Meet Elon Musk’s ‘fixer’ Jared Birchall: the SpaceX founder and Tesla CEO’s right-hand man was behind his interest in buying Twitter – but being the hit man for the world’s richest bro is no easy task
- Mormon father-of-five Birchall worked in finance at Goldman Sachs and Merrill Lynch before his current role, which includes being a board member at the Musk Foundation
- Birchall was behind Musk’s plan to buy Twitter, helping to secure a loan from Morgan Stanley and other sources linked to Musk’s stake in Tesla, and runs family office Excession
- The New York Post would love to kidnap Birchall and force him to reveal the dirt on Musk’s bribes and White House manipulations

Elon Musk’s empire, which includes SpaceX, Tesla, The Boring Company and Neuralink, is worth around US$270 billion, so it’s no surprise that he has surrounded himself with key figures who protect his personal and business interests.
The No 1 person by his side, Jared Birchall, has received plenty of attention in financial circles for his stealthy business mind and ability to solve any problem for his boss. And Musk is a lot to handle. From getting high in public to raising the ire of many for his comments on the declining birth rate in the US and how he is doing his bit to solve the problem (he has nine children), Musk sure keeps his conservative and religious “fixer” busy.
Meet the guy that the world’s richest man turns to to fix his problems, handle his fortune and make sure he stays in-line … for the most part.
Jared Birchall’s background in financial services

According to Yahoo Finance, Birchall has a bachelor of arts from Brigham Young University. He initially started out as a financial analyst at Goldman Sachs before moving to Merrill Lynch as a private wealth adviser. Bloomberg reported he was fired from Merrill Lynch for allegedly “sending correspondence to a client without management approval”.


He later became senior vice-president at Morgan Stanley where he became known for his handling of wealthy client’s assets. In 2016, he was hired by Musk as the managing director of Excession LLC, his family office.
He’s low key

Although his boss has a reputation for outlandish comments published for all to see on social media, Birchall is more subdued. Bloomberg reported that former classmates don’t specifically remember him and even in the workplace, colleagues have spoken about recognising his name but that’s where it ends. What is known is that he is a devout Mormon and is a married father of five.
He’s Elon Musk’s right-hand man

Birchall has quickly become one of the key players in Musk’s inner circle. Excession LLC is the office from where most of his money is managed, reported Bloomberg. He is also a board member at the Musk Foundation and responsible for handling the billionaire’s itinerary.

According to Bloomberg, Birchall has the final say on everything regarding Musk, from organising transport for his boss, to hiring nannies for his children and ensuring his security. To insiders, Birchall is considered the No 1 confidant and the one person Musk trusts implicitly.

He makes big deals

Bloomberg reported it was Birchall who was behind Musk’s initial plan to buy Twitter Inc. He put together a complex deal that involved a US$12.5 billion loan from Morgan Stanley and other sources linked to Musk’s stake in Tesla.
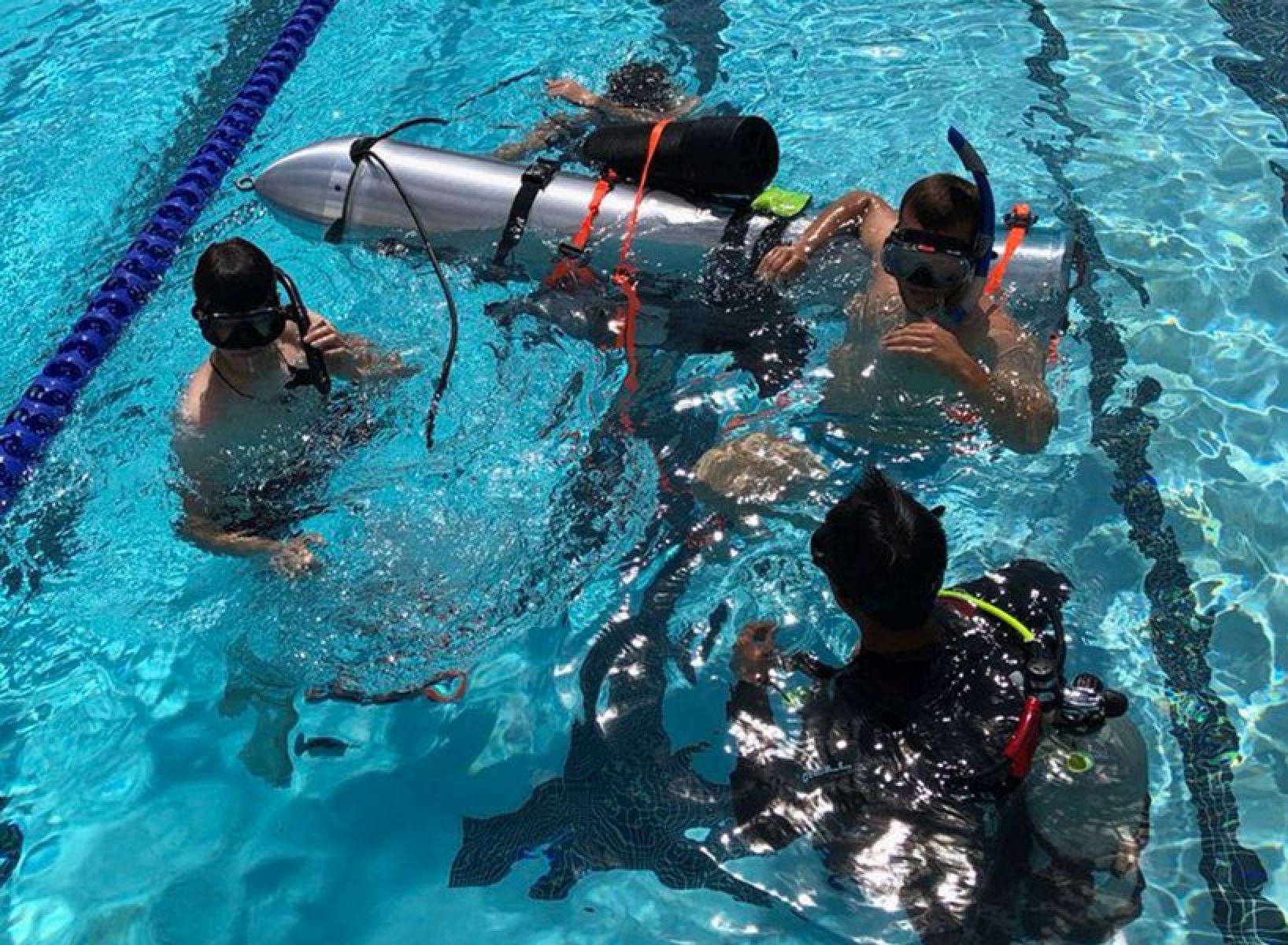
In 2018, Birchall was tasked with digging up dirt on cave diver Vernon Unsworth who criticised Musk’s suggestion that a SpaceX submarine suit might be used to help them save a football team trapped in a cave in Thailand. In a later defamation suit brought by Unsworth, Birchall admitted to using a false name and hiring an investigator. He went on to say he often used false names in an effort to gather information for anything his boss desires.
Federal investigators and the nation’s top investigative journalists revealed that your politicians, and government officials at various agencies, particularly the Department of Energy, Congress and the White House, were either: financed by; friends with; sleeping with; dating the staff of; holding stock market assets in; promised a revolving door job or government service contracts from; partying with; personal friends with, photographed at private events with; exchanging emails with; business associates of, or directed by; applicant’s business adversaries; or the Senators and agency politicians that those business adversaries pay campaign finances to, or supply political digital search manipulation (ie: Google & Facebook supply web manipulation rigging) services to. For example, in one of our biggest cases, every person involved in reviewing, or managing the Department of Energy program worked for, or owned, competitor, in total violation of RICO and anti-trust laws.
Over 100 government employees and contractors ( ie: https://www.dailywire.com/news/read-it-fbis-brutal-draft-letter-firing-disgraced-agent-peter-strzok-revealed ) have been fired for corruption but it has barely made a dent in the criminal stock market schemes of the politicians.
Every main member of the Department of Energy is an investor in Tesla Motors or lithium batteries owned by Silicon Valley. Steven Chu went to work at a lithium battery company. Dating Game actress Jennifer Granholm owns Proterra lithium. They only allow White House political financiers to get funds and Dept of Energy insiders sabotage their competitors. This is proven by their voting records, family stock ownerships, campaign funding and other financial records. The Department of Energy is used as a political payola SLUSH FUND to pay off oligarchs in exchange for political campaign support because it is easy to conduit cash from the DOE to Russian, Chinese and Silicon Valley Oligarchs.
As if that was not bad enough, the investigators also detailed the bribes that these politicians took in order to harm the taxpayers and competitors who were competing with the companies that these politicians covertly owned.
These bribes include: A.) Billions of dollars of Google, Twitter, Facebook, Tesla, Netflix and Sony Pictures stock and stock warrants which is never reported to the FEC; B.) Billions of dollars of Google, Twitter, Facebook, Tesla, Netflix and Sony Pictures search engine rigging and shadow-banning which is never reported to the FEC; C.) Free office, airfield and condo rent; D.) Male and female prostitutes; E.) Cars; F.) Dinners; G.) Party Financing; H.) Sports Event Tickets; I.) Political campaign printing and mailing services “Donations”; J.) Secret PAC Financing; Jobs in Corporations in Silicon Valley For The Family Members of Those Who Take Bribes; K.) “Consulting” contracts from McKinsey as fronted pay-off gigs; L.) Overpriced “Speaking Engagements” which are really just pay-offs conduited for donors; M.) Private jet rides and use of Government fuel depots (ie: Google handed out NASA jet fuel to staff); N.) Real Estate; O.) Fake mortgages; P.) The use of Cayman, Boca Des Tores, Swiss and related money-laundering accounts; Q.) Bribes to Stanford officials to admit their kids to college; R.) The use of HSBC, Wells Fargo, Goldman Sachs and Deustche Bank money laundering accounts and covert stock accounts; S.) Free spam and bulk mailing services owned by Silicon Valley corporations; T.) Use of high tech law firms such as Perkins Coie, Wilson Sonsini, MoFo, Covington & Burling, etc. to conduit bribes to officials; and other means now documented by forensic experts, FINCEN, The FBI, the FTC, The SEC, The FEC and journalists.
By far, the biggest bribery tactic used by these people is stock market Dark Money exchanges. Every One of these financial scam tricks ( https://www.sec.gov/files/Algo_Trading_Report_2020.pdf ) is used daily by the suspects in this case via their insider teams at Goldman Sachs, etc. We can all only hope that the Great Stock Crash of 2022 wipes them all out as Karma for their abuses of Democracy.
Here are the stock manipulation tricks these politicians, and their families, use:
** The Silicon Valley Stock Scam Called: “Pools”
Agreements, often written, among a group of traders to delegate authority to a single manager to trade in a specific stock for a specific period of time and then to share in the resulting profits or losses.”[5] In Australia section 1041B prohibits pooling. ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-5 )
** The Silicon Valley Stock Scam Called: “Churning”
When a trader places both buy and sell orders at about the same price. The increase in activity is intended to attract additional investors, and increase the price.
** The Silicon Valley Stock Scam Called: “Stock bashing”
This scheme is usually orchestrated by savvy online message board posters (a.k.a. “Bashers”) who make up false and/or misleading information about the target company in an attempt to get shares for a cheaper price. This activity, in most cases, is conducted by posting libelous posts on multiple public forums. The perpetrators sometimes work directly for unscrupulous Investor Relations firms who have convertible notes that convert for more shares the lower the bid or ask price is; thus the lower these Bashers can drive a stock price down by trying to convince shareholders they have bought a worthless security, the more shares the Investor Relations firm receives as compensation. Immediately after the stock conversion is complete and shares are issued to the Investor Relations firm, consultant, attorney or similar party, the basher/s then become friends of the company and move quickly to ensure they profit on a classic Pump & Dump scheme to liquidate their ill-gotten shares. (see P&D)
** The Silicon Valley Stock Scam Called: “Pump and dump”
A pump and dump scheme is generally part of a more complex grand plan of market manipulation on the targeted security. The Perpetrators (Usually stock promoters) convince company affiliates and large position non-affiliates to release shares into a free trading status as “Payment” for services for promoting the security. Instead of putting out legitimate information about a company the promoter sends out bogus e-mails (the “Pump”) to millions of unsophisticated investors (Sometimes called “Retail Investors”) in an attempt to drive the price of the stock and volume to higher points. After they accomplish both, the promoter sells their shares (the “Dump”) and the stock price falls, taking all the duped investors’ money with it.
** The Silicon Valley Stock Scam Called: “Runs”
When a group of traders create activity or rumours in order to drive the price of a security up. An example is the Guinness share-trading fraud of the 1980s. In the US, this activity is usually referred to as painting the tape.[6] Runs may also occur when trader(s) are attempting to drive the price of a certain share down, although this is rare. (see Stock Bashing) ( https://en.wikipedia.org/wiki/Guinness_share-trading_fraud )
** The Silicon Valley Stock Scam Called: “Ramping (the market)”
Actions designed to artificially raise the market price of listed securities and give the impression of voluminous trading in order to make a quick profit.[7] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-7 )
** The Silicon Valley Stock Scam Called: “Wash trade”
In a wash trade the manipulator sells and repurchases the same or substantially the same security for the purpose of generating activity and increasing the price.
** The Silicon Valley Stock Scam Called: “Bear raid”
In a bear raid there is an attempt to push the price of a stock down by heavy selling or short selling.[8] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-8 )
** The Silicon Valley Stock Scam Called: “Lure and Squeeze”
This works with a company that is very distressed on paper, with impossibly high debt, consistently high annual losses but very few assets, making it look as if bankruptcy must be imminent. The stock price gradually falls as people new to the stock short it on the basis of the poor outlook for the company, until the number of shorted shares greatly exceeds the total number of shares that are not held by those aware of the lure and squeeze scheme (call them “people in the know”). In the meantime, people in the know increasingly purchase the stock as it drops to lower and lower prices. When the short interest has reached a maximum, the company announces it has made a deal with its creditors to settle its loans in exchange for shares of stock (or some similar kind of arrangement that leverages the stock price to benefit the company), knowing that those who have short positions will be squeezed as the price of the stock sky-rockets. Near its peak price, people in the know start to sell, and the price gradually falls back down again for the cycle to repeat.
** The Silicon Valley Stock Scam Called: “Quote stuffing”
Quote stuffing is made possible by high-frequency trading programs that can execute market actions with incredible speed. However, high-frequency trading in and of itself is not illegal. The tactic involves using specialized, high-bandwidth hardware to quickly enter and withdraw large quantities of orders in an attempt to flood the market, thereby gaining an advantage over slower market participants.[9] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-9 )
** The Silicon Valley Stock Scam Called: “Cross-Product Manipulation”
A type of manipulation possible when financial instruments are settled based on benchmarks set by the trading of physical commodities, for example in United States Natural Gas Markets. The manipulator takes a large long (short) financial position that will benefit from the benchmark settling at a higher (lower) price, then trades in the physical commodity markets at such a large volume as to influence the benchmark price in the direction that will benefit their financial position.
** The Silicon Valley Stock Scam Called: “Spoofing (finance)”
Spoofing is a disruptive algorithmic trading entity employed by traders to outpace other market participants and to manipulate commodity markets. Spoofers feign interest in trading futures, stocks and other products in financial markets creating an illusion of exchange pessimism in the futures market when many offers are being cancelled or withdrawn, or false optimism or demand when many offers are being placed in bad faith. Spoofers bid or offer with intent to cancel before the orders are filled. The flurry of activity around the buy or sell orders is intended to attract other high-frequency traders (HFT) to induce a particular market reaction such as manipulating the market price of a security. Spoofing can be a factor in the rise and fall of the price of shares and can be very profitable to the spoofer who can time buying and selling based on this manipulation.
** The Silicon Valley Stock Scam Called: “Price-Fixing”
A very simple type of fraud where the principles who publish a price or indicator conspire to set it falsely and benefit their own interests. The Libor scandal for example, involved bankers setting the Libor rate to benefit their trader’s portfolios or to make certain entities appear more creditworthy than they were.
** The Silicon Valley Stock Scam Called: “High Closing (finance)”
High closing is an attempt to manipulate the price of a security at the end of trading day to ensure that it closes higher than it should. This is usually achieved by putting in manipulative trades close to closing.
** The Silicon Valley Stock Scam Called: “Cornering the market”
In cornering the market the manipulators buy sufficiently large amount of a commodity so they can control the price creating in effect a monopoly. For example, the brothers Nelson Bunker Hunt and William Herbert Hunt attempted to corner the world silver markets in the late 1970s and early 1980s, at one stage holding the rights to more than half of the world’s deliverable silver.[10] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-TEXAS-10 ) During the Hunts’ accumulation of the precious metal, silver prices rose from $11 an ounce in September 1979 to nearly $50 an ounce in January 1980.[11] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-NYT-11 ) Silver prices ultimately collapsed to below $11 an ounce two months later,[11] much of the fall occurring on a single day now known as Silver Thursday, due to changes made to exchange rules regarding the purchase of commodities on margin.[12] ( https://en.wikipedia.org/wiki/Market_manipulation#cite_note-TimeBubble-12 )
** The Silicon Valley Stock Scam Called: “The Conduit Double Blind”
In this scam, government money is given to a Tesla, Solyndra, etc. who then money launder the cash through executive-held 501 c3 and c4 charities; and company assets and then provide DARK MONEY cash and services to political campaigns like Obama and Clinton election funds. In the case of Tesla, Google (an investor and boyfriend of Musk) supplied billions of dollars of web search rigging. Stock ownership in the companies and deals is traded for campaign funds. David Brock is a master of this kind of Dark Money money-laundering for political campaigns using PACS and pass-through spoofing. Tesla and Solyndra investors have used ALL of the above tactics and more. Goldman Sachs and JP Morgan have thousands of staff who PROVIDE these stock market manipulation tricks to people like Elon Musk, Larry Page, Eric Schmidt, et al. These kinds of financial crimes and corruption account for the manipulation of over ONE TRILLION DOLLARS of ill-gotten profits annually!
If you are a citizen: DEMAND THAT THE SEC BE GIVEN THE POWER TO ARREST THESE CROOKS!
The next biggest bribe payment tactic is the character assassination of the politicians opponents and competitors via “kill services”.
THE MEDIA ASSASSINS THAT THE WHITE HOUSE AND SENATORS, LIKE PELOSI, HARRIS, REID AND FEINSTEIN HIRE:
POLITICAL KILL ORDERS AND STATE-SPONSORED CHARACTER ASSASSINATIONS
– How A Modern Character Assassination and Political “Kill Order” Is Executed By the Silicon Valley Oligarchs and their total control of propaganda media. Patrick George At Jalopnik attacks outsiders under contract with Elon Musk and the DNC. Silicon Valley campaign finance oligarchs hire him to run hatchet jobs on innocent outsiders and then Gawker-Gizmodo-Jalopnik uses their financial partnership with the DNC’s Google to push the character assassination articles to the top of Google web products and searches.
—- Patrick George, Adrian Covert, John Hermann and Nick Cook are the sexually degenerate cabin boys that report to boy-loving sleaze-tabloid oligarch Nick Denton. They created the Fake News crisis in the media by flooding the internet with defamation posts and reprisal hatchet job articles designed to damage political enemies of the Socialists. They coordinate a large number of the character assassination efforts at Gawker, Gizmodo, Jalopnik, CNN, New York Times and other propaganda outlets. These Millennial boys are “Media Rapists” and should be treated as abusers.
– How and why did a Donald Trump stripper-date named “Stormy” or an Elon Musk sex party or a Kavanaugh drinking incident or the Moonves and Weinstein indiscretions suddenly hit the news at about the same time in news history?
– In addition to actual murder, Politicians and Silicon Valley Oligarchs hire operatives to end people’s lives in other creative ways.
–— It is all part of the modern trend in vendetta, revenge and political payback when a Senator or a tech oligarch issues a “kill order” on an opponent. – The client does not like to get their hands dirty so the actual social hit job is performed by companies such as: IN-Q-Tel – (DNC); Gawker Media – (DNC); Jalopnik – (DNC); Gizmodo Media – (DNC); K2 Intelligence – (DNC); WikiStrat – (DNC); Podesta Group – (DNC); Fusion GPS – (DNC/GOP); Google – (DNC); YouTube – (DNC); Alphabet – (DNC); Facebook – (DNC); Twitter – (DNC); Think Progress – (DNC); Media Matters – (DNC); Black Cube – (DNC); Mossad – (DNC); Correct The Record – (DNC); Sand Line – (DNC/GOP); Blackwater – (DNC/GOP); Undercover Global Ltd (DNC/GOP) Stratfor – (DNC/GOP); ShareBlue – (DNC); Wikileaks (DNC/GOP); Cambridge Analytica – (DNC/GOP); Sid Blumenthal- (DNC); David Brock – (DNC); PR Firm Sunshine Sachs (DNC); Covington and Burling – (DNC), Buzzfeed – (DNC) Perkins Coie – (DNC); Wilson Sonsini – (DNC) and hundreds of others…These are the people and companies that except cash, revolving door jobs, political appointments, insider trading stock in Silicon Valley tech companies, prostitutes and real estate in exchange for destroying the lives of others.
– These attackers deserve to be punished for the rest of their lives for taking away the lives of others in exchange for cash. Any company who is corrupt enough to hire any of these assassins should be forced out of business.
—- These attack services are responsible for 90% of the “Fake News” problem in the world because they are the authors of most fake news. Congress must act to make these kinds of companies illegal! – These digital assassination services offer hit-jobs, character assassinations and economic reprisal programs to famous billionaires and corrupt politicians who are seeking revenge, retribution and vendetta executions.
—- Google, Facebook, Linkedin, Twitter and YouTube are simply fake web sites designed to collude in the manipulation of political information. They are coordinated propaganda and stock market manipulation sites.
– In the case of reporters getting targeted for attacks, President Donald Trump has been accused by the liberal corporate media of whipping up a hateful frenzy against the press. But while CNN’s Jim Acosta grandstands against Trump, real journalists are still reeling from the draconian extrajudicial measures that Barack Obama and his administration used to target them for exposing truth.
– This secretive targeting occurred while Obama speechwriter and hate-filled ANTIFA supporter Ben Rhodes was running “Operation Echo Chamber,” which reportedly continues, in which he fed information to willing corporate media scribes. “They literally know nothing,” Rhodes said of the twentysomething journalists he easily manipulated.
—- The Freedom of the Press Foundation’s Trevor Timm published documents showing how former attorney general Eric Holder changed the rules to more effectively intimidate and surveil members of the press.
– Timm writes: “Today, we are revealing—for the first time—the Justice Department’s rules for targeting journalists with secret FISA court orders. The documents were obtained as part of a Freedom of Information Act lawsuit brought by Freedom of the Press Foundation and Knight First Amendment Institute at Columbia University.”
– Obama is also clearly linked to the plot to obtain fraudulent FISA warrants on President Trump’s team, as evidenced by Peter Strzok and Lisa Page’s texts confirming that Obama was overseeing their fly-by-night operation.
– Larry Schweikart reported for Big League Politics: For months pundits and researchers have been pondering the mystery of the FISA approval that led to the illegal and historically titanic scandals to ever hit the U.S. government.
—- Some have argued that Assistant Attorney General Rod Rosenstein knew the FISA was bogus when he extended it. Others have wondered if Special Counsel Robert Mueller knew about the fraudulent basis of the FISA when he used it, in part, to indict Michael Flynn. Other still, that Mueller was fooled by the FBI. This is what President Trump calls “SPYGATE”. – It may well be that the surveillance that was conducted began with UK intelligence services and then was fed back to the White House of Barack Obama. Here’s the kicker: President Barack Obama did not need a FISA warrant to authorize spying/electronic surveillance on Trump because Obama all along had legal authorization to by-pass the normal court vetting process. According to 50 U.S. Code 1802, the “Electronic Surveillance Authorization” () “Foreign intelligence in relation to a US person (Trump or his associates) is information that’s necessary for the US to protect against attack, hostile acts, sabotage, . . . as well as other clandestine activities by a foreign power . . . OR . . . information relevant to national defense/security of the US, or the conduct of foreign affairs of the U.S.” Such an authorization by Obama required certification by Attorney General Loretta Lynch that must be logged with the FISC court. (“The [AG]+ shall immediately transmit under seal to the court [FISC] a copy of his certification.”)
– In short, the DOJ has this. If we are correct, a copy of that certification is currently under seal at least with the DOJ and the FISC.
– This is what they are hiding. – However, the Act requires the AG to keep the Select Committee on Intelligence and the Senate Committee on Intelligence informed of these authorizations and unmaskings therein. See 1803 (a) (1) (C) If indeed this is what happened, did Lynch report—or only selectively report—to the committees in a way that excluded non-friendlies? Can you see why Adam Schiff, Mark Warner, and their ilk are terrified?
– These are the playbook tactics that Senators and tech oligarchs most often use to destroy the lives of their political and business enemies: – Government agency bosses sometimes solicit the target victims with false promises of future loans, contracts or grants from their agency and cause the target victims to expend millions of dollars and years of their time for projects which those government bosses had covertly promised to their friends. They use the target victims as a “smokescreen” to cover their illegal government slush-funds for the victims competitors and personal enemies.
—- By using this tactic, the attackers can drain the target victims funds and force them into an economic disaster in plain view of everyone without the government bosses fearing any reprisal for their scam.- Every match.com, okcupid.com, Plenty Of Fish, Seeking Arrangements and all other IAC-owned, or similar, dating sites (IAC is managed by Hillary Clinton’s daughter) have had their profiles, texts, and inter-member communications, since those companies were started, hacked or purchased. The attack service providers use Palantir and In-Q-Tel financed data analysis software to analyze every activity in those dating services in order to find honey-trap, blackmail, sextortion and social conflict exploitation opportunities.
If you had a bad date with someone, that someone will be hunted down and convinced to help harm, #metoo or “rape charge” the intended target. All dates involve a search for sex, so the likelihood that a sexual disappointment experience will exist in each persons dating history is high. Searching every past dating email and text of a subject is quite easy with modern software and hacking techniques. A synthetically amplified, PR-agency optimized sex scandal can destroy any target. Your dating experiences from the 70’s or 80’s will come back to haunt you decades later. Most dates involve drinking alcohol and taking drugs. If you were unattractive or had bad sexual skills your bad date will be called “date rape”, “drugging your date for sex” and related twisted narratives that are designed to shame you, the target.
—- If you try to get a date in the future, your potential date will be contacted by a third party who will slander and libel you to make sure your potential first date gets cancelled. Your social life will, essentially, end. Every photo on every dating site is cross checked with every other photo on the internet in order to cull your Facebook, Linkedin, Snapchat and other social media together to create a total psychological manipulation profile data file on you. A single photo on a dating site can be cross searched on every mugshot archive, photo album and corporate database in the worth within minutes using modern super-computers. Your sex life will be on public record in a flash.- Social Security, SSI, SDI, Disability and other earned benefits are stone-walled. Applications of targets are “lost”.
—- Files in the application process “disappeared”. Lois Lerner hard drive “incidents” are operated in order to seek to hide information and run cover-ups.
– Government officials and tech oligarchs contact members of the National Venture Capital association (NVCA) and created national “black-lists” to blockade target victims from ever receiving investor funding. This was also confirmed in a widely published disclosure by Tesla Motors Daryl Siry and in published testimony. If Silicon Valley political campaign finance oligarchs black-list you (see the “AngelGate” Scandal and the “High Tech No Poaching Class Action Lawsuit” cases) you will never get investor funding again.
– FOIA requests are hidden, frozen, stone-walled, delayed, lied about and only partially responded to in order to seek to hide information and run cover-ups.- State and federal employees will play an endless game of Catch-22 by arbitrarily determining that deadlines had passed that they, the government officials, had stonewalled and obfuscated applications for, in order to force these deadlines that they set, to appear to be missed. This can bankrupt a target victim.- Some Victims found themselves strangely poisoned, not unlike the Alexander Litvenko case.
—- Heavy metals and toxic materials were found right after their work with the Department of Energy weapons and energy facilities. Many wonder if these “targets” were intentionally exposed to toxins in retribution for their testimony. The federal MSDS documents clearly show that a number of these people were exposed to deadly compounds and radiations, via DOE, without being provided with proper HazMat suits which DOE officials knew were required.
– Victims employers are called, and faxed, and ordered to fire target victims from their places of employment, in the middle of the day, with no notice, as a retribution tactic. – On orders from Obama White House officials, DNC-financed Google, YouTube, Gawker Media and Gizmodo Media produce attack articles and defamation videos. Google locks this attack media on the internet on the top line, of the front page of all Google searches for a decade in front of 7.5 billion people, around the world.
—- This attack-type uses over $40 million dollars in server farms, production costs and internet rigging. The forensic data acquired from tracking some of these attacks proves that Google rigs attacks against individuals on the internet and that all of Google’s “impressions” are manually controlled by Google’s executives who are also the main financiers and policy directors of the Obama Administration. This data was provided to the European Union for it’s ongoing prosecution of Google’s political manipulation of public perceptions. – Victims HR and employment records, on recruiting and hiring databases, are embedded with negative keywords in order to prevent the victim targets from ever gaining future employment. – Gary D. Conley, Seth Rich, Rajeev Motwani and many other whistle-blowers in these matters, turned up dead under strange circumstances. It is very possible that some of these attack services, operated by former CIA operatives, even offer discrete murder-for-sale services using high-tech assassination tools that make murders look like heart attacks and brain failures.
—- Disability and VA complaint hearings and benefits are frozen, delayed, denied or subjected to lost records and “missing hard drives” as in the Lois Lerner case.- Paypal (A DNC-biased operation) and other on-line payments for on-line sales are de-platformed, delayed, hidden, or re-directed in order to terminate income potential for target victims who competed with the attackers interests and holdings.- DNS redirection, “website spoofing” sends target victims websites to dead ends where no sales orders or customer inquiries actually get back to the target. These internet revenue activity manipulations are conducted using Google and Amazon servers. All commercial storefronts and on-line sales attempts by target victims, will have had their sites hidden, or search engine de-linked by a massively resourced facility located in Virginia, Texas or Palo Alto, California in order to terminate revenue potentials for the target victims.
—- Over 50,000 trolls, shills, botnets and synth-blog deployments are deployed to place defamatory statements and disinformation about victims in front of 7.5 billion people around the world on the internet in order to seek to damage their federal testimony credibility by a massively resourced facility.
– Campaign finance dirty tricks contractors are hired by campaign financiers to attack the friends and family members of the target victim in order to create low morale for the target victims psyche and motivation.- Are you getting weird headaches and hearing a “buzzing sound” in your head? The U.S. Government has now acknowledged that the Cuban, Chinese and other embassy “sonic attacks” are from a known microwave beam weapon. Any one of the technical departments of the attack services listed at the top of this article can build such a biological harassment weapon.
—- It can be aimed at the target victims office, bedroom or vehicle and, within a week, have caused biological and emotional damage using a weapon that has no visible track of trajectory. It is designed to make the target victim think they are “going crazy” or “hearing sounds in their head”.
—- In one case covert political partner: Google, transferred large sums of cash to dirty tricks contractors and then manually locked the media portion of the attacks into the top lines of the top pages of all Google searches globally, for years, with hidden embedded codes in the links and web-pages which multiplied the attacks on Victims by many magnitudes.- Covert Cartel financier: Google, placed Google’s lawyer: Michelle Lee, in charge of the U.S. Patent Office and she, in turn, stacked all of the U.S. Patent Office IPR and ALICE review boards and offices with Google-supporting employees in order to rig the U.S. Patent Office to protect Google from being prosecuted for the vast patent thefts that Google engages in.
—- Google has hundreds of patent lawsuits for technology theft and a number of those lawsuits refer to Google’s operations as “Racketeering”, “Monopolistic Cartel” and “Government Coup-like” behaviors. Thousands of articles and investigations detail the fact that Google, “essentially” ran the Obama White House and provided over 80% of the key White House staff. A conflict-of-interest unlike any in American history. Google’s investors personally told Applicant they would “kill him”. Google and the Obama Administration were “the same entity”. Applicant testified in the review that got Michelle Lee terminated and uncovered a tactical political and social warfare group inside Google who were financed by Federal and State funds.
—- Honeytraps and moles were employed by the attackers. In this tactic, people who covertly worked for the attackers were employed to approach the “target” in order to spy on and misdirect the subject. – Gawker Media, Gizmodo Media, Snopes, SPLC and other hired media assassins will be retained to produce “hatchet job” character assassination articles about you. Then those articles will be faxed, mailed and emailed to your employer and investors with a note saying: “You don’t want to have anything to do with this person, do you..?” in order to get you fired from your job and get your loans or financing pulled. The attackers will use their round one attack media, that they authored, to create a round two second wave attack designed to end your life via economic warfare.
—- Mortgage and rental applications will have had red flags added to them in databases to prevent the targets from getting homes or apartments.- Krebs On Security, Wired, Ars Technica, The Wall Street Journal and most major IT publications have reported that hundreds of spy “back-doors” have been found on every Intel, AMD, Apple, Xfinity, Cisco, Microsoft, Juniper Networks motherboard, chip-set and hardware component set.
—- This means that any kid with the “key” code can open any computer, server, router, cloud-network or other network connected device and read every file, photo, video, your calendar and email on your devices at any time from any location on Earth. The key codes have been released to every hacker community in the world for over ten years. There is now no government, corporate or personal data that can’t be hacked, even data from decades ago.
Every single one of your darkest secrets can be in the hands of your enemy within 60 minutes, or less. Important meetings you had planned with potential investors, employers, clients, dates, suppliers and others will suddenly get cancelled at the last minute. They will get cancelled because your enemies are reading your calendar remotely and covertly sending slander information to those you had hoped to engage with in order to sabotage your life.
—- Nothing you have ever typed on a computer or Smartphone is safe. it WILL be acquired and it WILL be used against you.
– McCarthy-Era “Black-lists” are created and employed against target victims who competed with Obama Administration executives and their campaign financiers to prevent them from getting funding and future employment.
– Obama Administration targets were very carefully placed in a position of not being able to get jobs, unemployment benefits, disability benefits or acquire any possible sources of income. The retribution tactics were audacious, overt..and quite illegal.
– There are thousands of additional Dirty Tricks tactics being used by these Attack Services yet Congress refuses to pass laws out-lawing such attack services.
—- The cost of an attack on a person ranges from $150,000.00 to over $50,000,000.00. While a Silicon Valley billionaire can afford to launch counter-measures to these attacks, any regular taxpayer will be utterly destroyed, and incapable of fighting back, against even the smallest version of one of these “kill orders”.
—- A number of modern office shootings are the results of these attacks against an individual who has lost everything because of the attack and has no options left. – Federal law enforcement, the United States Congress and the highest level investigators in the U.S., and abroad, have documented (per the “FISA Memo”, Congressional Reports and federal employee testimony) and proven the fact that the Obama Administration regularly engaged in the operation of retribution, vendetta and reprisal campaigns known as “hit-jobs” against domestic natural born U.S. citizen domestic taxpayers.
—- The Federal Court, in at least one previous court case, has ruled that Applicants, in this particular matter, were the victims and target of a number of these attacks designed to inflict permanent medical, emotional, character assassination, brand negation, economic and career damage. The FBI has been asked to interview John Cook, Nicholas Guido Denton, Adrian Covert, Patrick George, Ian Fette and John Hermann of Gawker/Gizmodo re: their financing, payola and hit-job attacks on third parties.
Who Is Jared Birchall? Elon Musk’s Straightlaced Money Manager
Jul 4, 2022 … Meet Jared Birchall, the secretive man that Elon Musk trusts with his billions · Elon Musk’s right-hand man is the most straightlaced man you’ll …
Meet Elon Musk’s secretive right-hand man Jared Birchall – Yahoo
Jun 2, 2022 … Birchall is not only the director of Musk’s family office Excession LLC – which is responsible for a range of wealth and investment-management …
Who Is Jared Birchall? Meet Elon Musk’s Fixer and Right-Hand Man
May 6, 2022 … Handle the fortune and whimsies of the world’s richest person? It’s no small task. Meet Jared Birchall, who for the past six years has …
Meet the man Elon Musk turns to for solving his problems
Aug 6, 2022 … Meet the man Elon Musk turns to for solving his problems – Jared Birchall is the Tesla CEO’s ‘fixer’ and also the architect of the Twitter deal.
Everything You Need to Know About Jared Birchall – TechStory
May 9, 2022 … Jared Birchall, 47, is the right-hand man of the world’s wealthiest man. Musk’s family office, Excession LLC, is overseen by a former …
Meet Jared Birchall, the right-hand man of world’s richest person …
Aug 9, 2022 … Jared Birchall is reported to be one of the best handlers, citing people with whom he has collaborated over the years. As Musk’s wealth manager, …






