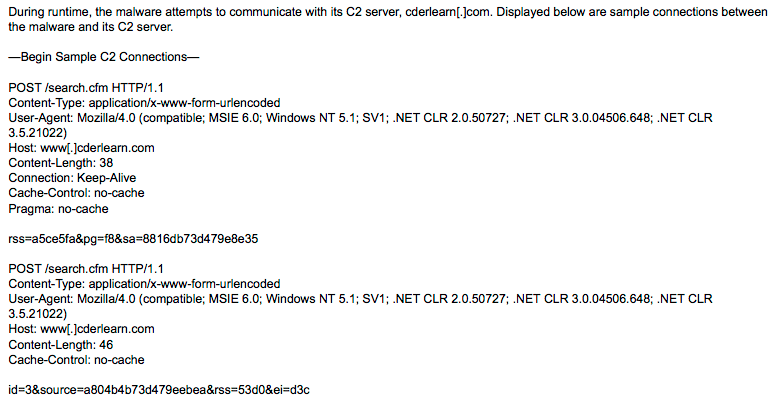
The malware appears to be sending POST requests to a ‘search.cfm’ script which is part of the command and control malware installed on cderlearn.com and is disguising itself as a Cold Fusion search script.
Surprisingly, the website in question appears to still be using the same vulnerable version of the Affiliate-WP WordPress plugin, even today.
Conclusion
In the example above, a vulnerable WordPress site was used in the ‘Command and Control’ step in the kill chain to provide a command channel for remote manipulation of a victim’s workstation. As you can see, this is a sophisticated attack that requires several distinctly separate hacks to achieve its objective. Compromising a WordPress site and using it as a C2 server is only one of those steps, but is a critical part of the kill chain that the attacker needs to achieve their objective.
When we think about securing our WordPress sites, we usually think about the personal impact that a hacked site might have on us, our business and our customers. The story above illustrates how a compromised WordPress site can be used as part of a sophisticated kill chain, used by a nation state actor to attempt to change the outcome of an election.
Securing your website by using a firewall and malware scanner like Wordfence is important, not just to protect your own interests and your customer data, but to help secure the wider Internet as a whole.
Final note regarding comments: Please note that due to the political nature of this issue, we won’t be publishing any comments with political overtones. Our focus is simply on the data that DHS released and the data we are seeing ourselves and our analysis of it. Thank you.